Threat Model Template
Threat Model Template - Web template for new models. Description of the subject to be modeled; Data flow diagram online banking application. Web this document describes a structured approach to application threat modeling that enables you to identify, quantify, and address the security risks associated with an application. Threat models are a wonderful tool to understand the risk represented by a. September 4, 2016— leave a comment. Web threat modeling is designed to provide this systematic approach, with the aim of finding and addressing issues early in the design process, when the mitigations have a low relative. Threat modeling for ceph rbd. Web a threat modeling tool is defined as software that enables you to proactively identify and resolve possible security threats to your software, data, or device. Web a threat model typically includes: Web many threat modeling approaches begin with a template, which is based on some previously effective threat model. Identify threats, describe them, propose mitigation plans and map them to nist csf controls. Web stride, a mnemonic, is one of the most popular threat modeling frameworks. A mix of frustrations, aspirations, and unsolicited opinions regarding the current state of threat modeling. Threat modeling for ceph rbd. Description of the subject to be modeled; The first step in the threat model process is to define the scope of the threat model, including the system or application to be modeled, its assets, data, and. Web many threat modeling approaches begin with a template, which is based on some previously effective threat model. A. Assumptions that can be checked or challenged in the future as the threat landscape changes;. Web many threat modeling approaches begin with a template, which is based on some previously effective threat model. Web then use that template as the starting point for your threat model. Identify threats, describe them, propose mitigation plans and map them to nist csf controls.. Description of the subject to be modeled; Identify threats, describe them, propose mitigation plans and map them to nist csf controls. It supports various threat modeling methods and. How to start your own. Threat models are a wonderful tool to understand the risk represented by a. Web template for new models. Web then use that template as the starting point for your threat model. It supports various threat modeling methods and. Web a threat model typically includes: In the context of application security, threat modeling is a structured, repeatable process used to gain actionable insights into the security characteristics of a particular. Web this document describes a structured approach to application threat modeling that enables you to identify, quantify, and address the security risks associated with an application. Web owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. How to start your own. Threat modeling knowledge bases and templates. The first step. In the context of application security, threat modeling is a structured, repeatable process used to gain actionable insights into the security characteristics of a particular. A mix of frustrations, aspirations, and unsolicited opinions regarding the current state of threat modeling are. Threat models are a wonderful tool to understand the risk represented by a. Web stride, a mnemonic, is one. Web a threat modeling tool is defined as software that enables you to proactively identify and resolve possible security threats to your software, data, or device. Web microsoft threat modeling template files. Identify threats, describe them, propose mitigation plans and map them to nist csf controls. Web template for new models. In the context of application security, threat modeling is. Identify threats, describe them, propose mitigation plans and map them to nist csf controls. Data flow diagram online banking application. Web owasp threat dragon is a web or desktop application that helps you create threat model diagrams for secure development. An attacker attempts to impersonate an entity — for example, a user, a service — that. Web next generation cyber. Web template for new models. You must select which template to use before creating a model. Web then use that template as the starting point for your threat model. In the context of application security, threat modeling is a structured, repeatable process used to gain actionable insights into the security characteristics of a particular. An attacker attempts to impersonate an. Web template for new models. Web then use that template as the starting point for your threat model. An attacker attempts to impersonate an entity — for example, a user, a service — that. It makes sense to use a template and avoid having to. Web this document describes a structured approach to application threat modeling that enables you to identify, quantify, and address the security risks associated with an application. A mix of frustrations, aspirations, and unsolicited opinions regarding the current state of threat modeling are. It supports various threat modeling methods and. If all else fails, find an existing threat model outside. How to start your own. Threat modeling knowledge bases and templates. Threat models are a wonderful tool to understand the risk represented by a. September 4, 2016— leave a comment. Data flow diagram online banking application. Description of the subject to be modeled; You must select which template to use before creating a model. Web a threat modeling tool is defined as software that enables you to proactively identify and resolve possible security threats to your software, data, or device.
The threatmodeltemplates from AzureArchitecture Coder Social
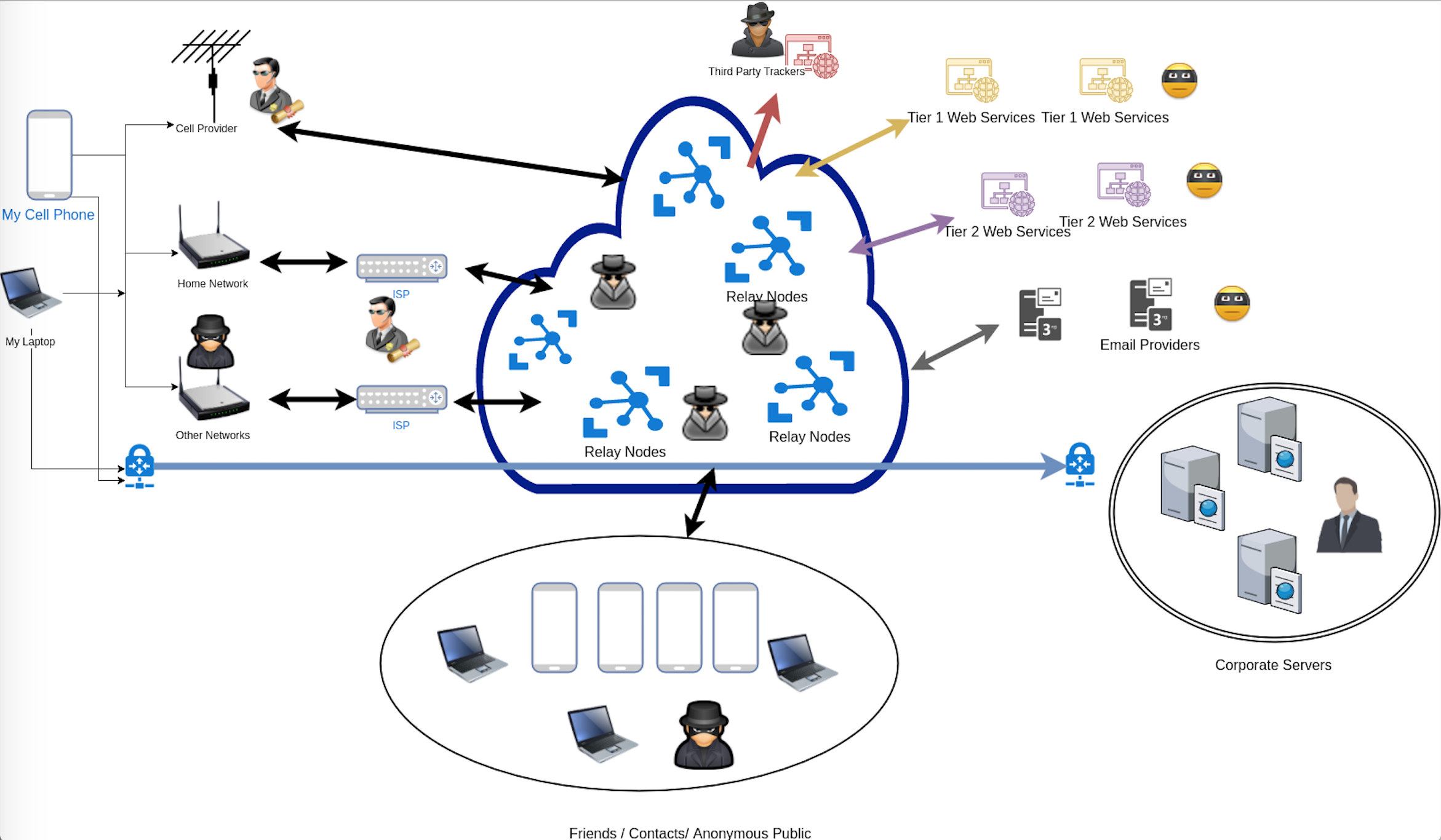
Creating Your Own Personal Threat Model
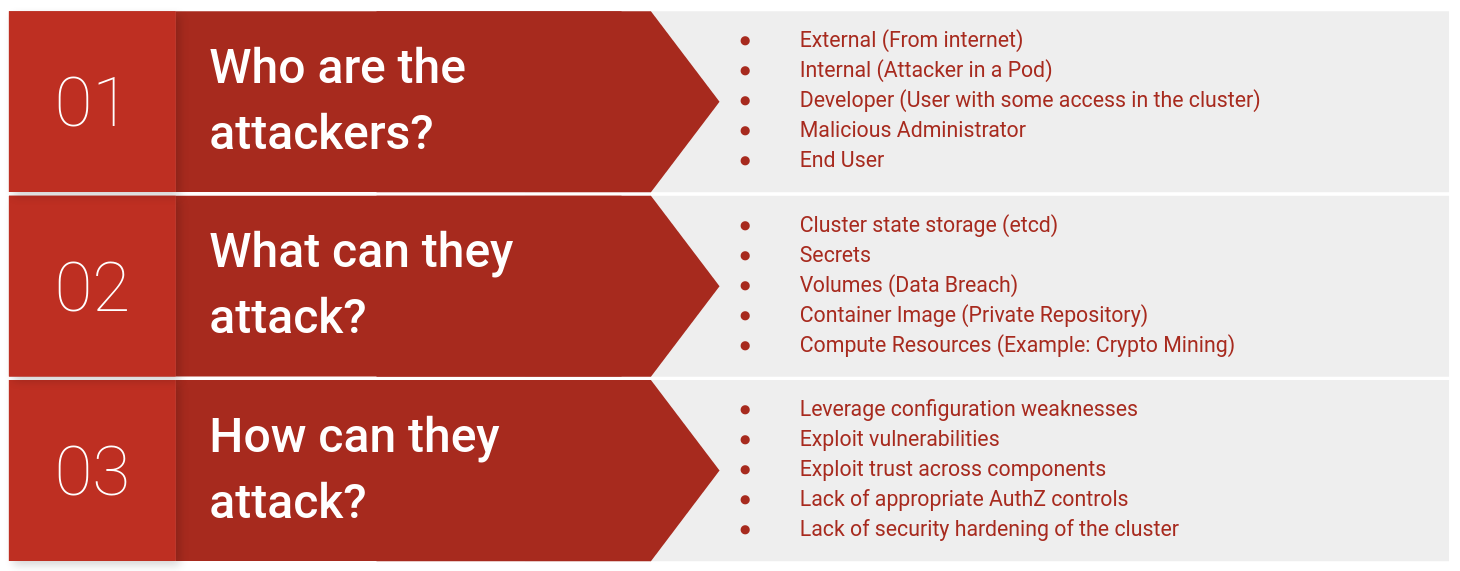
Threat Modeling Threat Model Diagram Template
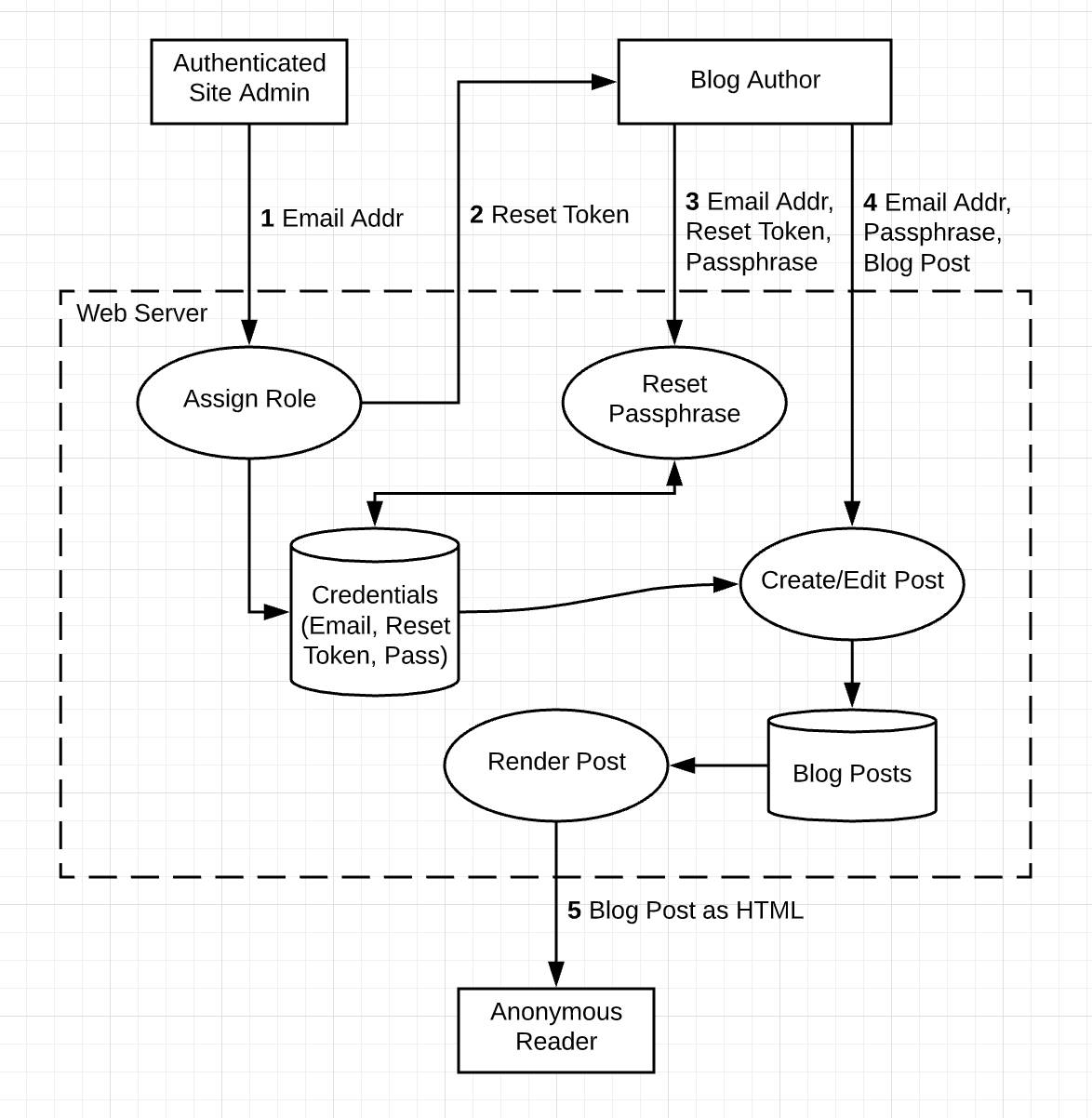
Create a Threat Model Unit Salesforce Trailhead
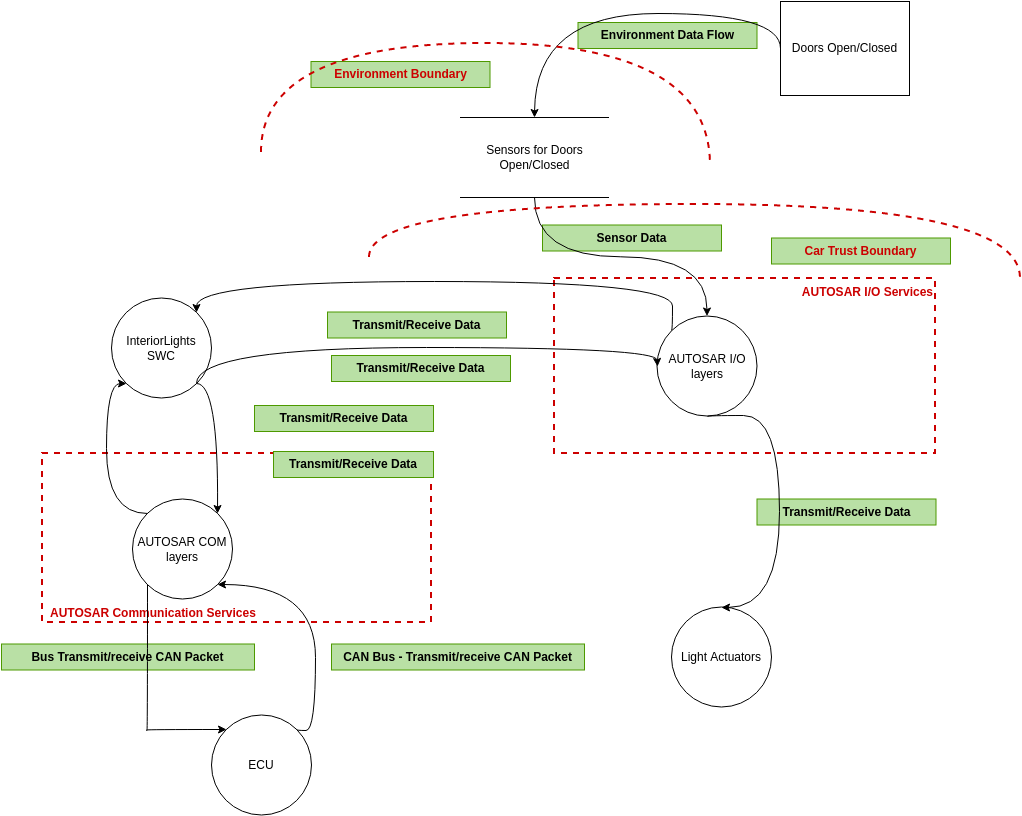
Threat Model Security Testing Guide
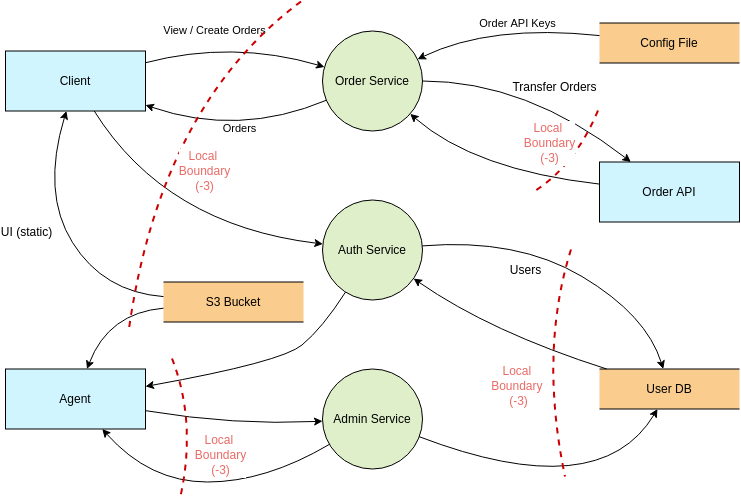
Threat Model Template
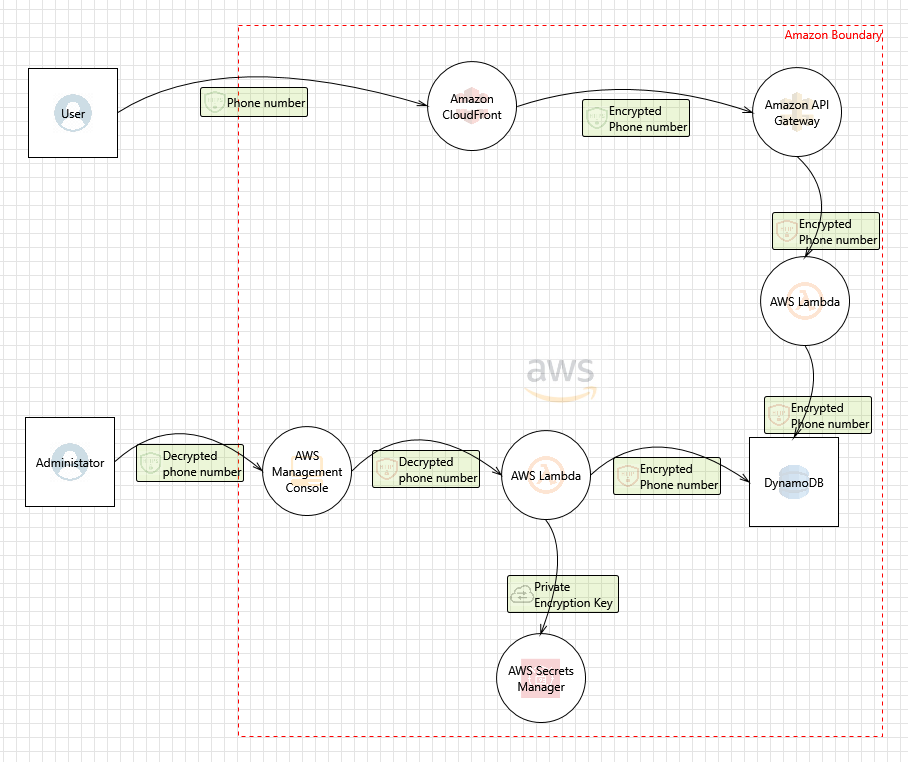
GitHub rusakovichma/awsthreatmodelingtooltemplate Amazon Web
GitHub AzureArchitecture/threatmodeltemplates Templates for the
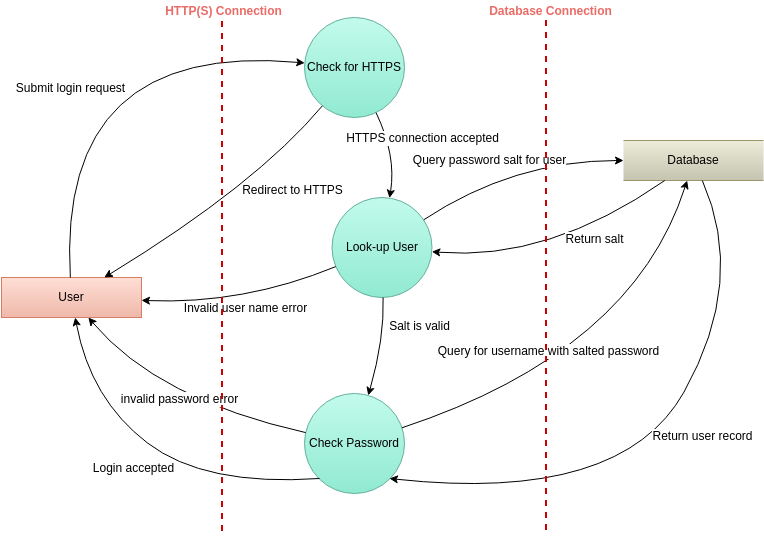
Threat Modeling Threat Model Diagram Template
![What is Threat Modeling? All you need to know [OverView]](https://www.acte.in/wp-content/uploads/2020/07/PASTA.png)
What is Threat Modeling? All you need to know [OverView]
Identify Threats, Describe Them, Propose Mitigation Plans And Map Them To Nist Csf Controls.
Web Threat Modeling Is Designed To Provide This Systematic Approach, With The Aim Of Finding And Addressing Issues Early In The Design Process, When The Mitigations Have A Low Relative.
Web Next Generation Cyber Infrastructure (Ngci) Apex Cyber Risk Metrics And Threat Model Assessment This Hssedi Task Order Is To Enable The Dhs Science And Technology.
Web A Threat Model Typically Includes:
Related Post: