Security Patterns
Security Patterns - Not paying attention to authentication activities and patterns. All of the classical design patterns have different instantiations to fulfill some information security goal: Botnets often camouflage their activity by utilizing common internet. These solutions encapsulate expert knowledge and best practices for developing secure software at different stages of the development lifecycle. Web the global center for health security is the premier u.s. We describe here the properties of asps and present a detailed example. 1.5 other approaches to building secure systems. Web gifted content creator and singer, david ezebri, professionally known as davidconnect, is thrilled to announce the release of his highly anticipated debut ep titled different patterns. We describe here the properties of asps and present a detailed example. Web software security patterns are structured solutions to reoccurring security problems [ 1, 2 ]. 2.1 what is a security pattern? Botnets often camouflage their activity by utilizing common internet. Web security patterns can be applied to achieve goals in the area of security. A different cow tissues may help to explain the pattern of illness being seen in the outbreak of h5n1 bird flu in u.s. No single component can address all security problems: Web an abstract security pattern describes a conceptual security mechanism that includes functions able to stop or mitigate a threat or comply with a regulation or institutional policy. A different cow tissues may help to explain the pattern of illness being seen in the outbreak of h5n1 bird flu in u.s. A website dedicated to helping security professionals build better. Learn to combine security theory and code to produce secure systemssecurity is clearly a crucial issue to consider during the design and implementation of any distributed software architecture. Our objective is to explore the research efforts on security patterns and discuss the current state of the art. Further, our clinical capabilities include biological, chemical, burn, and radiation domains. We describe. Designing secure architectures using software patterns. These solutions encapsulate expert knowledge and best practices for developing secure software at different stages of the development lifecycle. Web a botnet is a network of compromised computer systems, or bots, remotely controlled by an attacker through bot controllers. Learn to combine security theory and code to produce secure systemssecurity is clearly a crucial. Web when considering advanced authentication factors, prioritize solutions that minimize steps and reduce friction. So what makes up a security pattern? By christoph koettl the new york times, source: There are many security challenges need to be addressed in the application design and implementation phases. Web this guide will step you through the process for constructing security patterns, provide a. We describe here the properties of asps and present a detailed example. This guide describes how to use and apply security patterns. If you have already read through the previous guide you may be now wondering; These solutions encapsulate expert knowledge and best practices for developing secure software at different stages of the development lifecycle. Osa it security architecture patterns. To help you focus on only your code, the debugger will now skip scripts from /node_modules/ and /bower_components/ by default. Web the global center for health security is the premier u.s. Use paseto tokens over jwt. Web a botnet is a network of compromised computer systems, or bots, remotely controlled by an attacker through bot controllers. All of the classical. We describe here the properties of asps and present a detailed example. It follows on from the previous guide for how to write a security pattern. Ronald wassermann and betty h.c. Osa it security architecture patterns are based on architectural overview diagrams depicting a certain information usage context. A different cow tissues may help to explain the pattern of illness. Web when considering advanced authentication factors, prioritize solutions that minimize steps and reduce friction. This guide describes how to use and apply security patterns. Not paying attention to authentication activities and patterns. Patterns ensure the security controls identified are based on threat modelling associated to protecting the assets. These solutions encapsulate expert knowledge and best practices for developing secure software. There are many security challenges need to be addressed in the application design and implementation phases. 1.4 industrial use of security patterns. Patterns ensure the security controls identified are based on threat modelling associated to protecting the assets. Web security patterns can be applied to achieve goals in the area of security. If you have already read through the previous. By christoph koettl the new york times, source: 2.1 what is a security pattern? There are many security challenges need to be addressed in the application design and implementation phases. Use paseto tokens over jwt. Not paying attention to authentication activities and patterns. Web an abstract security pattern describes a conceptual security mechanism that includes functions able to stop or mitigate a threat or comply with a regulation or institutional policy. Web software security patterns are structured solutions to reoccurring security problems [1,2]. All of the classical design patterns have different instantiations to fulfill some information security goal: This version enables the default regular expression as a custom exclusion rule in settings > ignore list. By harnessing the immense processing power of ai, cybersecurity professionals can augment their security stacks, proactively identifying. Standard of good practice, security principles, and. Botnets often camouflage their activity by utilizing common internet. Web default exclusion pattern for node_modules. Security is a blend of hw, sw, and procedures designed and combined to ensure the highest level and resist future threats that are still unknown. Patterns ensure the security controls identified are based on threat modelling associated to protecting the assets. If you have already read through the previous guide you may be now wondering;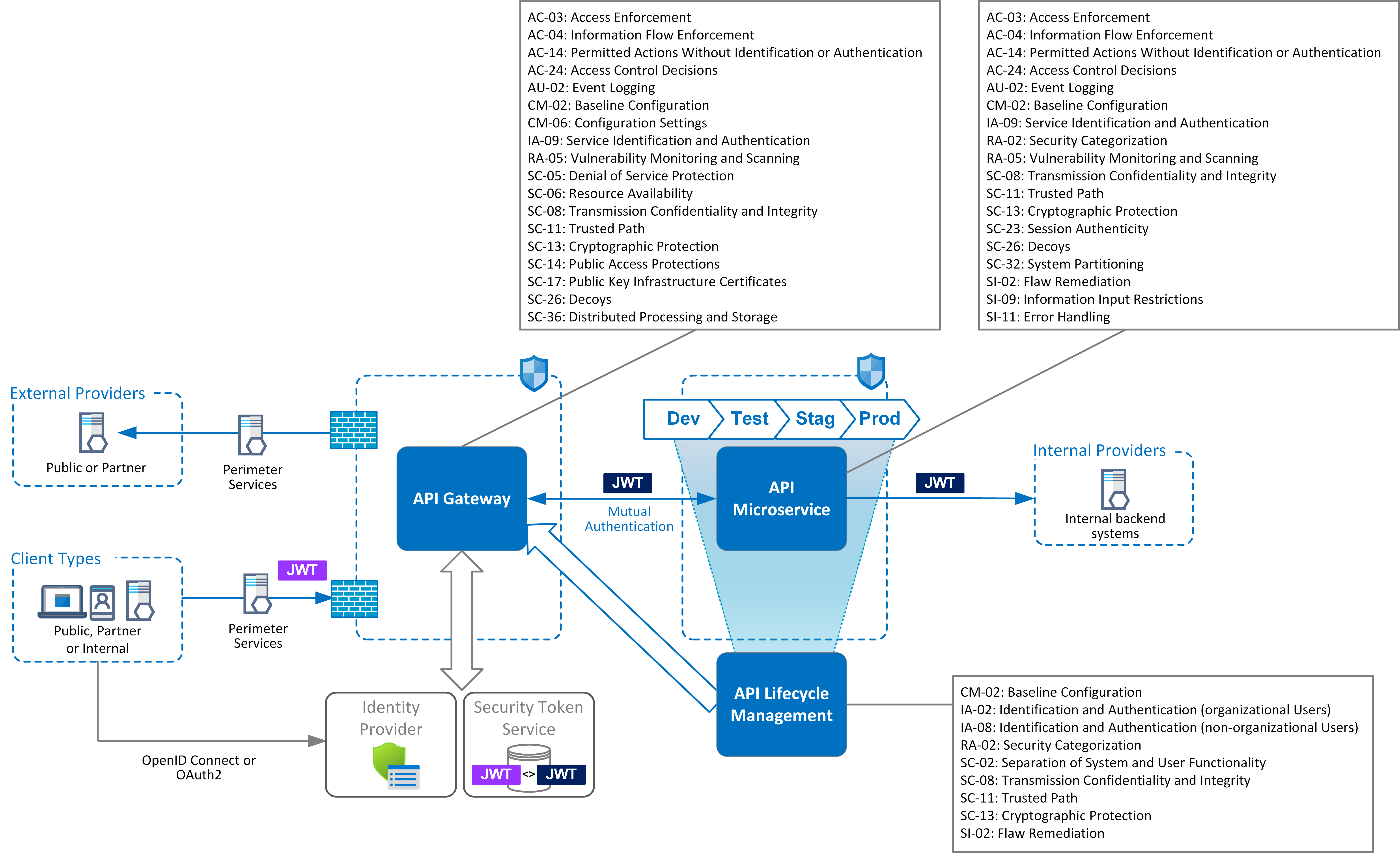
How to Write A Security Pattern API based Microservices
Security patterns vector free vector download (19,040 Free vector) for
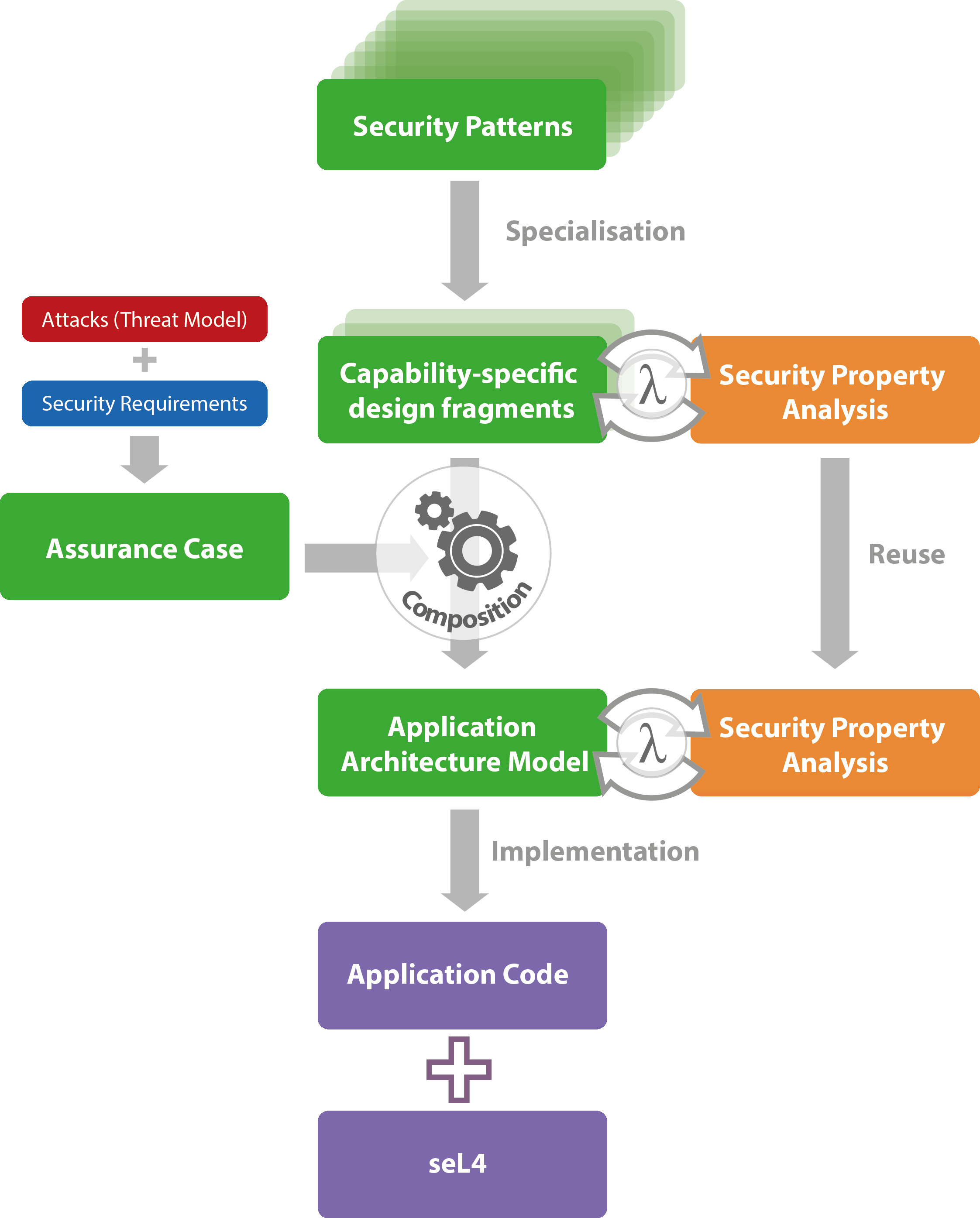
Secure Design using Security Patterns TS
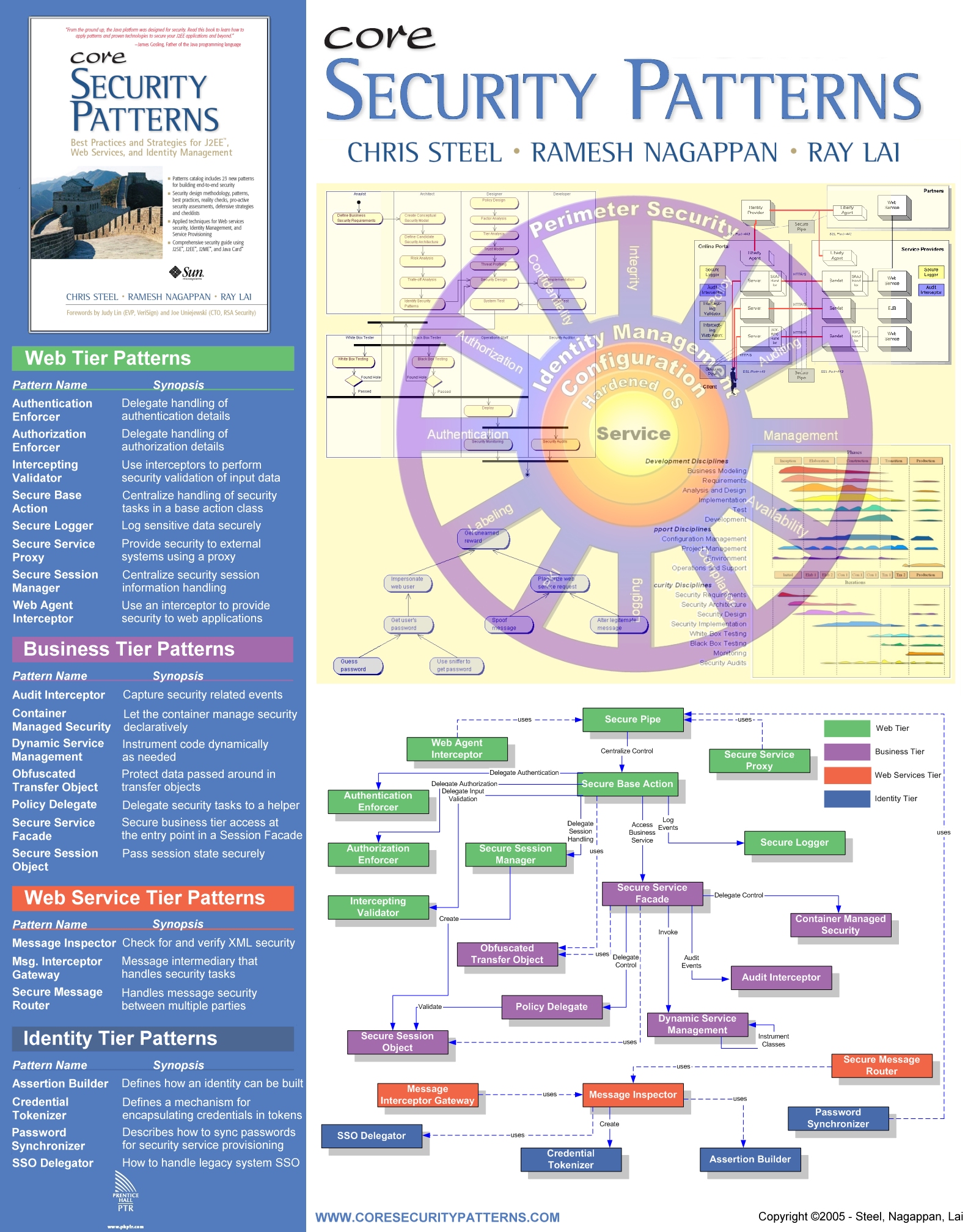
Core Security Patterns Ramesh Nagappan CISSP, Chris Steel CISSP
Security pattern 01 vector Free Vector / 4Vector

Security pattern (23738) Free EPS Download / 4 Vector
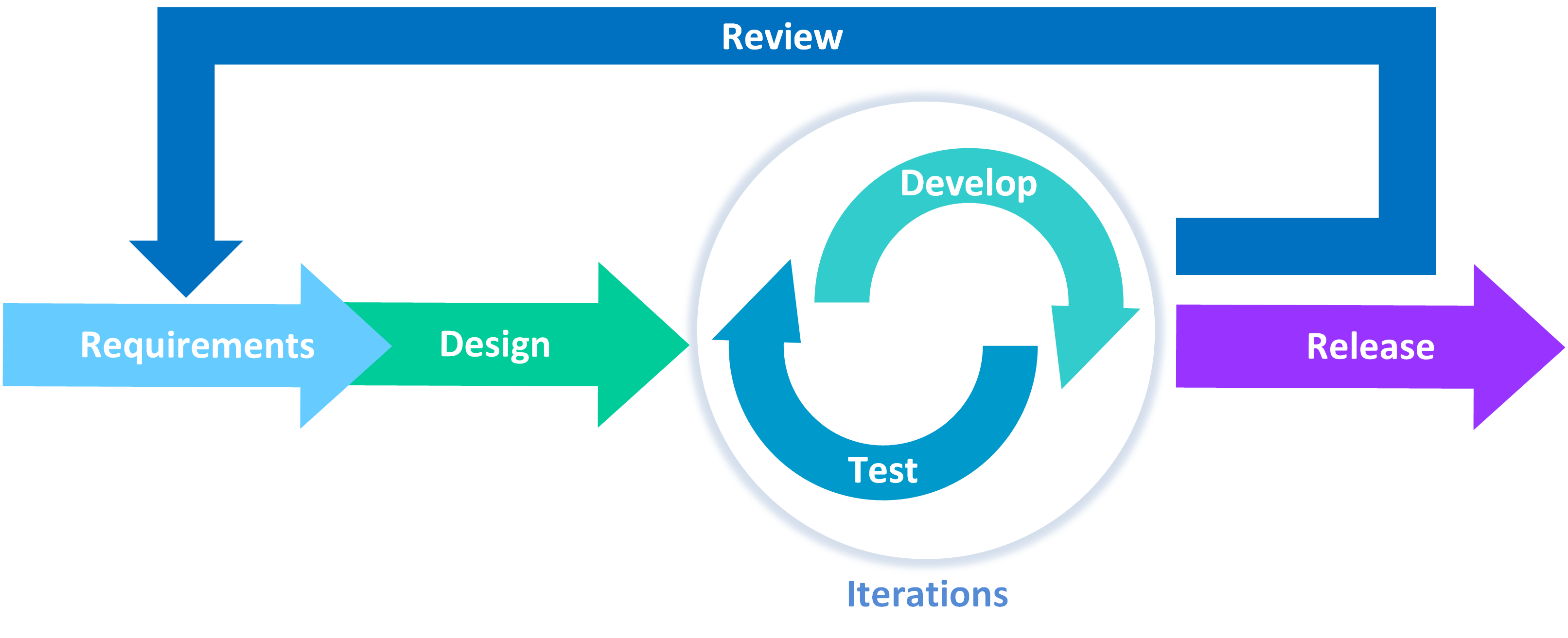
How to Write A Security Pattern Writing Patterns

A variety of security pattern shading vector free download
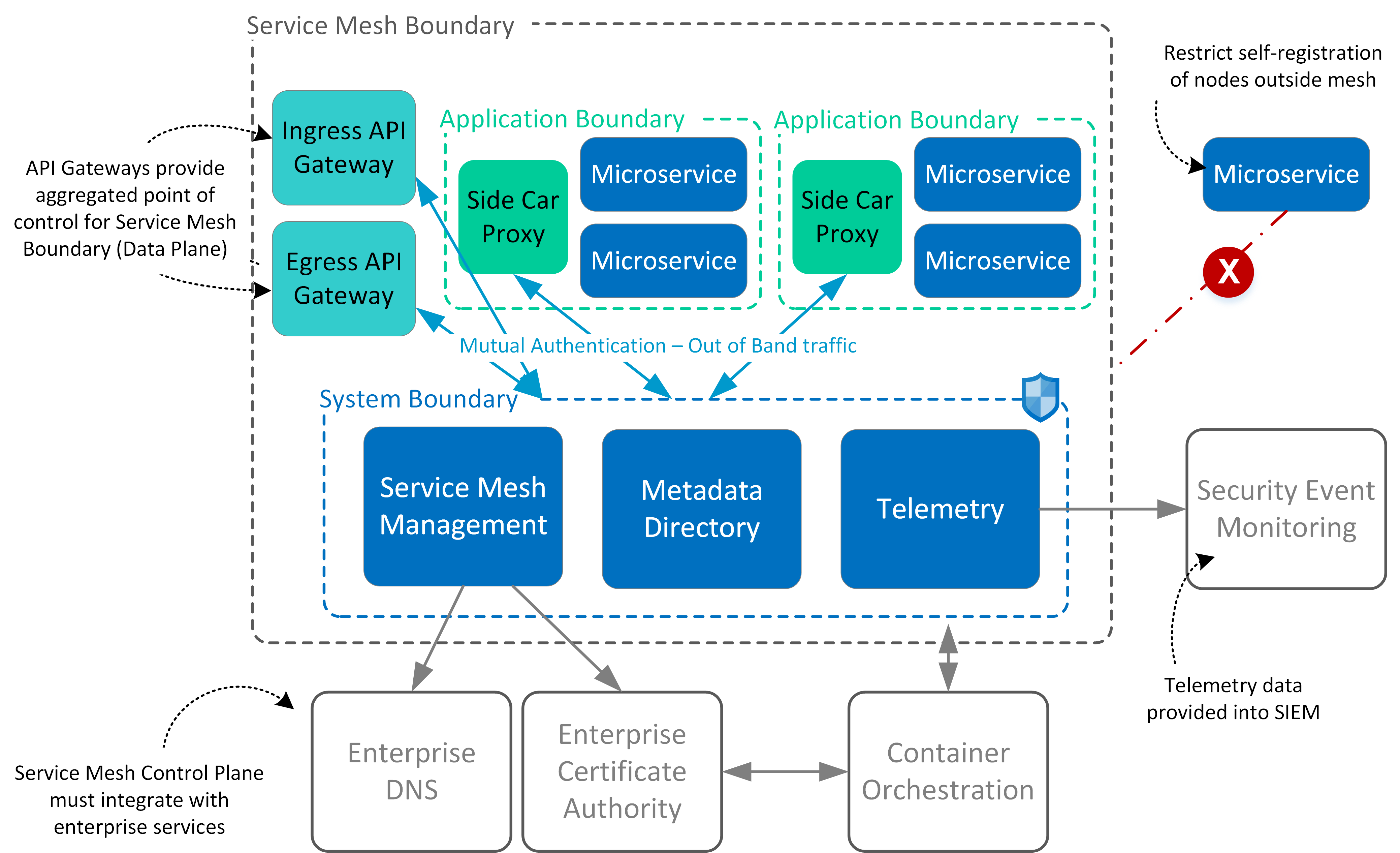
How to Write A Security Pattern Service Mesh

Security Patterns How To Make Security Arch Easy To Consume
Without Regular Review Or Insights Into User Behaviors.
So What Makes Up A Security Pattern?
Web Available Patterns (Nist Sp 800:53 Framework) Security Pattern:
Software Engineering And Network Systems Laboratory Department Of Computer Science And Engineering Michigan State University East Lansing, Michigan 48824, Usa Email:{Wasser17,Chengb}@Cse.msu.edu.
Related Post: