Vulnerability Remediation Plan Template
Vulnerability Remediation Plan Template - Classify the vulnerabilities and assess the risk; Yet, as indicated by the wave of massive data breaches and ransomware attacks, all too often organizations are compromised over missing patches and misconfigurations. Block, patch, remove components, or. Web the remediation plan should include: Analyze system and network scan results. Establish a list of assets that need protection. Effective remediation entails continuous processes that together are called vulnerability management. Identify vulnerabilities through testing and scanning; The purpose of the (company) vulnerability management policy is to establish the rules for the review, evaluation, application, and verification of system updates to mitigate vulnerabilities in the it environment and the risks associated with. Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. Top 10 assets by vulnerabilities. Top policy remediations with details. This chapter provides a top 20 summary of vulnerabilities discovered through active scanning by severity level. Web what is vulnerability remediation? Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. Web owasp vulnerability management guide. Web updated conmon report template and other outdated information. This chapter provides a top 20 summary of vulnerabilities discovered through passive scanning by severity level. The purpose of the (company) vulnerability management policy is to establish the rules for the review, evaluation, application, and verification of system updates to mitigate vulnerabilities in the it environment. Define the criticality of each asset. Top 10 assets by vulnerabilities. Establish a list of assets that need protection. Interim mitigation actions to overcome constraints. The steps include the following: The policy statements included within this document can be used by all cis implementation groups (igs), but are specifically geared towards safeguards in implementation group 1 (ig1). Web this policy template is meant to supplement the cis controls v8. Effective remediation entails continuous processes that together are called vulnerability management. Fedramp pmo 1/31/2018 3.0 all updated to newest template. Web. Create a vulnerability assessment action plan template that focuses on remediation. Identify vulnerabilities through testing and scanning; Best choice for pen testers and other contractors. Web this policy template is meant to supplement the cis controls v8. The plan is focused on providing the proper steps and resources to ensure the security and safety of data and systems. Interim mitigation actions to overcome constraints. Enhance your cybersecurity with our vulnerability management template, a comprehensive guide for identifying, prioritizing, resolving, and documenting vulnerabilities. A security remediation plan is a set of processes and procedures that are created to identify, address, and prevent security vulnerabilities. With cascade, you can quickly and efficiently reduce the risk of security threats. Utilize centralized. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy template for. The plan is focused on providing the proper steps and resources to ensure the security and safety of data and systems. Best overall vulnerability management solution. The steps include the following: This chapter provides a top 20 summary of vulnerabilities discovered. Interim mitigation actions to overcome constraints. Web updated conmon report template and other outdated information. Final actions required to remediate vulnerability. Web the remediation plan should include: Fedramp pmo 1/31/2018 3.0 all updated to newest template. Perform system and network scanning. Web z )> zd^ &. The plan is focused on providing the proper steps and resources to ensure the security and safety of data and systems. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy template for. Identify and document the scope of the assessment. Enhance your cybersecurity with our vulnerability management template, a comprehensive guide for identifying, prioritizing, resolving, and documenting vulnerabilities. The steps include the following: The policy statements included within this document can be used by all cis implementation groups (igs), but are specifically geared towards safeguards in implementation group 1 (ig1). Web • developing a vulnerability analysis and resolution strategy •. Fedramp pmo 1/31/2018 3.0 all updated to newest template. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy template for. The steps include the following: Remediation of network vulnerabilities is something every organization wants done before hackers exploit the weaknesses. Web download our free vulnerability management policy template now. Identify vulnerabilities through testing and scanning; This chapter provides a top 20 summary of vulnerabilities discovered through passive scanning by severity level. Web the vulnerability remediation process is a workflow that fixes or neutralizes detected weaknesses including bugs and vulnerabilities. Top policy remediations with details. Web an effective vulnerability assessment and remediation program must be able to prevent the exploitation of vulnerabilities by detecting and remediating vulnerabilities in covered devices in a timely fashion. Perform system and network scanning. The purpose of the (company) vulnerability management policy is to establish the rules for the review, evaluation, application, and verification of system updates to mitigate vulnerabilities in the it environment and the risks associated with. This chapter provides a top 20 summary of vulnerabilities discovered through active scanning by severity level. Web active vulnerability remediation plan: A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. Web z )> zd^ &.
Remediation Plans Templates Word Format, Free, Download

Vulnerability Sample Report Security Assessment, Report With Patch
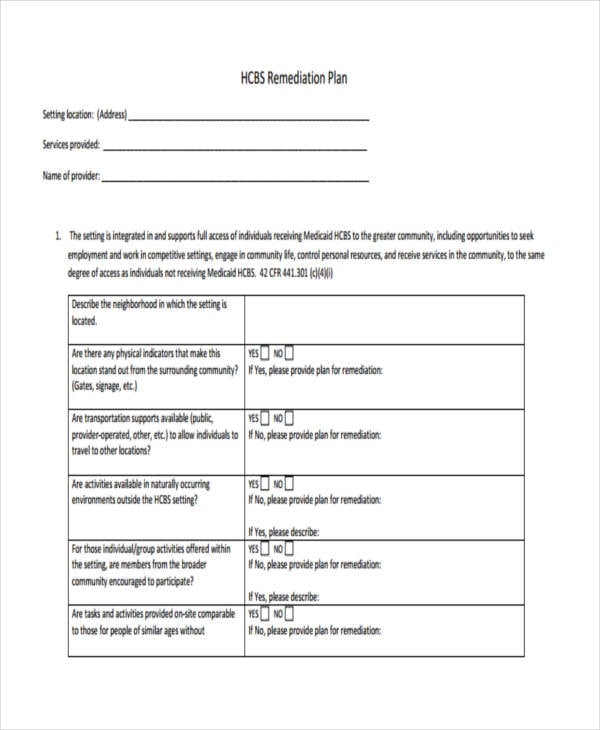
18+ Remediation Plan Templates Free Sample, Example Format Download
ICVulnerabilityRemediationPlanTemplate_Google.xltx Google Sheets
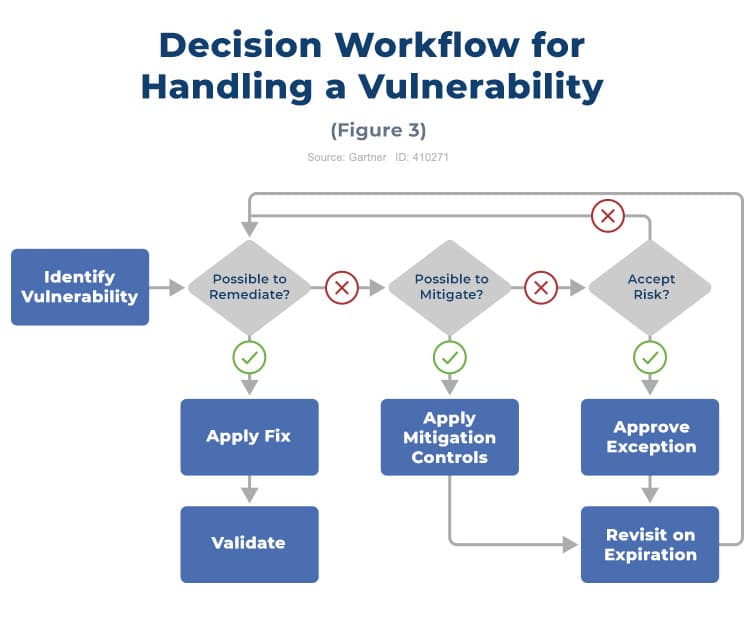
Vulnerability Management Process Flow Chart Rootshell
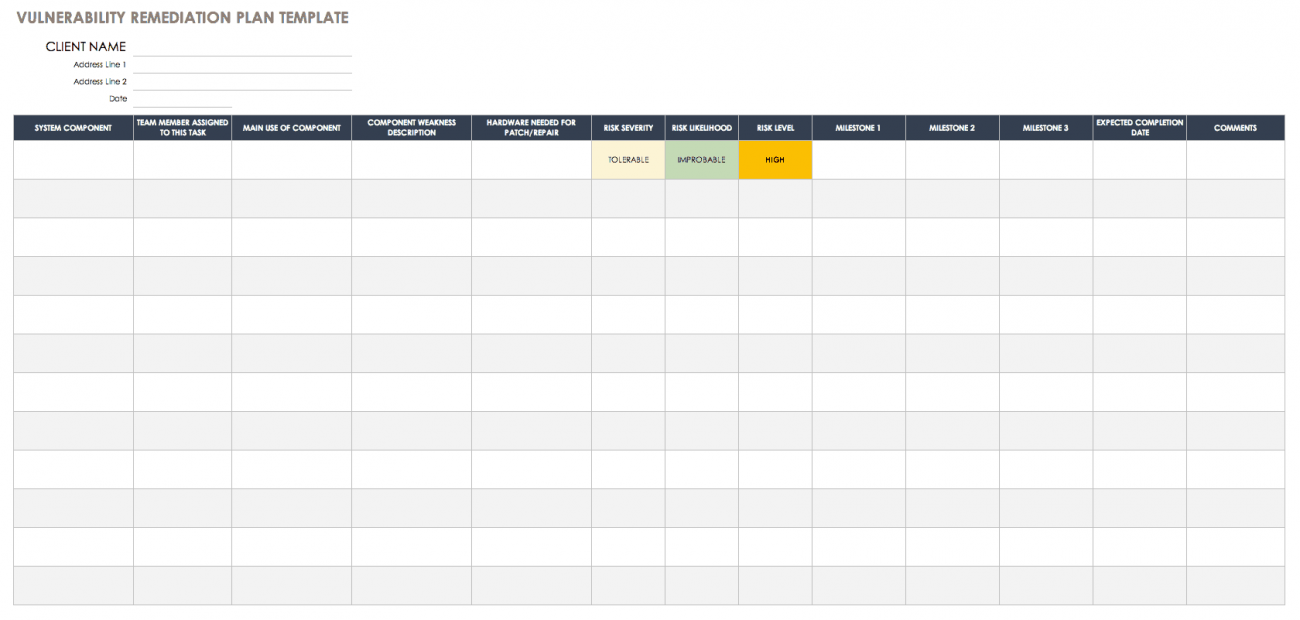
Free Vulnerability Assessment Templates Smartsheet
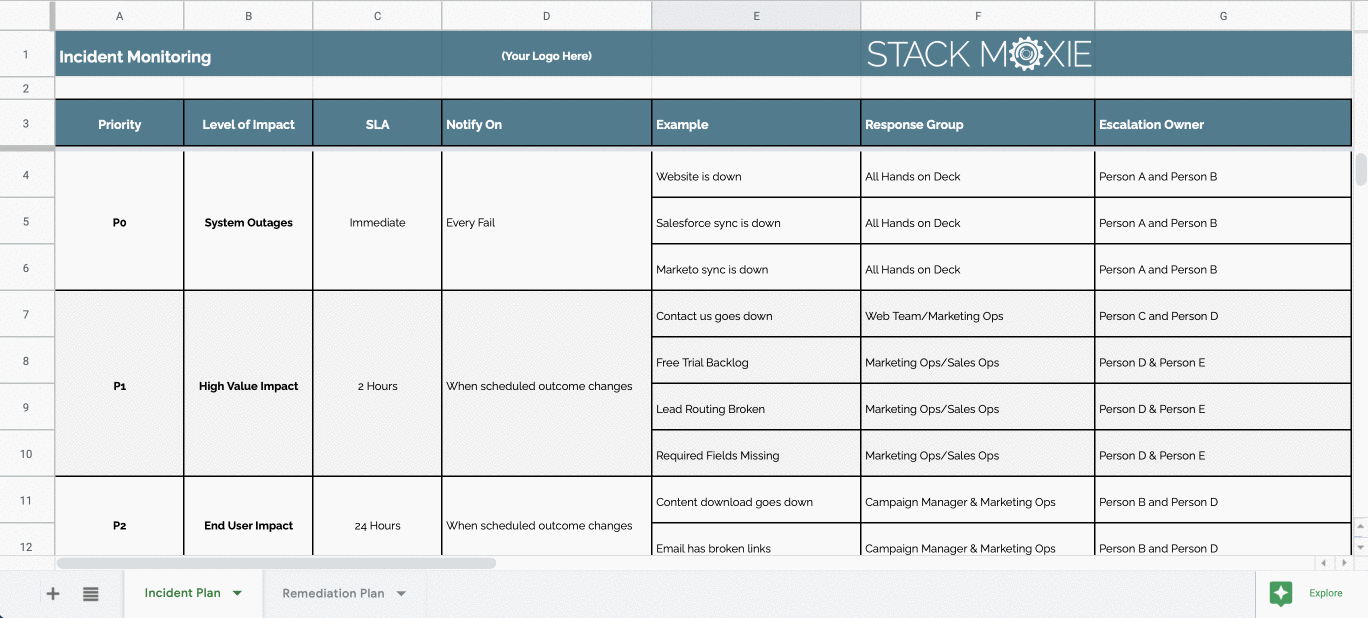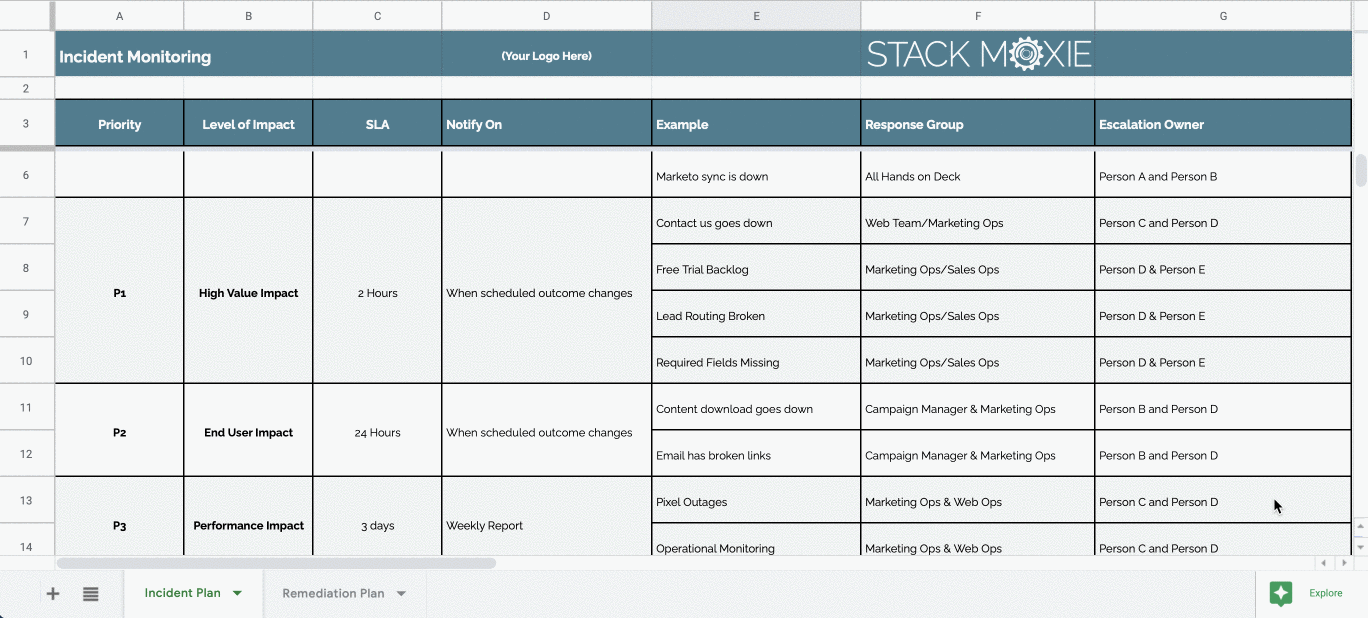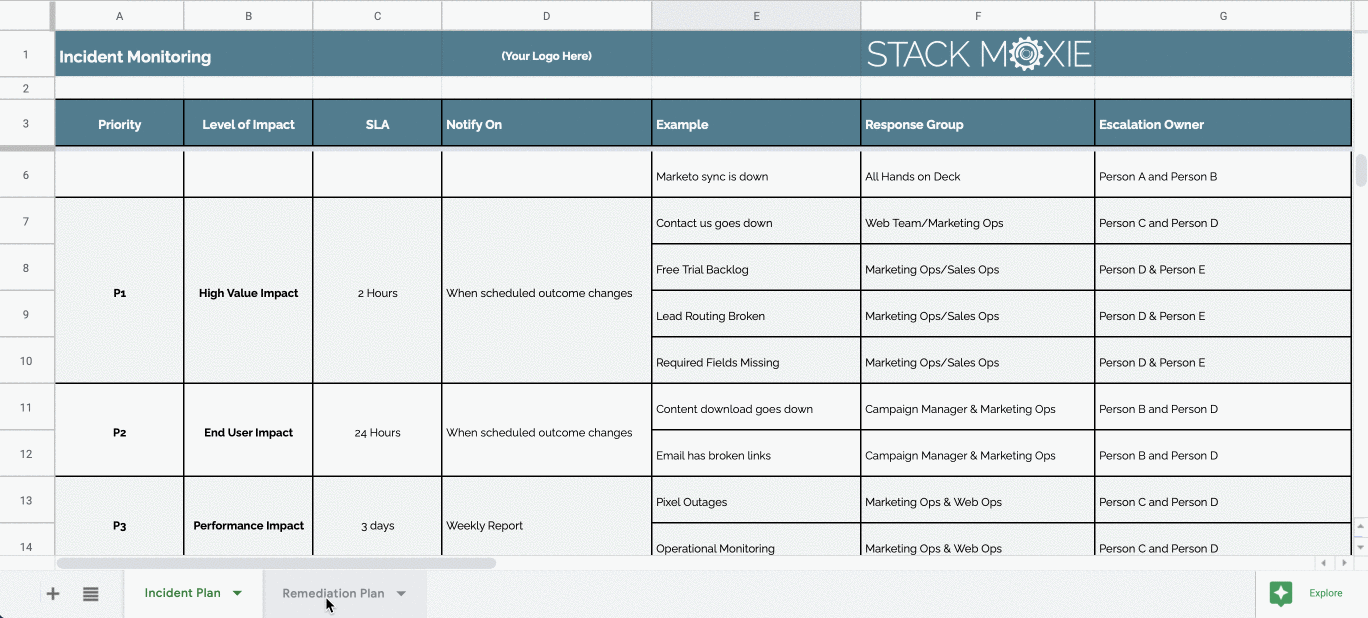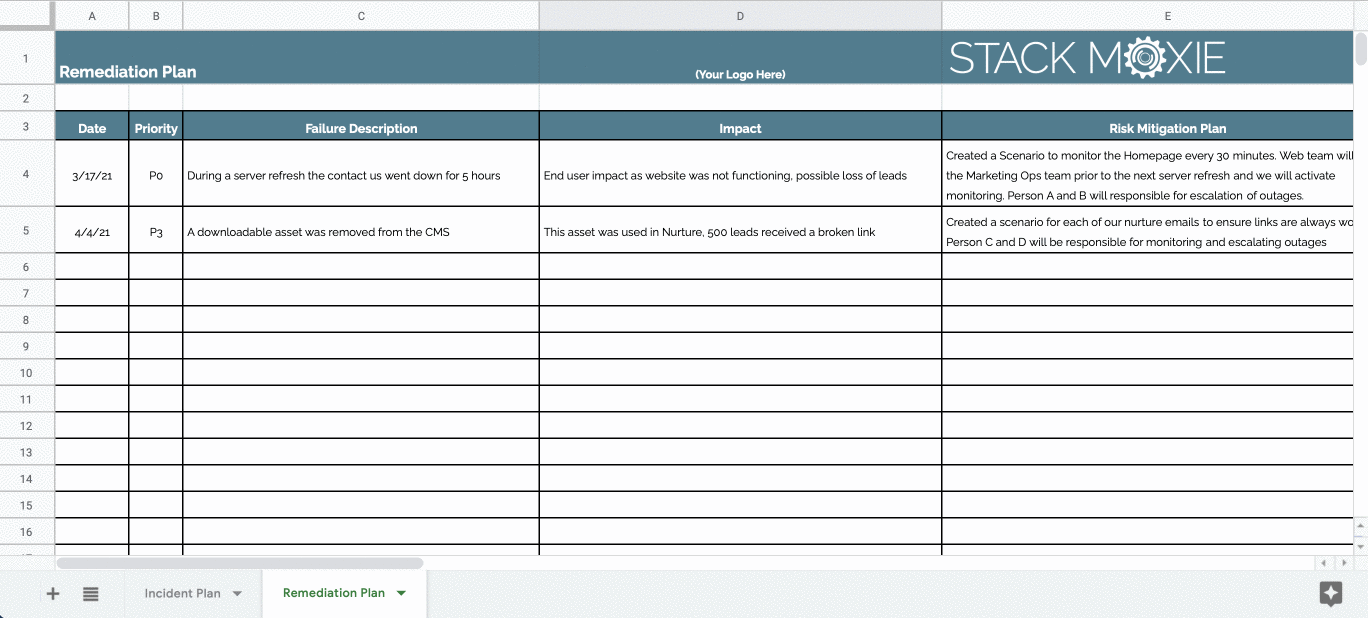
Incident & Remediation Plan Template for managing critical errors and
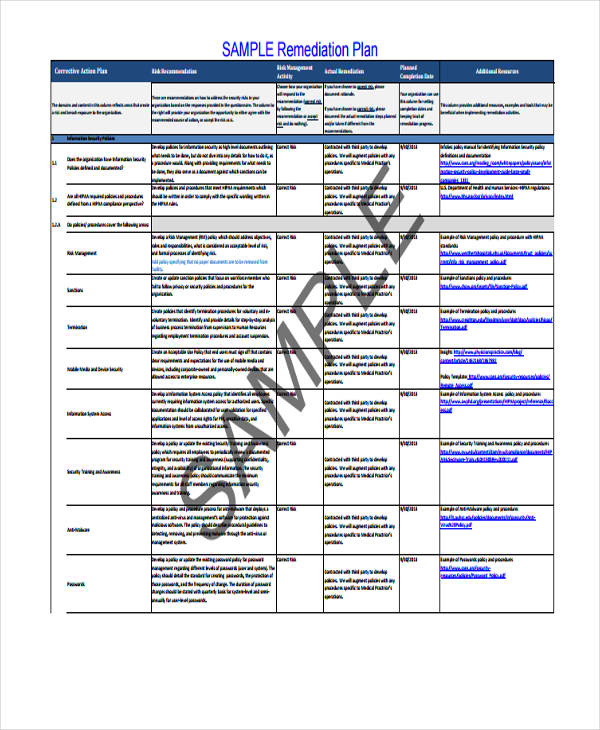
18+ Remediation Plan Templates Free Sample, Example Format Download

Remediation Instructions by Severity Report SC Report Template Tenable®
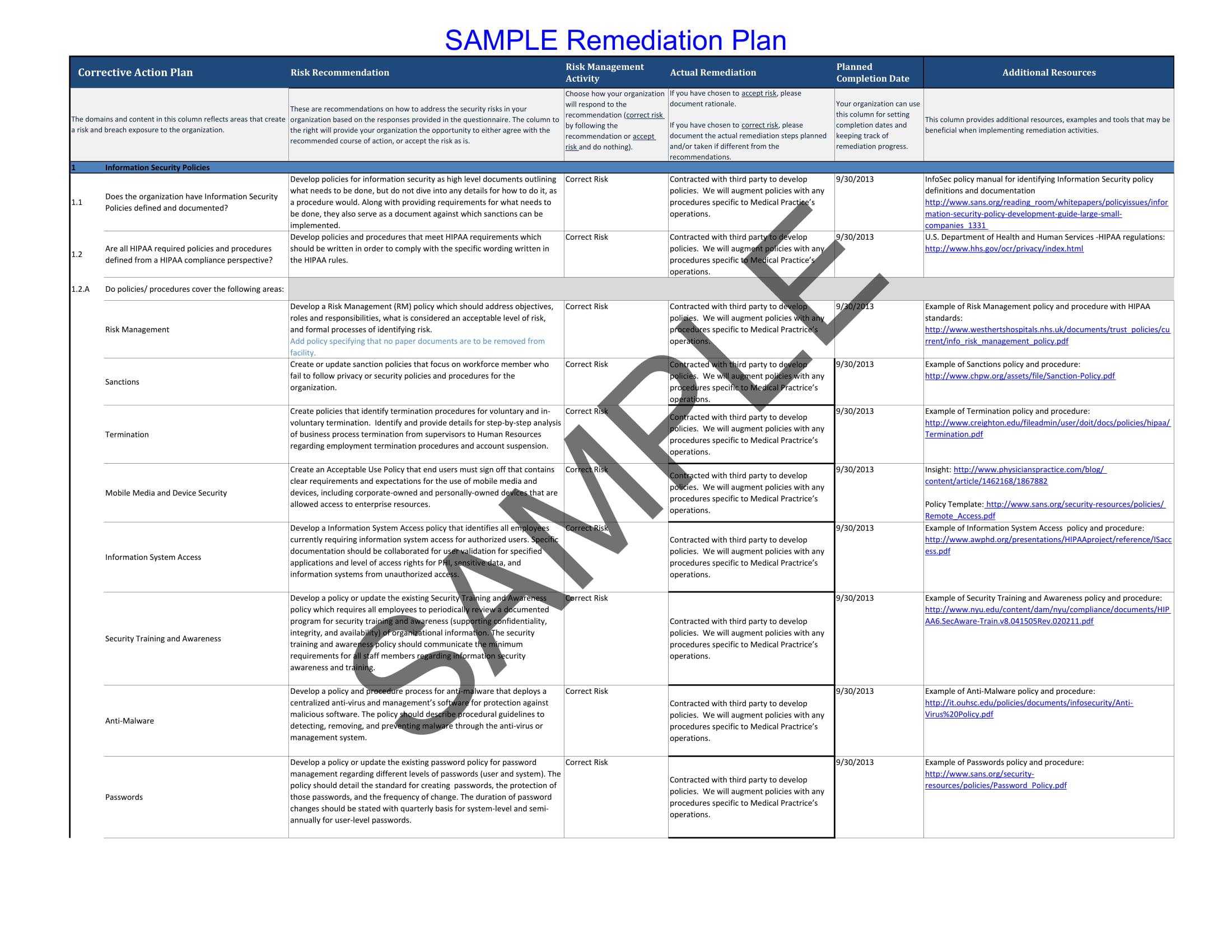
Remedial Action Plan 9+ Examples, Format, Pdf Examples
Enhance Your Cybersecurity With Our Vulnerability Management Template, A Comprehensive Guide For Identifying, Prioritizing, Resolving, And Documenting Vulnerabilities.
Web Our Vulnerability Assessment Report Template Outlines A Detailed Workflow For Identifying, Assessing And Resolving System And Network Vulnerabilities Effectively.
Effective Remediation Entails Continuous Processes That Together Are Called Vulnerability Management.
Finding Vulnerabilities Through Scanning And Testing, Prioritising, Fixing, And Monitoring Vulnerabilities.
Related Post: