Strangler Fig Pattern
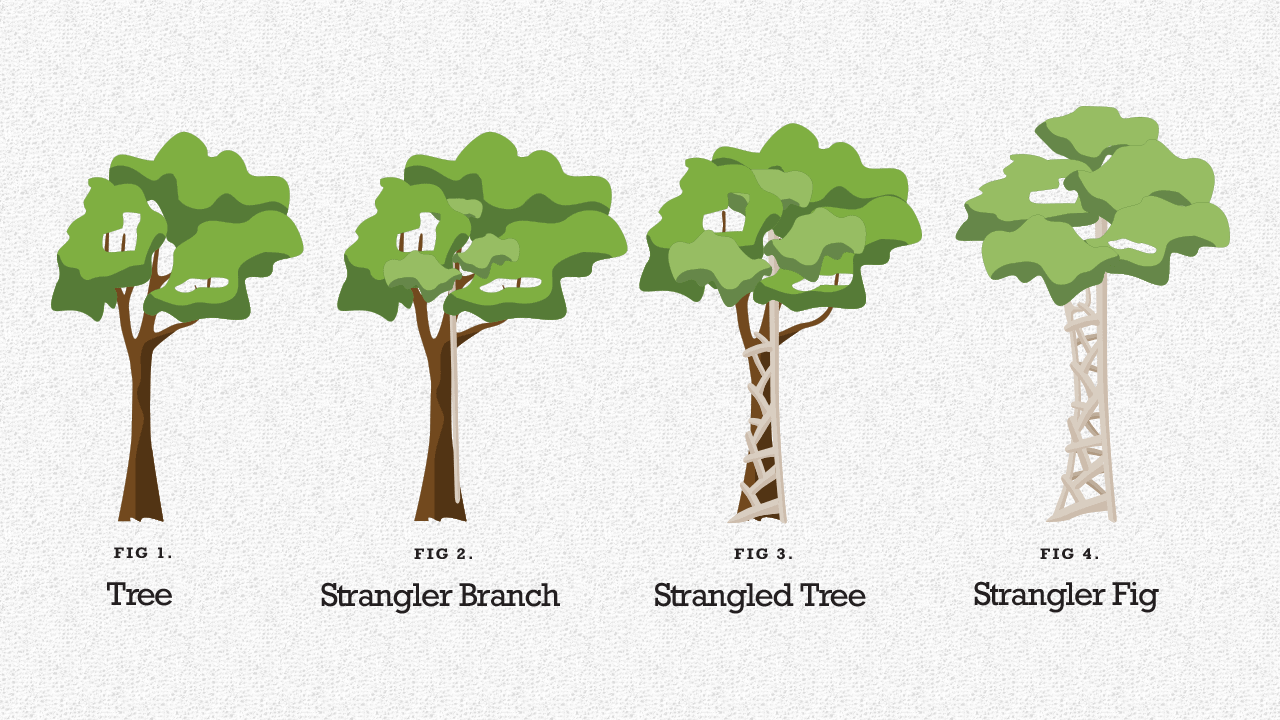
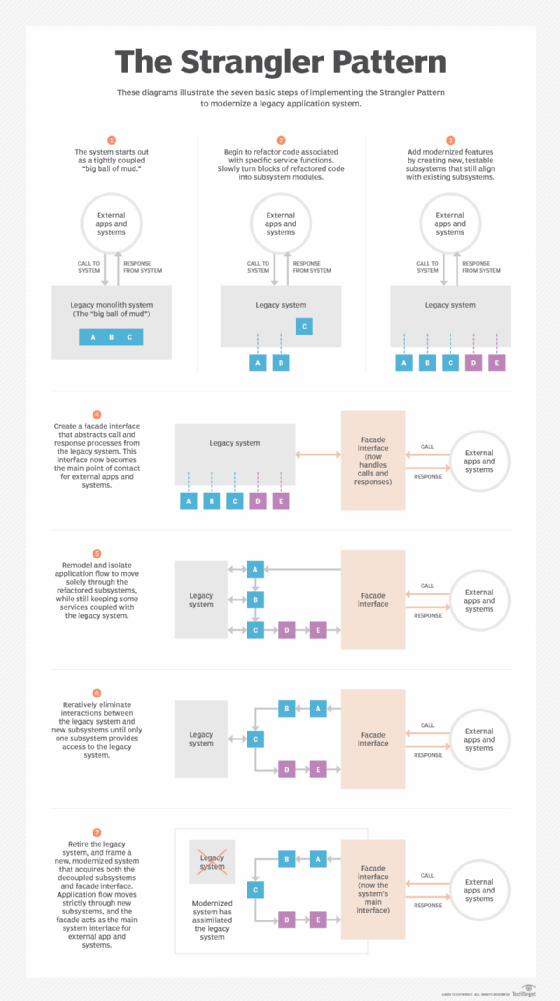
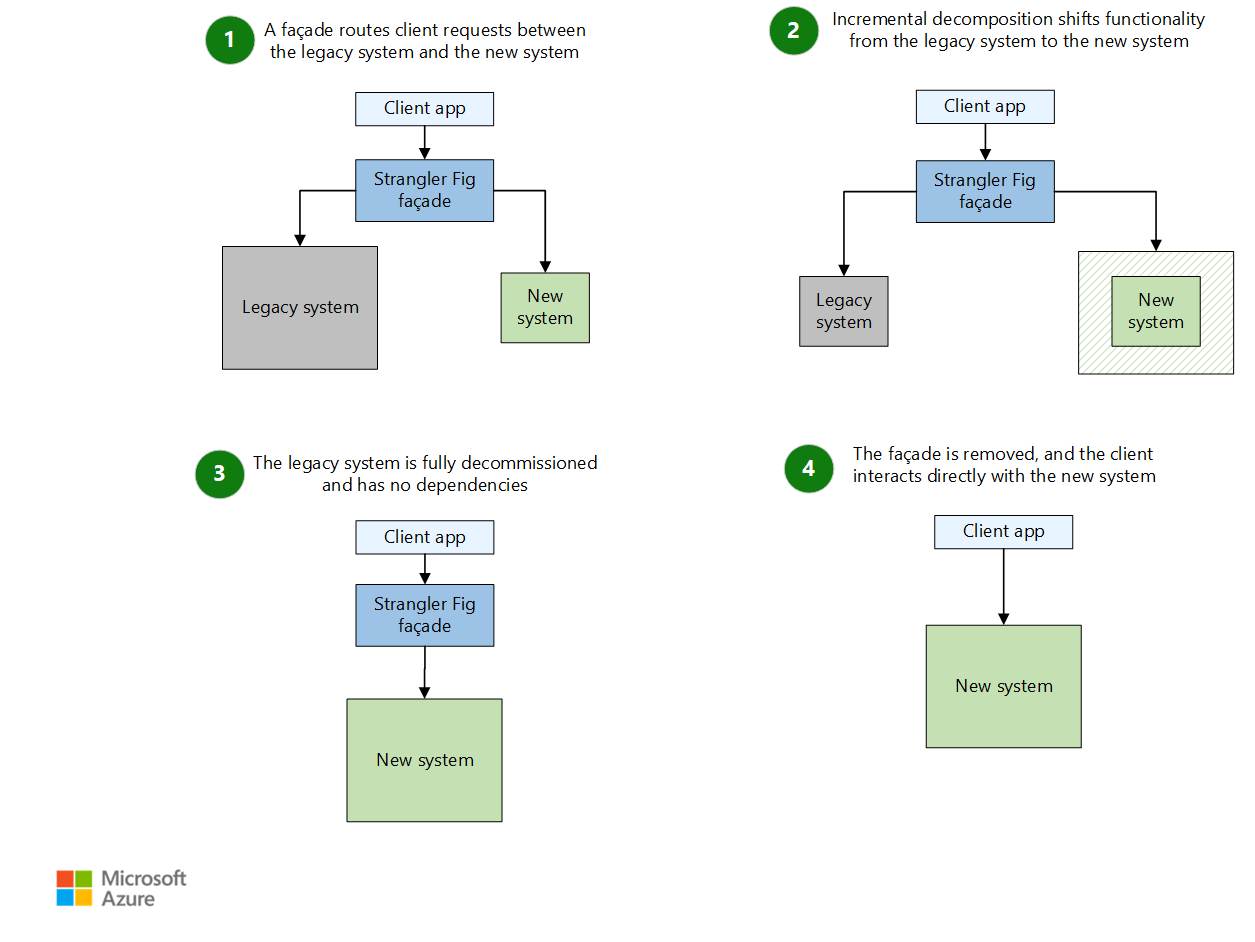
Strangler Fig Pattern - The term was coined in 2004 by martin fowler. Transform —create a parallel new site (for example, in ibm cloud or even in your existing environment) but based on more modern approaches. Web strangler fig pattern: Web in this tutorial, we’ll explore a typical pattern that can be used when migrating a monolithic system to microservices. This pattern's incremental approach can help mitigate risks during a component transition vs large systemic changes. Web what is the strangler fig pattern? Web how this pattern supports pillar goals; There is also a good representation of it among microsoft's cloud design patterns. A slow migration, one endpoint by one endpoint, not a bigbang. But its usage often gets separated from its metaphorical root, and takes on a unpleasantly violent connotation. Modernize an application by incrementally developing a new (strangler) application around the legacy application. Web thus, the strangler fig application pattern steps are transform, coexist, and eliminate: This pattern's incremental approach can help mitigate risks during a component transition vs large systemic changes. Web how this pattern supports pillar goals; He noticed that the seeds of the strangler fig tree. The strangler pattern allows software teams to retire legacy systems incrementally and avoid the pitfalls of major rewrites. Web the process to transition from a monolithic application to microservices by implementing the strangler fig pattern consists of three steps: Web what is the strangler pattern and how does it work? The pattern is an analogy for a type of plant. Four best practices to prepare for the strangler fig pattern; The term was coined in 2004 by martin fowler. But what, exactly, is the strangler fig pattern? Web thus, the strangler fig application pattern steps are transform, coexist, and eliminate: Web strangler fig, any of numerous species of tropical figs (genus ficus, family moraceae) named for their pattern of growth. Web if you are wondering where the term “strangler fig” comes from, it’s from the plant species that have a “strangling” growth habit, that suck up its nutrients from its victims, causing them to eventually die. It describes a method whereby a new system slowly grows over top of an old system until the old system is “strangled” and can. Web the strangler fig pattern helps migrate a monolithic application to a microservices architecture incrementally, with reduced transformation risk and business disruption. The new system wraps around the existing system, intercepting calls to old functionality, and redirecting those calls to the new system as that functionality is ported. Web if you are wondering where the term “strangler fig” comes from,. Web the strangler fig pattern allows for the incremental migration of functionality from one system to another. Web the strangler fig pattern offers several advantages when it comes to replacing legacy systems, especially those that are large, complex and critical to ongoing operations: The strangler fig pattern allows for the gradual replacement of the old system, reducing risk and making. The pattern is an analogy for a type of plant that begins life as a vine growing alongside an older, established tree. Web the process to transition from a monolithic application to microservices by implementing the strangler fig pattern consists of three steps: Web what is the strangler fig pattern? Web the strangler fig pattern allows for the incremental migration. The strangler fig pattern allows for the gradual replacement of the old system, reducing risk and making the process more manageable. The new system wraps around the existing system, intercepting calls to old functionality, and redirecting those calls to the new system as that functionality is ported. Web if you are wondering where the term “strangler fig” comes from, it’s. Web in this tutorial, we’ll explore a typical pattern that can be used when migrating a monolithic system to microservices. Web the strangler fig pattern helps migrate a monolithic application to a microservices architecture incrementally, with reduced transformation risk and business disruption. He noticed that the seeds of the strangler fig tree germinate in the upper branches of. We want. Implement the strangler fig pattern with vfunction and aws refactor spaces The term was coined in 2004 by martin fowler. Web the strangler fig pattern offers several advantages when it comes to replacing legacy systems, especially those that are large, complex and critical to ongoing operations: Web what is the strangler pattern and how does it work? Web the original. Web what is the strangler fig pattern? The new system wraps around the existing system, intercepting calls to old functionality, and redirecting those calls to the new system as that functionality is ported. Web the strangler fig pattern allows for the incremental migration of functionality from one system to another. A slow migration, one endpoint by one endpoint, not a bigbang. It describes a method whereby a new system slowly grows over top of an old system until the old system is “strangled” and can simply be removed. Web if you are wondering where the term “strangler fig” comes from, it’s from the plant species that have a “strangling” growth habit, that suck up its nutrients from its victims, causing them to eventually die. Web the strangler fig pattern offers several advantages when it comes to replacing legacy systems, especially those that are large, complex and critical to ongoing operations: Web the process to transition from a monolithic application to microservices by implementing the strangler fig pattern consists of three steps: If i rename the post to “strangler fig application”, and use the term “strangler fig” as. Web strangler fig pattern: Modernize an application by incrementally developing a new (strangler) application around the legacy application. Web the strangler fig pattern was introduced by martin fowler as a way to manage risk when modernizing or rewriting large, monolithic systems. Web in this final installment of our three part series, we delve into overcoming technology challenges when applying the strangler fig pattern. But its usage often gets separated from its metaphorical root, and takes on a unpleasantly violent connotation. Confluent cloud is a fully managed apache kafka. The term was coined in 2004 by martin fowler.
How to Use the Strangler Fig Pattern in Serverless Stack by Julien
Modernize with the Strangler Application Pattern and Microservices CM
What is the strangler pattern and how does it work? TechTarget

The Strangler Fig Migration Pattern by Diana Darie Medium

A tree with a strangler fig growing on the surface creates an amazing

What is the Strangler Fig Pattern and How it Helps Manage Legacy Code

The Strangler Pattern and Legacy Migration Strategies Atelier Solutions
Conquering Legacy Code Embrace the Strangler Fig Pattern for Seamless

What is the Strangler Fig Pattern and How it Helps Manage Legacy Code

Strangler fig pattern AWS Prescriptive Guidance
The Strangler Pattern Allows Software Teams To Retire Legacy Systems Incrementally And Avoid The Pitfalls Of Major Rewrites.
Strangler Figs And Other Strangler Species Are Common In.
We Want To Gradually Deprecate The Old System.
Deals Of The Dayfast Shippingshop Best Sellersread Ratings & Reviews
Related Post: