Vulnerability Management Plan Template
Vulnerability Management Plan Template - Web vulnerability risk assessment template. Web security patch management team members. Web enhance your cybersecurity with our vulnerability management template, a comprehensive guide for identifying, prioritizing, resolving, and documenting. It outlines the strategies and procedures to identify, assess, and remediate vulnerabilities. Vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. Web a free policy template for establishing rules to review, evaluate, apply, and verify system updates to mitigate vulnerabilities in the it environment and the risks associated with. Web this task focuses on developing a comprehensive vulnerability management plan. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Web understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. 145,000+ plugins2 million downloads30,000+ organizations24/7 tenable support Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Boost your system's security with our vulnerability management program template, enabling comprehensive identification,. Web free vulnerability management policy template. It outlines the strategies and procedures to identify, assess, and remediate vulnerabilities. This policy template is meant to supplement the cis. Web improve your cybersecurity with our robust vulnerability management process template, enabling systematic identification and mitigation of network risks. Vulnerabilities are weaknesses in an information system, system security procedures, internal controls, or implementation that could be. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy. The process areas described include • developing. This policy template is meant to supplement the cis. Web the three documents you’ve provided are templates for vulnerability management policies, each with unique components and structures. Web a free policy template for establishing rules to review, evaluate, apply, and verify system updates to mitigate vulnerabilities in the it environment and the risks associated with. Any articles, templates, or information. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Web improve your cybersecurity with our robust vulnerability management process template, enabling systematic identification and mitigation of network risks. A comprehensive guide for systematic detection, mitigation, and review of risks. Web security patch management team members. Vulnerabilities are weaknesses in an information system, system security. A comprehensive guide for systematic detection, mitigation, and review of risks. Web the three documents you’ve provided are templates for vulnerability management policies, each with unique components and structures. It covers three focus areas,. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable repeatable functions: The process. Web download your free vulnerability management template pack to assist you in assessing and planning your organization’s data security posture. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Web the objective of this document is to bridge the gaps in information security by breaking down complex. Web a vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. Web understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. Web vulnerability risk assessment template. Over 800 clients served100% audit pass ratestay compliantdod compliance Web enhance your cybersecurity with our vulnerability management template,. 145,000+ plugins2 million downloads30,000+ organizations24/7 tenable support This policy template is meant to supplement the cis. It outlines the strategies and procedures to identify, assess, and remediate vulnerabilities. Any articles, templates, or information provided by smartsheet on the website are for reference only. Over 800 clients served100% audit pass ratestay compliantdod compliance Web security patch management team members. Web understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention, and resources. Web download your free vulnerability management template pack to assist you in assessing and planning your organization’s data security posture. Web enhance your cybersecurity with our vulnerability management template, a comprehensive guide for identifying, prioritizing, resolving, and documenting.. Web the three documents you’ve provided are templates for vulnerability management policies, each with unique components and structures. Web vulnerability management is a continuous, proactive, and often automated process that keeps your computer systems, networks, and enterprise applications safe from. Web a vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security. 145,000+ plugins2 million downloads30,000+ organizations24/7 tenable support Web a free policy template for establishing rules to review, evaluate, apply, and verify system updates to mitigate vulnerabilities in the it environment and the risks associated with. Web the objective of this document is to bridge the gaps in information security by breaking down complex problems into more manageable repeatable functions: Web a vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. Web here are the top six vulnerability management systems: Create a comprehensive and strategic plan to manage and mitigate vulnerabilities in your systems and infrastructure with this template. A comprehensive guide for systematic detection, mitigation, and review of risks. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy. Web download your free vulnerability management template pack to assist you in assessing and planning your organization’s data security posture. Web free vulnerability management policy template. Web vulnerability risk assessment template. It covers three focus areas,. Best overall vulnerability management solution. Web we've created a vulnerability management policy template to help organizations assess and patch security vulnerabilities. Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Web security patch management team members.
Vulnerability Assessment Plan Template in Word, Pages, Google Docs
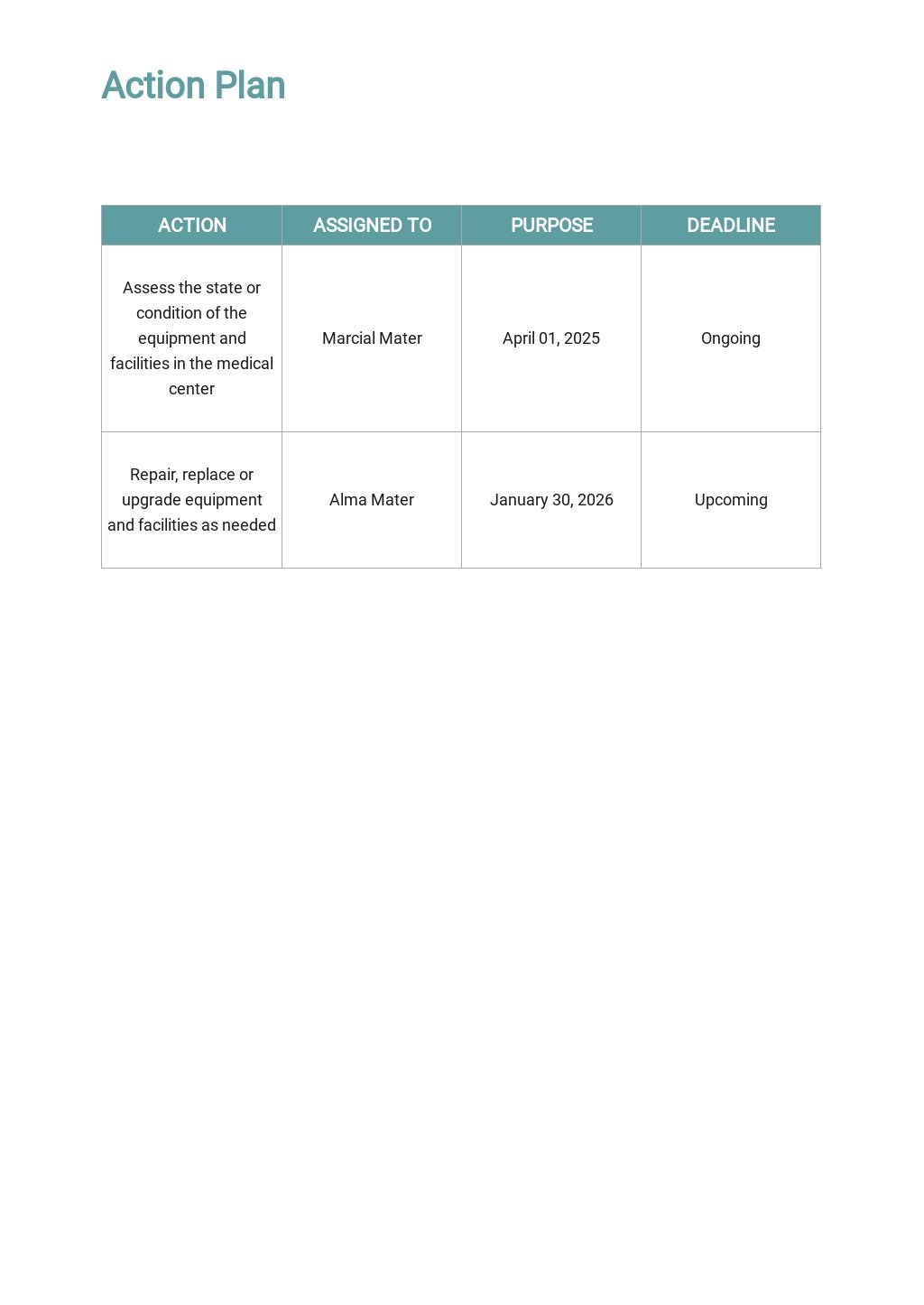
Free Vulnerability Assessment Plan Template Google Docs, Word, Apple

Free Vulnerability Assessment Templates Smartsheet

Free Vulnerability Assessment Templates Smartsheet

Creating a Vulnerability Management Strategy Dr. Erdal Ozkaya

Vulnerability Assessment Template Download Printable PDF Templateroller

Vulnerability Sample Report Security Assessment, Report With Patch
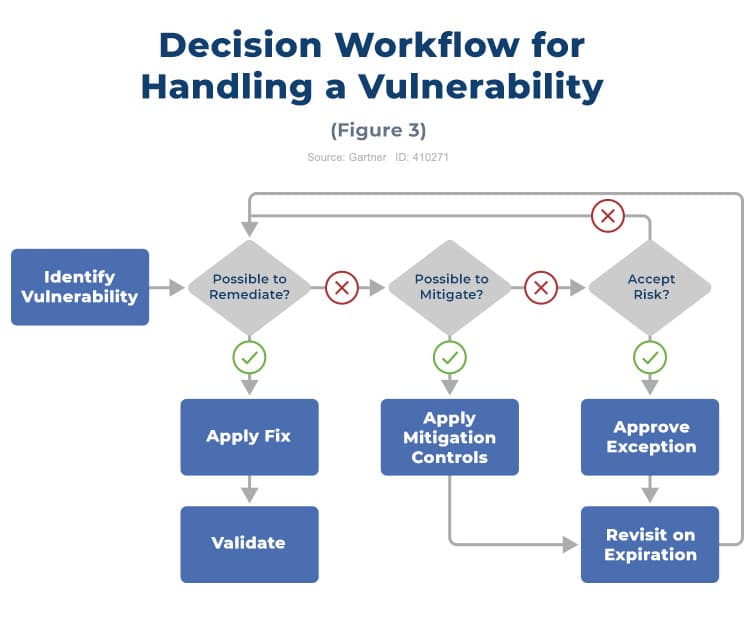
Vulnerability Management Process Flow Chart Rootshell

Security Vulnerability Assessment Template PDF Sample Kelitbanganwonogiri
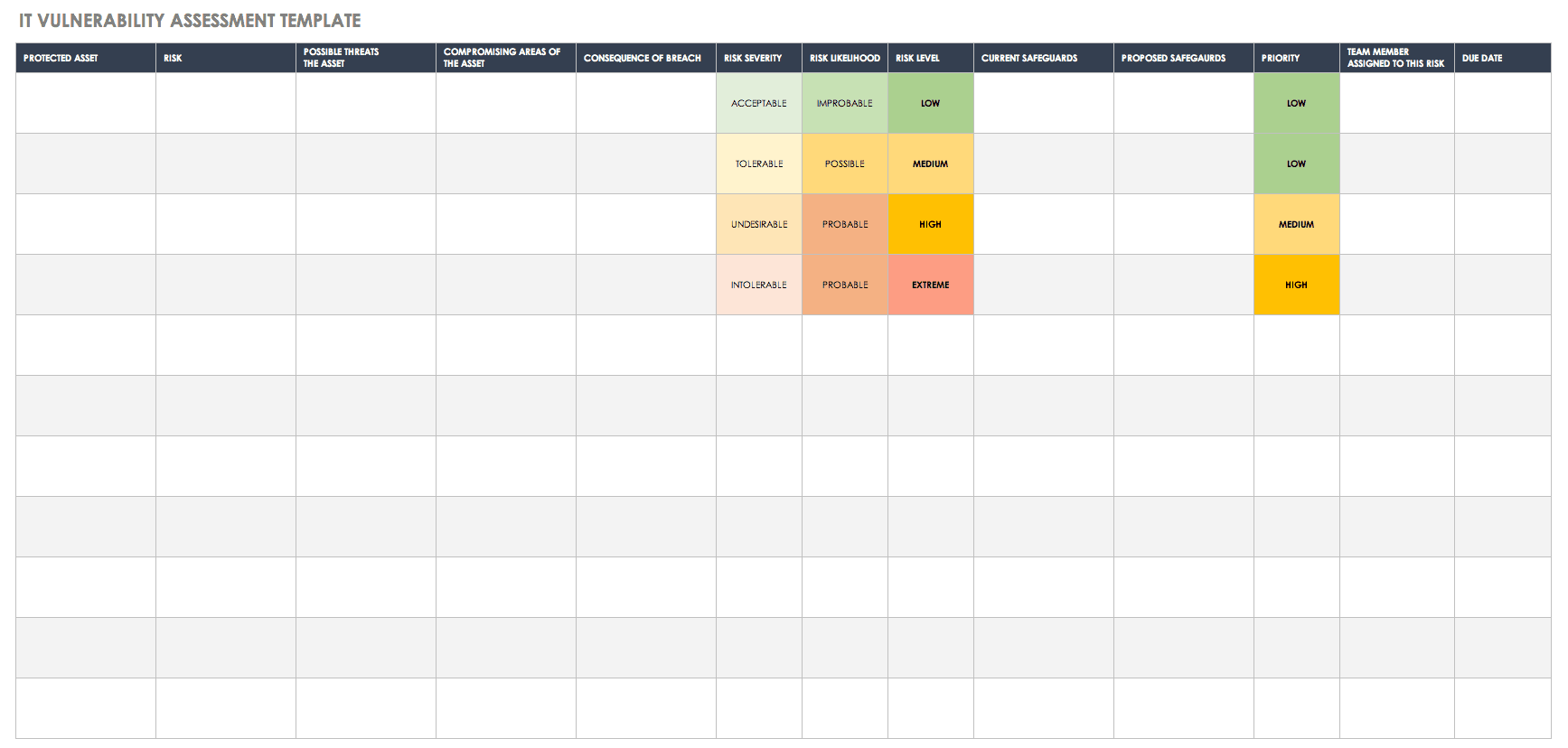
Free Vulnerability Assessment Templates Smartsheet
Web Improve Your Cybersecurity With Our Robust Vulnerability Management Process Template, Enabling Systematic Identification And Mitigation Of Network Risks.
Web Understanding And Managing Vulnerabilities Is A Continuous Activity, Requiring Focus Of Time, Attention, And Resources.
Boost Your System's Security With Our Vulnerability Management Program Template, Enabling Comprehensive Identification,.
Web The Three Documents You’ve Provided Are Templates For Vulnerability Management Policies, Each With Unique Components And Structures.
Related Post: