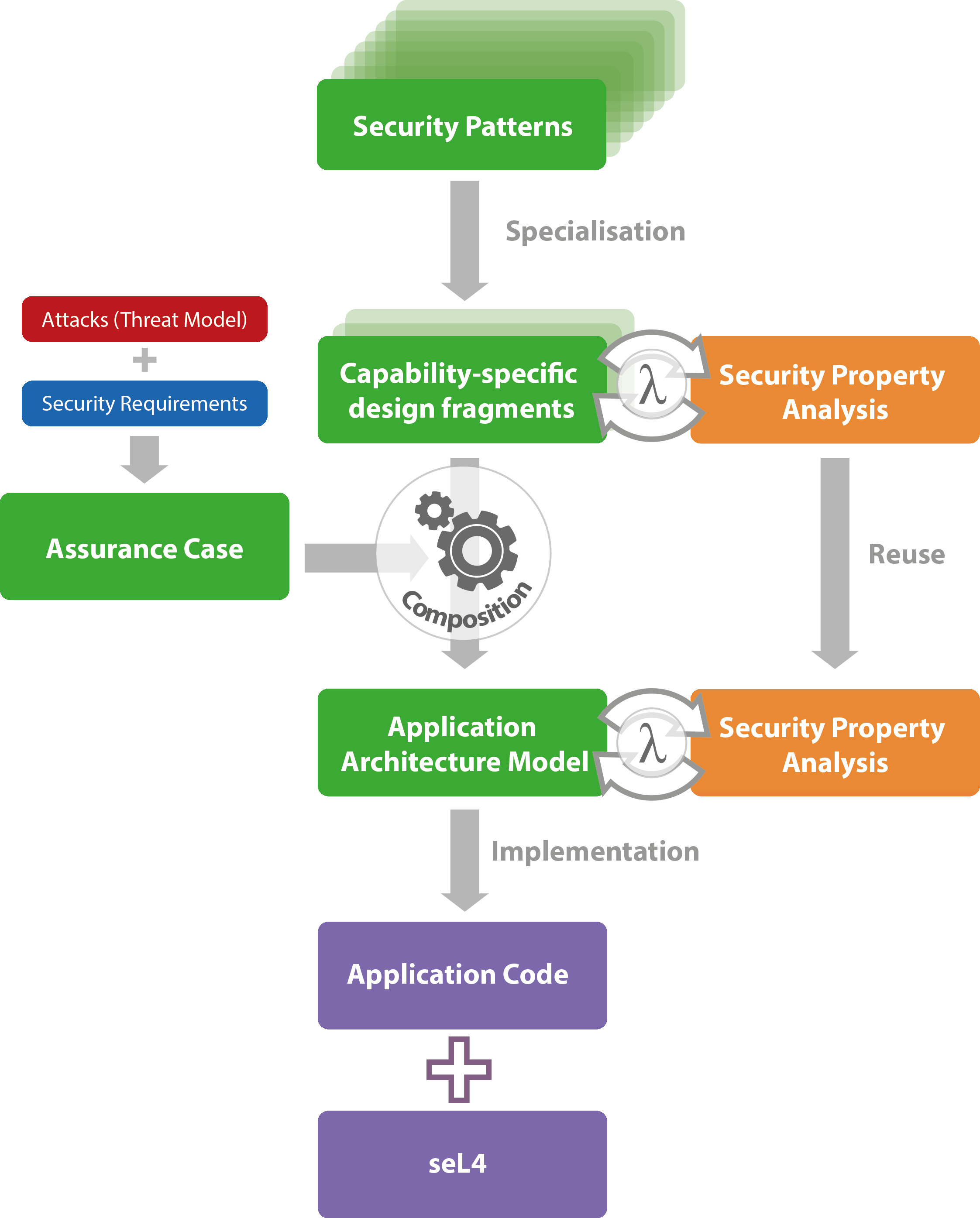
Security Pattern
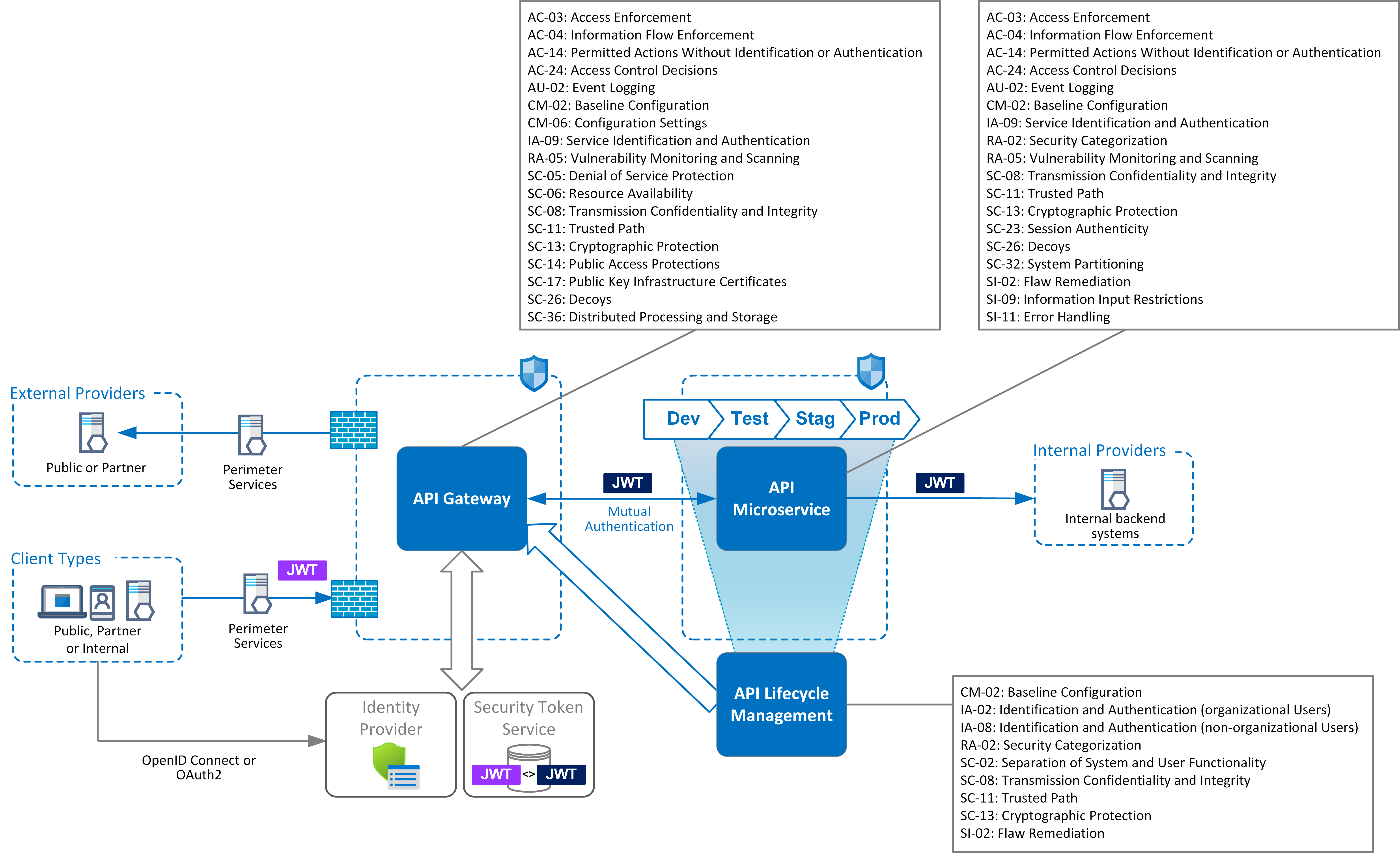
Security Pattern - Standard of good practice, security principles, and. An authenticated user owns a security context (erg. Among the 274 papers reviewed for this study, only 8% have devoted their efforts towards evaluation, whereas the development and usage of security patterns are respectively responsible for 52% and 35% of the research (rq2). Patterns can be bounded around the product scope for that the project, and in coordination with the product owner. Web security patterns for microservice architectures. Web map controls to threats. Describes the security issues addressed by the pattern. Collate and extract the security pattern for each asset, by combining the previous mappings for threats, assets and controls. In fiscal 2019, the total number of people from the northwest african. The guard checks inside the policy whether the context of this user and the rules match and provides or denies access to the resource. Written in context of a security problem and how it affects the asset. While the implementation of mfa can take many forms, common patterns for enterprise systems include: For each threat identify the mitigating security controls. Web in this section, i’ll introduce a systemic approach to develop security patterns. An authenticated user owns a security context (erg. 2006).the problem solved by the pattern is briefly described in its. Abstracted from specific vendor or technology implementations. If you have user input, sanitize the data and remove malicious characters. The documentation for jdk 22 includes developer guides, api documentation, and release notes. To facilitate using the security patterns, we adopted a pattern template that consists of the following: Web the global center for health security is the premier u.s. Patterns can be bounded around the product scope for that the project, and in coordination with the product owner. Centralized pattern with embedded policy decision point¶ in this pattern, access control rules are defined centrally but stored and evaluated at the microservice level. Within these guides, we establish security. If you have user input, sanitize the data and remove malicious characters. Web security patterns are increasingly being used by developers who take security into serious consideration from the creation of their work. These diagrams are then annotated with references to the nist controls catalog. Web security pattern helps creators of smart and connected devices design, implement, and operate their. A different cow tissues may help to explain the pattern of illness being seen in the outbreak of h5n1 bird flu in u.s. Web he worked at stmicroelectronics from 2003 to 2017, covering the role of principal engineer of security and cryptography. Web a security pattern is typically defined by the following following 4 characteristics. Standard of good practice, security. Web a security pattern is typically defined by the following following 4 characteristics. The guard checks inside the policy whether the context of this user and the rules match and provides or denies access to the resource. Among the 274 papers reviewed for this study, only 8% have devoted their efforts towards evaluation, whereas the development and usage of security. Web the government accused russia’s domestic intelligence agency, the federal security service, or f.s.b., of a pattern of “malign activity” in britain and europe, including hacking and leaking. For each threat identify the mitigating security controls. Maintains traceability of prescribed controls to the original threats being mitigated. Web security pattern helps creators of smart and connected devices design, implement, and. In context of a security problem and how it affects the asset. While the implementation of mfa can take many forms, common patterns for enterprise systems include: Abstracted from specific vendor or technology implementations. The following table summarizes cloud design patterns that support the goals of security. Written in context of a security problem and how it affects the asset. Web the ransomware activity in q1 of 2024 continues the substantial growth pattern that we saw develop over the course of 2023. Highlights the reasons for choosing the pattern and provides. In this article we discuss how the evolution of design patterns has shaped the prevalent understanding of security patterns. Web a security pattern is a solution to a security. Web security patterns are increasingly being used by developers who take security into serious consideration from the creation of their work. Centralized pattern with embedded policy decision point¶ in this pattern, access control rules are defined centrally but stored and evaluated at the microservice level. In fiscal 2019, the total number of people from the northwest african. Abstract design patterns. Among the 274 papers reviewed for this study, only 8% have devoted their efforts towards evaluation, whereas the development and usage of security patterns are respectively responsible for 52% and 35% of the research (rq2). Within these guides, we establish security patterns that are. He has been a contract professor at politecnico di milano, teaching cryptography to the master course of computer science from 2004 to 2010. Web available patterns (nist sp 800:53 framework) security pattern: Web security patterns are increasingly being used by developers who take security into serious consideration from the creation of their work. Standard of good practice, security principles, and. These diagrams are then annotated with references to the nist controls catalog. Ronald wassermann and betty h.c. In fiscal 2019, the total number of people from the northwest african. An authenticated user owns a security context (erg. Web security patterns are increasingly being used by developers who take security into serious consideration from the creation of their work. Web and some countries that previously sent negligible numbers of migrants to the u.s. Maintains standards for threat and control taxonomies to. While the implementation of mfa can take many forms, common patterns for enterprise systems include: In the proceeding sections of this guide, i’ll provide reference how the security pattern for source code management.it’s probably not the best example for demonstrating the value of security patterns but does simplify the example so that we can focus on the process to. Web map controls to threats.
Security patterns vector free vector download (20,109 Free vector) for
Secure Design using Security Patterns TS

Security pattern (23738) Free EPS Download / 4 Vector
How to Write A Security Pattern Service Mesh

A variety of security pattern shading vector free download
How to Write A Security Pattern API based Microservices
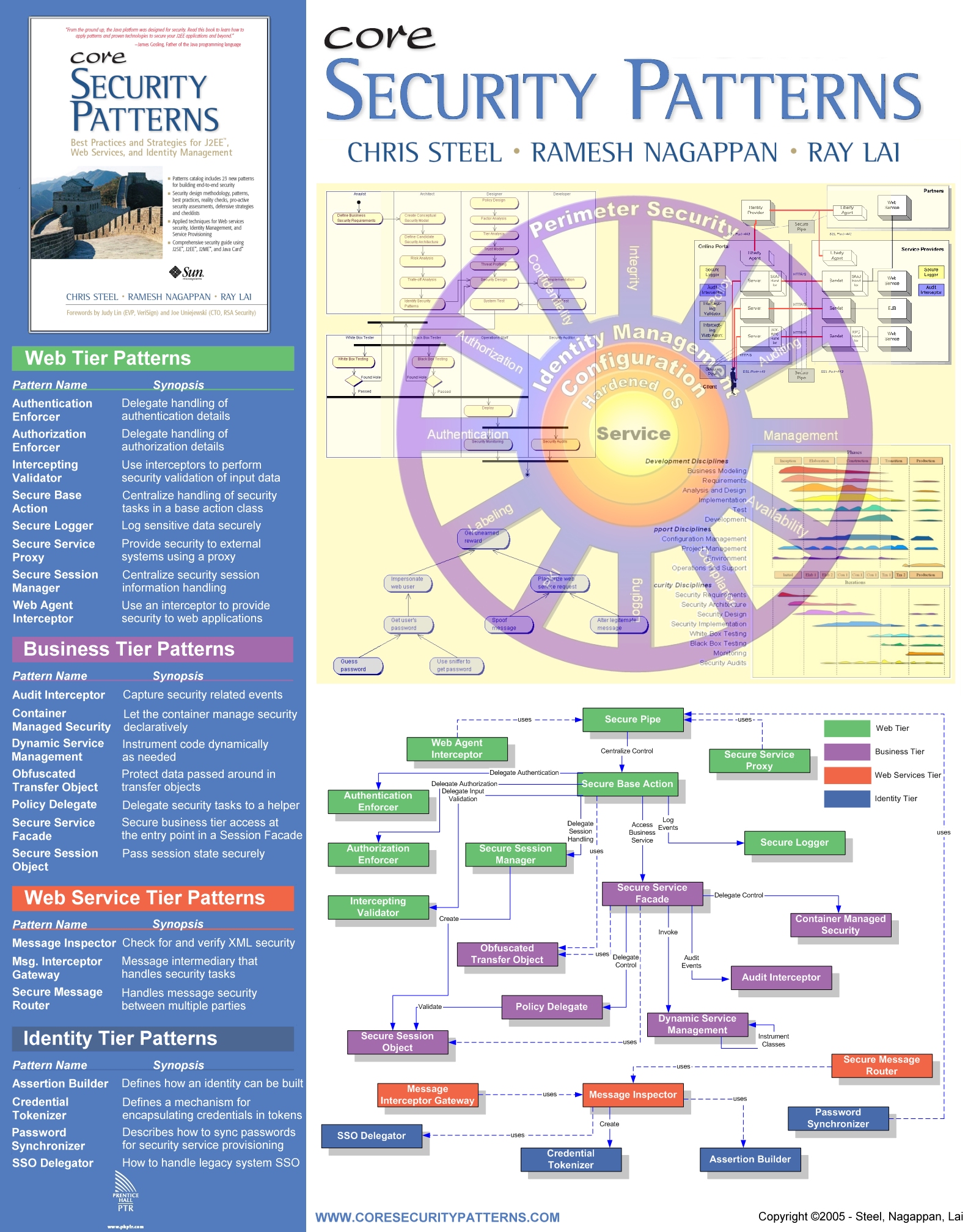
Core Security Patterns Ramesh Nagappan CISSP, Chris Steel CISSP
Security pattern 01 vector Free Vector / 4Vector
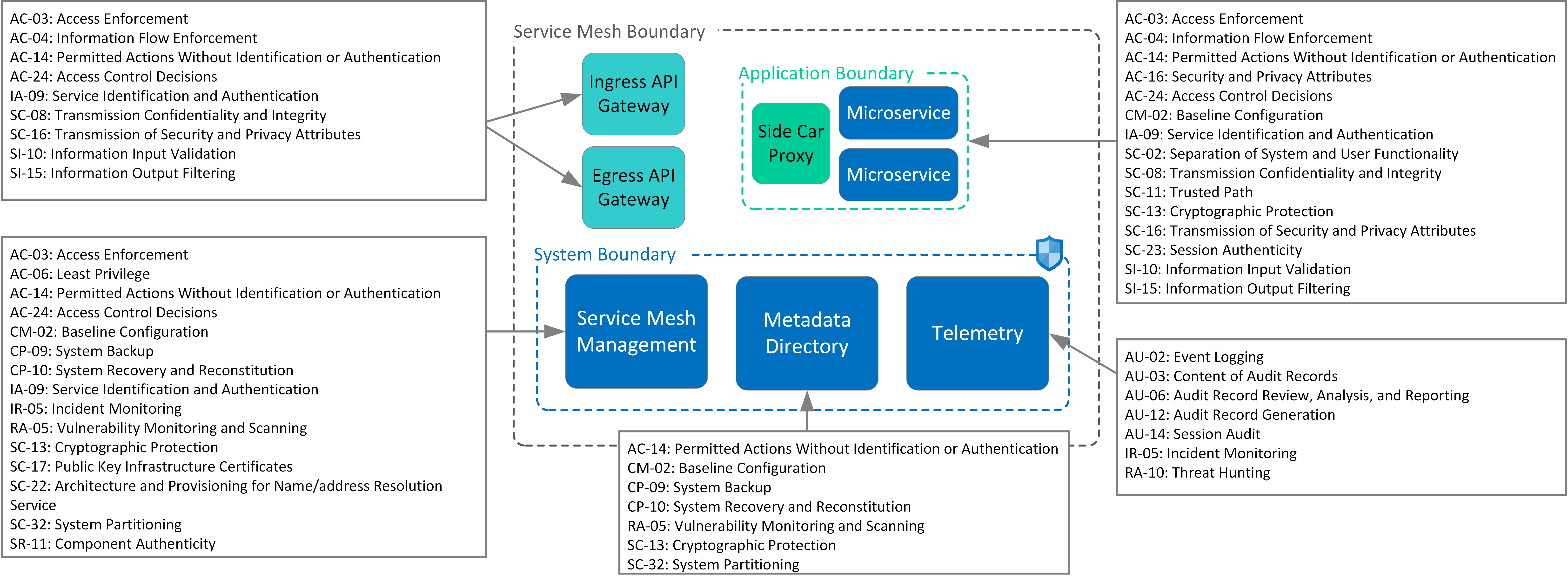
How to Write A Security Pattern Service Mesh
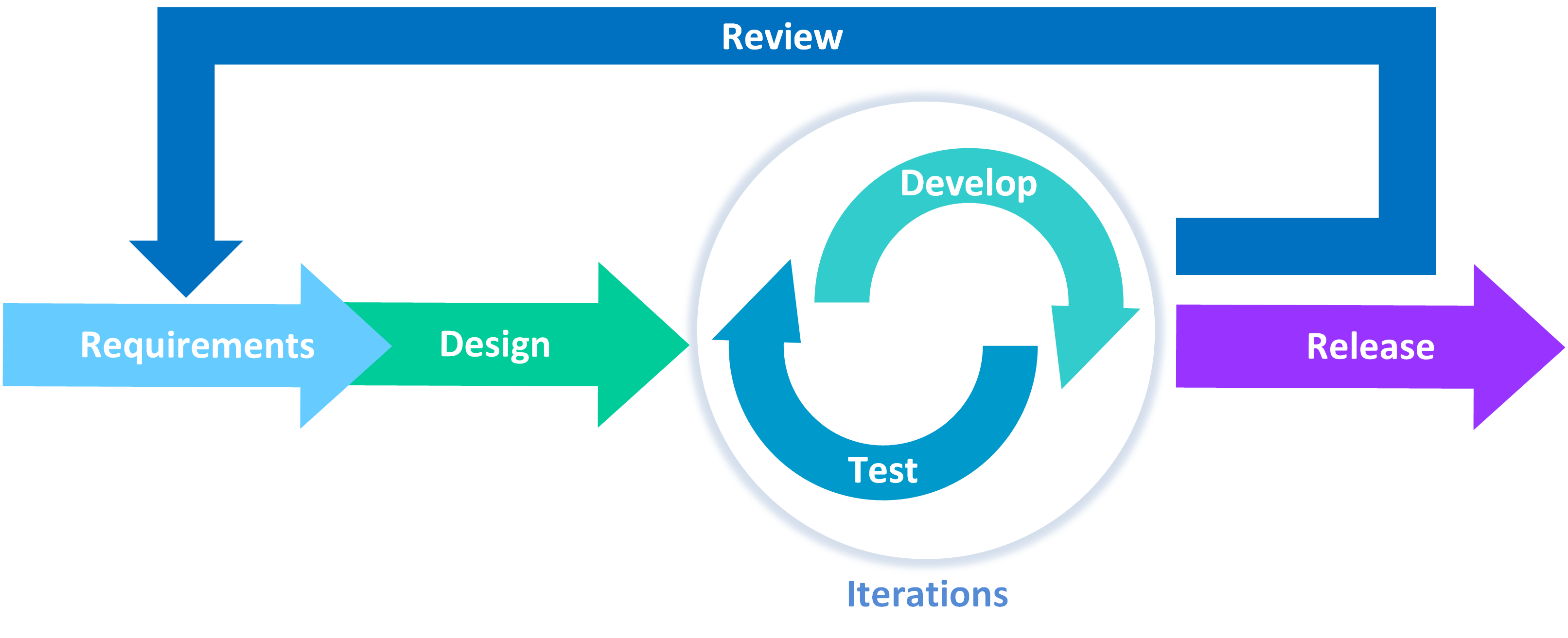
How to Write A Security Pattern Writing Patterns
Further, Our Clinical Capabilities Include Biological, Chemical, Burn, And Radiation Domains.
Web A Security Pattern Is A Solution To A Security Problem, Intended To Control (Stop Or Mitigate) A Specific Type Of Threat By Defining A Security Mechanism, Or A Way To Realize A Security Policy Or Regulation, Applicable In A Given Context (Fernandez 2013;
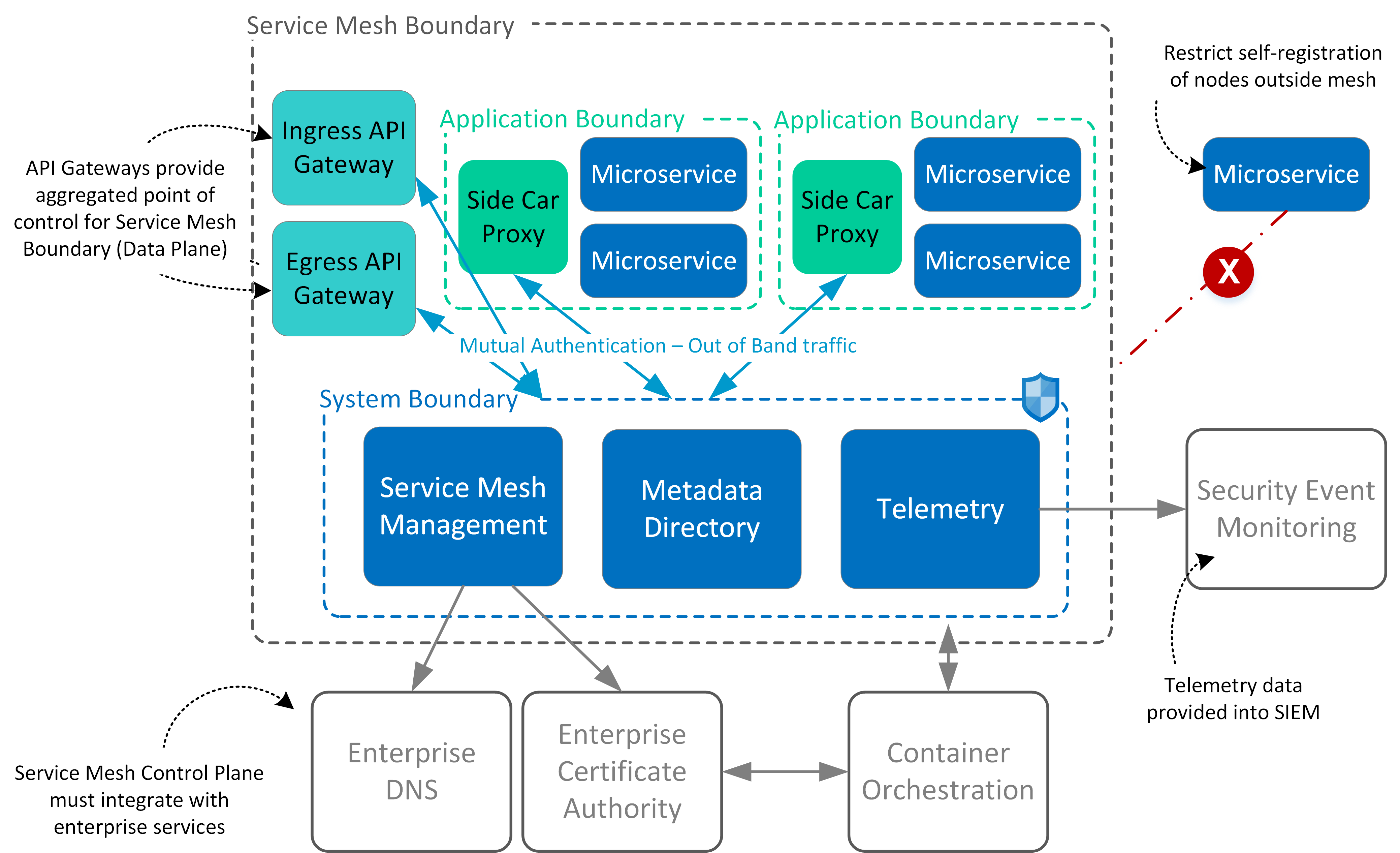
The Guard Checks Inside The Policy Whether The Context Of This User And The Rules Match And Provides Or Denies Access To The Resource.
Web The Policy Pattern Is An Architecture To Decouple The Policy From The Normal Resource Code.
Related Post: