Vulnerability Management Process Template
Vulnerability Management Process Template - Acquire necessary tools and equipment. Web sand boil formation at the toe of river embankments is the typical manifestation of the initiation and progression of an internal erosion process known as backward erosion piping, which is recognized to be a major concern in many river systems worldwide. Web security advisory description. This template can assist an enterprise in developing a data management. Fill out the questionnaire in the feature request template by. Web a deep dive into nist patch management. Minimize the overall attack surface. Web download our free vulnerability management policy template now. Identify and outline the scope of the assessment. Web optimize your security with our vulnerability management plan template. This template can assist an enterprise in developing a data management. Traffic is disrupted while the tmm. Web the cyclical nature of vulnerability management implies continuous process improvement, and it is crucial to understand how a single process feeds into other processes and how all tasks are interconnected across three domains. Web this document provides guidance on creating a security. This is not legal advice. Develop the vulnerability management plan. Web vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them. Web this vulnerability management process template provides a basic outline for creating your own comprehensive plan. Web a deep dive into nist patch management. Maintain compliance with security standards and regulations. Acquire necessary tools and equipment. Web this vulnerability management plan template is designed for it leaders and teams who are looking to create a plan to manage and mitigate vulnerabilities in their systems. However, this document also contains information useful to system. The cwe refers to vulnerabilities while the cve pertains to the. Maintain compliance with security standards and regulations. A successful exploit of this vulnerability can allow the attacker to cross a security boundary. Identify and outline the scope of the assessment. Fill out the questionnaire in the feature request template by. This is not legal advice. Web this vulnerability management plan template is designed for it leaders and teams who are looking to create a plan to manage and mitigate vulnerabilities in their systems. Identify all systems, applications and. The template provides a structure and guidance to help create a comprehensive plan that can be used to identify and track potential vulnerabilities, implement security patches. Web. Prevent the introduction of known vulnerabilities. Maintain compliance with security standards and regulations. Improve your cybersecurity with our robust vulnerability management process template, enabling systematic identification and mitigation of network risks. Web this vulnerability management process template provides a basic outline for creating your own comprehensive plan. Define the criticality of each asset. Web a deep dive into nist patch management. Web vulnerability management process template. The official web page of the ovmg contains a gif animation that illustrates connections among all tasks. The cwe refers to vulnerabilities while the cve pertains to the specific instance of a vulnerability in a system or product. This template can assist an enterprise in developing a. Evaluate risks associated with assets. Web this document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program. Web sand boil formation at the toe of river embankments is the typical manifestation of the initiation and progression of an internal erosion process known as backward erosion piping, which is recognized to be. Identify and list all devices or systems in the network. Prevent the introduction of known vulnerabilities. This template can assist an enterprise in developing a data management. Web this vulnerability management training course will show you the most effective ways to mature your vulnerability management program and move from identifying vulnerabilities to successfully treating them. Web vulnerability management process template. Web optimize your security with our vulnerability management plan template. By doing so, you ensure that all parties are on the same page and you set clear expectations concerning quality, performance, timeline, and budget. Establish a list of assets that need protection. Web vulnerability management process template. The primary audience is security managers who are responsible for designing and implementing. Web threat and vulnerability management plays a crucial role in safeguarding information systems. Web the cyclical nature of vulnerability management implies continuous process improvement, and it is crucial to understand how a single process feeds into other processes and how all tasks are interconnected across three domains. Effective threat and vulnerability management not only anticipates and counters potential cyber threats but also ensures. Improve your cybersecurity with our robust vulnerability management process template, enabling systematic identification and mitigation of network risks. Consider the specific systems, networks, applications, and processes that will be included in the assessment. Web implementing a vulnerability management process. The cwe refers to vulnerabilities while the cve pertains to the specific instance of a vulnerability in a system or product. Define the scope of the vulnerability assessment. A successful exploit of this vulnerability can allow the attacker to cross a security boundary. Web this vulnerability management training course will show you the most effective ways to mature your vulnerability management program and move from identifying vulnerabilities to successfully treating them. Create and maintain a documented vulnerability management process for enterprise assets. Identify and list all devices or systems in the network. The template provides a structure and guidance to help create a comprehensive plan that can be used to identify and track potential vulnerabilities, implement security patches. Web sand boil formation at the toe of river embankments is the typical manifestation of the initiation and progression of an internal erosion process known as backward erosion piping, which is recognized to be a major concern in many river systems worldwide. Web define the scope of vulnerability assessment this task involves determining the scope of the vulnerability assessment. It streamlines, regulates, and methodizes the application of patches for a smoother process.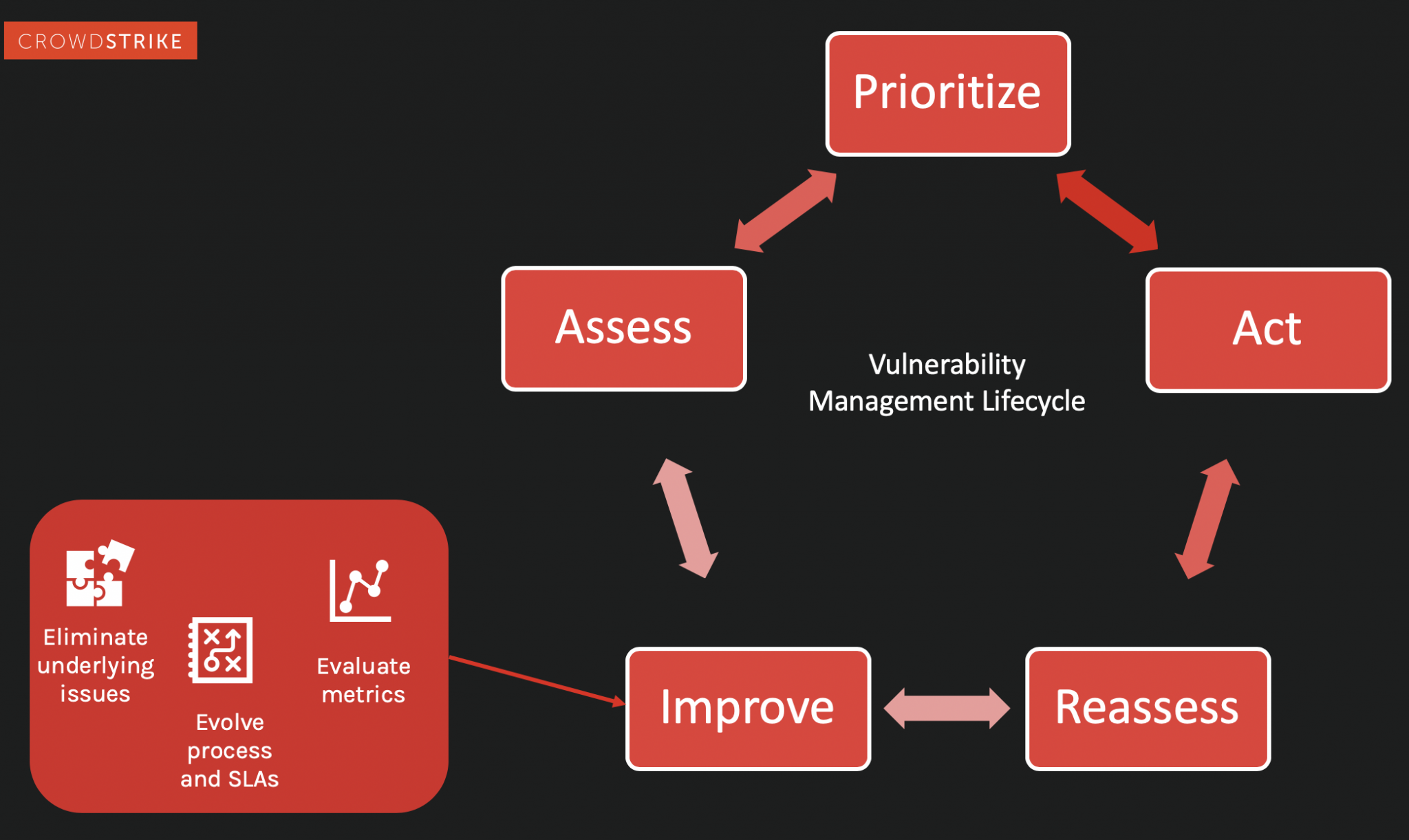
The Vulnerability Management Lifecycle (5 Steps) CrowdStrike

Vulnerability Management Services Optiv

Vulnerability Management Processes and tools

Vulnerability Assessment Tools & Checklists ManageEngine

Creating a Vulnerability Management Strategy zSecurity
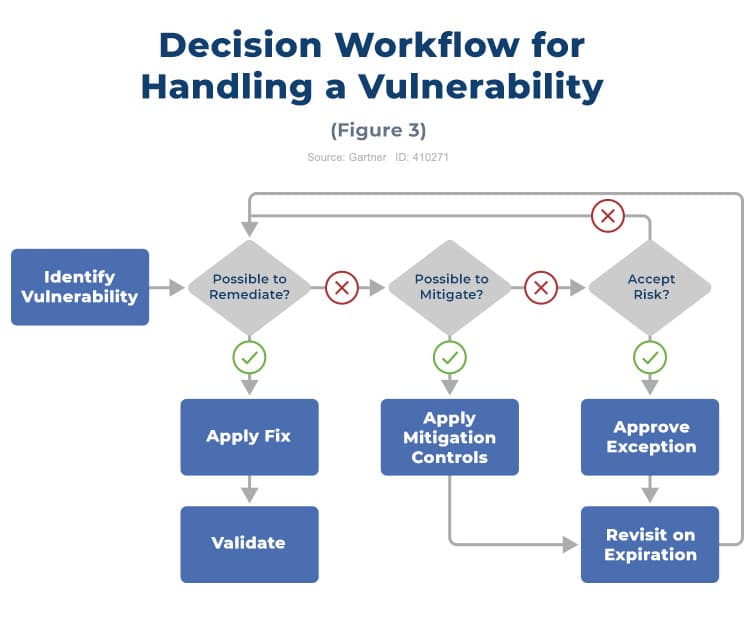
Vulnerability Management Process Flow Chart Rootshell
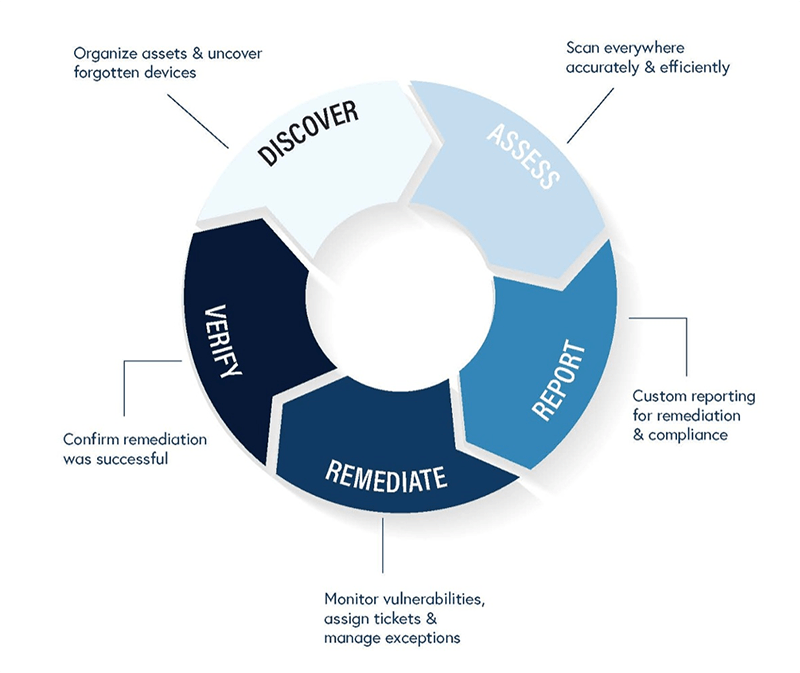
The Five Stages of Vulnerability Management
Vulnerability Management Process Template
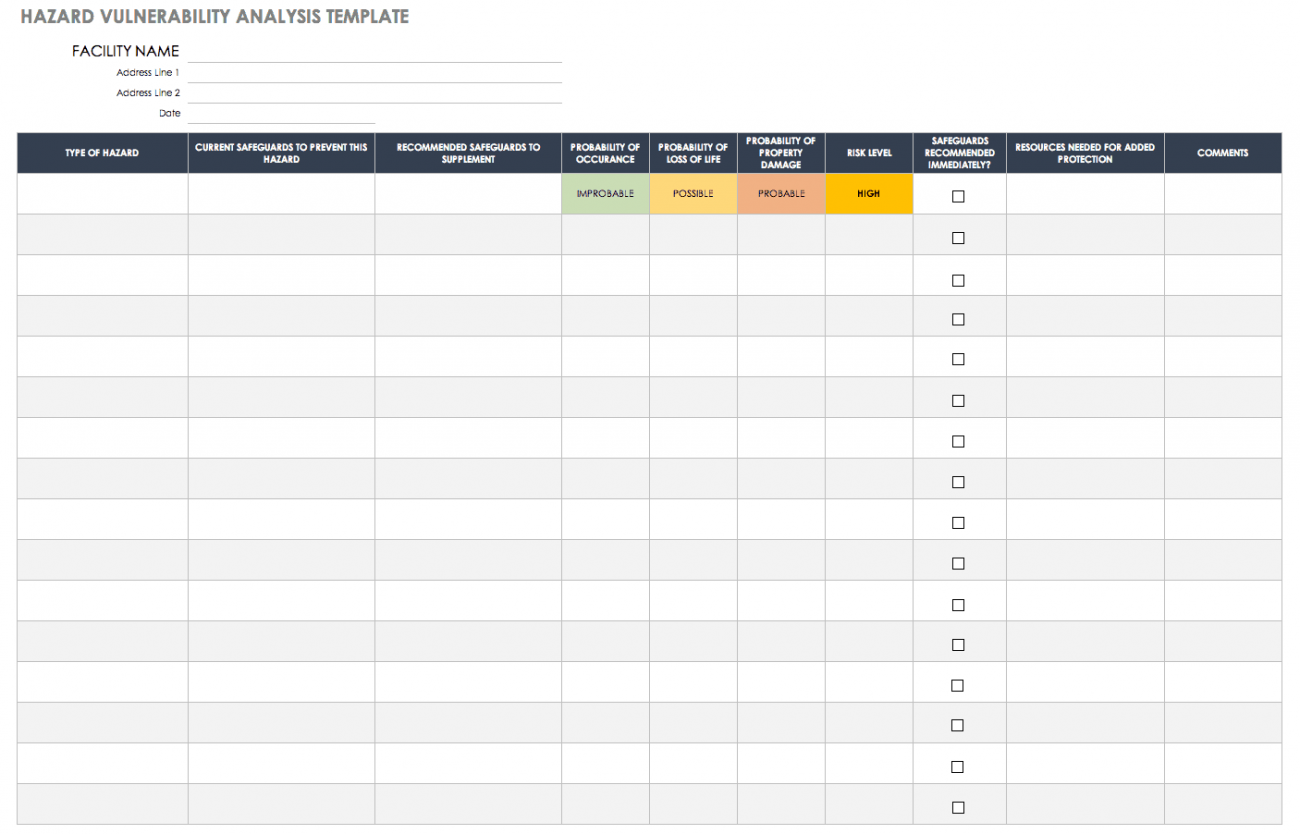
Free Vulnerability Assessment Templates Smartsheet
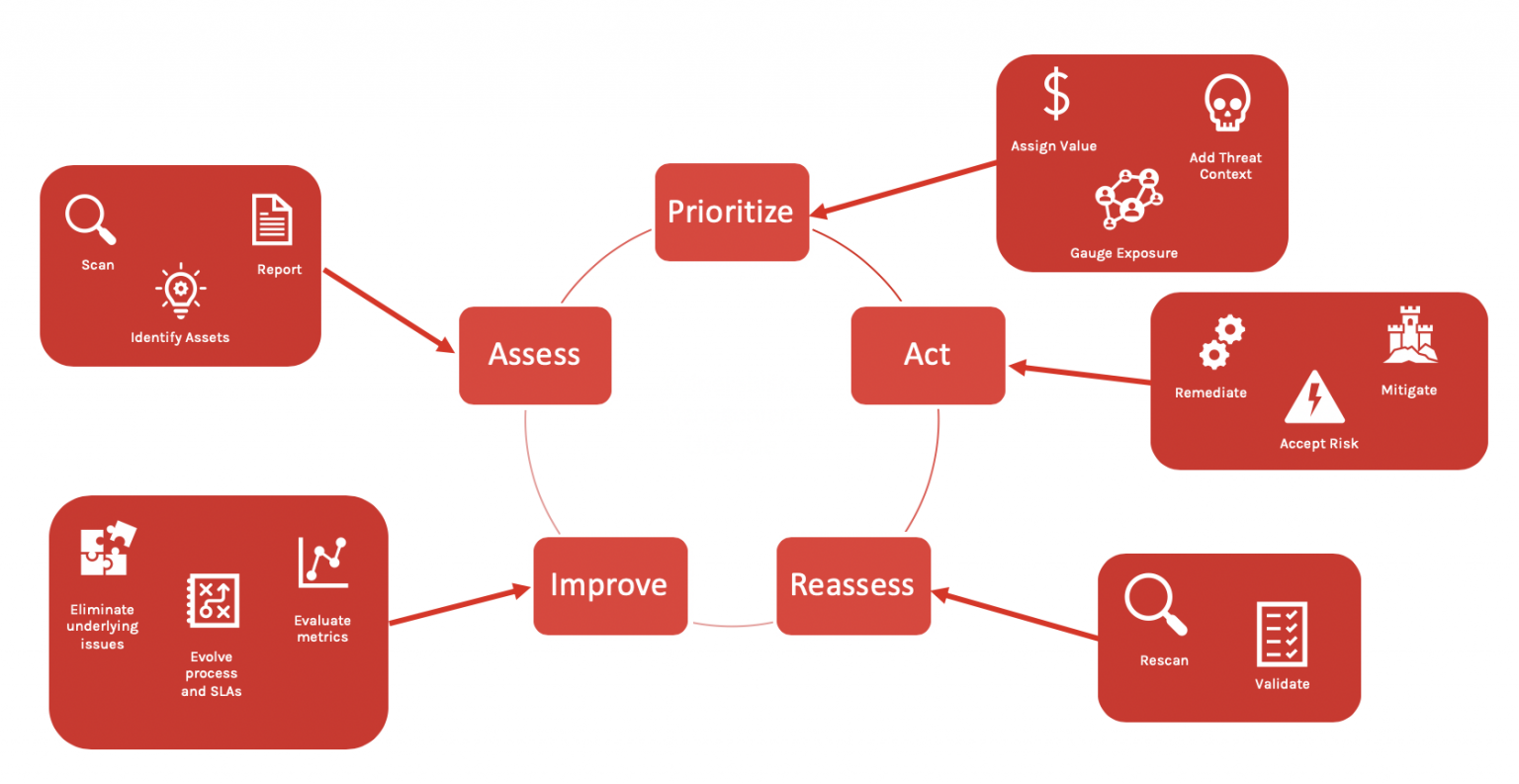
The Vulnerability Management Lifecycle (5 Steps) CrowdStrike
Prioritize Vulnerabilities Based On Risk And Exposure.
Establish A Vulnerability Assessment Team.
Documenting Procedures For Patch Management Is A Vital Part Of Ensuring Cybersecurity:
Minimize The Overall Attack Surface.
Related Post: