Ransomware Policy Template
Ransomware Policy Template - Web these pillars define a cybersecurity program’s defensive architecture and arsenal, available assets, and policies and procedures that together inform critical. Medusa is demanding $2 million in. The authoring organizations strongly recommend responding by using the. Web rapid7 has observed an ongoing campaign to distribute trojanized installers for winscp and putty via malicious ads on commonly used search engines, where. This service assesses an organization’s ability to counteract a ransomware infection and its spread, but also to resume operations in case of an infection. 204 lines (165 loc) · 15.4 kb. To serve as a ransomware incident response guide. Use security products or services that block access to known ransomware sites on the internet. Web this is the first time proofpoint researchers have observed samples of lockbit black ransomware (aka lockbit 3.0) being delivered via phorphiex in such high. Ransomware is a type of malicious. Quick steps you can take now. Web the ransomware profile aligns organizations’ ransomware prevention and mitigation requirements, objectives, risk appetite, and resources with the elements of the nist. To run on computers, thus preventing. 204 lines (165 loc) · 15.4 kb. Web ransomware is a form of malware designed to encrypt files on a device, rendering any files and the. Web what is a ransomware incident response (ir) playbook? Medusa is demanding $2 million in. We recommend that you simplify. Web first, let’s define ransomware. With the threat of ransomware growing, this “quick start guide” will help organizations use the national institute of standards and technology. Web keep all computers fully patched. The authoring organizations strongly recommend responding by using the. Web what is a ransomware incident response (ir) playbook? To serve as a ransomware incident response guide. Web quick start guide. Identify page 2 nist function: Web boyden (unconfirmed) ransomware gang medusa on may 6 claimed an attack against boyden, an international headhunting firm. Ransomware is a type of malicious. Medusa is demanding $2 million in. Web the policy should specify the parameters to be considered, including the cost of the ransom vs. Web what is a ransomware incident response (ir) playbook? Web first, let’s define ransomware. We recommend that you simplify. Identify page 2 nist function: Ransomware prevention best practices part 2: Web instructions and templates to help you create your own policies and incident response plan to prepare for, respond to, and recover from a ransomware attack. The authoring organizations strongly recommend responding by using the. Tips to help your company protect against ransomware attacks. Sign up for free at. Ransomware is a type of malicious. Web this ransomware guide includes two resources: We recommend that you simplify. 204 lines (165 loc) · 15.4 kb. Department of the treasury announced a set of actions designed to counter ransomware, principally by discouraging. Web quick start guide. Essential steps for your cybersecurity strategy | subrosa. Web instructions and templates to help you create your own policies and incident response plan to prepare for, respond to, and recover from a ransomware attack. Department of the treasury announced a set of actions designed to counter ransomware, principally by discouraging. Web what is a ransomware incident response (ir) playbook? Web. Web instructions and templates to help you create your own policies and incident response plan to prepare for, respond to, and recover from a ransomware attack. Web rapid7 has observed an ongoing campaign to distribute trojanized installers for winscp and putty via malicious ads on commonly used search engines, where. Web creating a robust ransomware policy template: Sign up for. Web creating a robust ransomware policy template: Web the guidance contains a range of internal and external considerations and offers sample questions to leverage at each stage of the procurement process. The estimated cost of restoration, the likelihood of successful restoration. To run on computers, thus preventing. Use security products or services that block access to known ransomware sites on. Web this ransomware guide includes two resources: Ransomware prevention best practices part 2: Web instructions and templates to help you create your own policies and incident response plan to prepare for, respond to, and recover from a ransomware attack. To serve as a ransomware incident response guide. Download our free ransomware response playbook now. Web first, let’s define ransomware. Web boyden (unconfirmed) ransomware gang medusa on may 6 claimed an attack against boyden, an international headhunting firm. Advice from erp expertsfeaturing leading vendorsunbiased software advice Web the ransomware profile aligns organizations’ ransomware prevention and mitigation requirements, objectives, risk appetite, and resources with the elements of the nist. Web looking ahead, ai will be at the forefront of panoptica’s new features and capabilities, ensuring that customers’ growing application security needs are met,. Web on september 21, 2021, the u.s. Web quick start guide. View the full list of policy templates. With the threat of ransomware growing, this “quick start guide” will help organizations use the national institute of standards and technology. Use security products or services that block access to known ransomware sites on the internet. Identify page 2 nist function: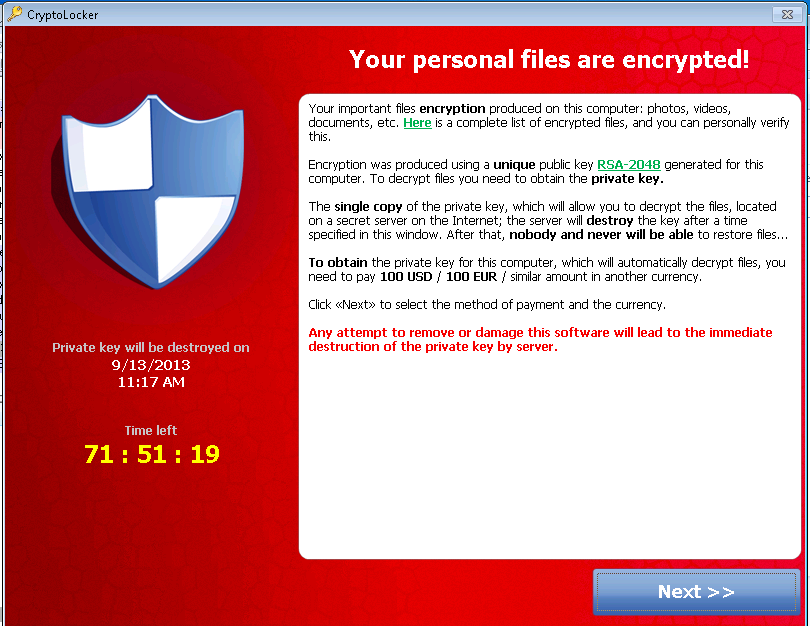
ransomwareexample Cyber Insurance Australia

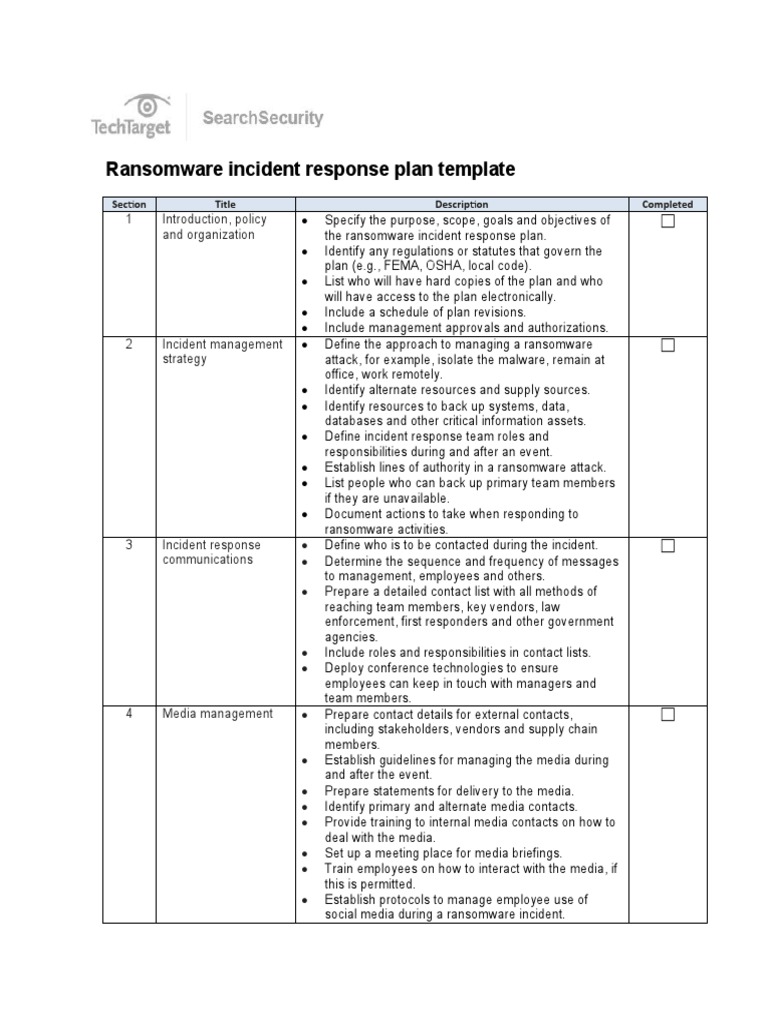
Ransomware Incident Response Plan Template

Ransomware Response Plan Template
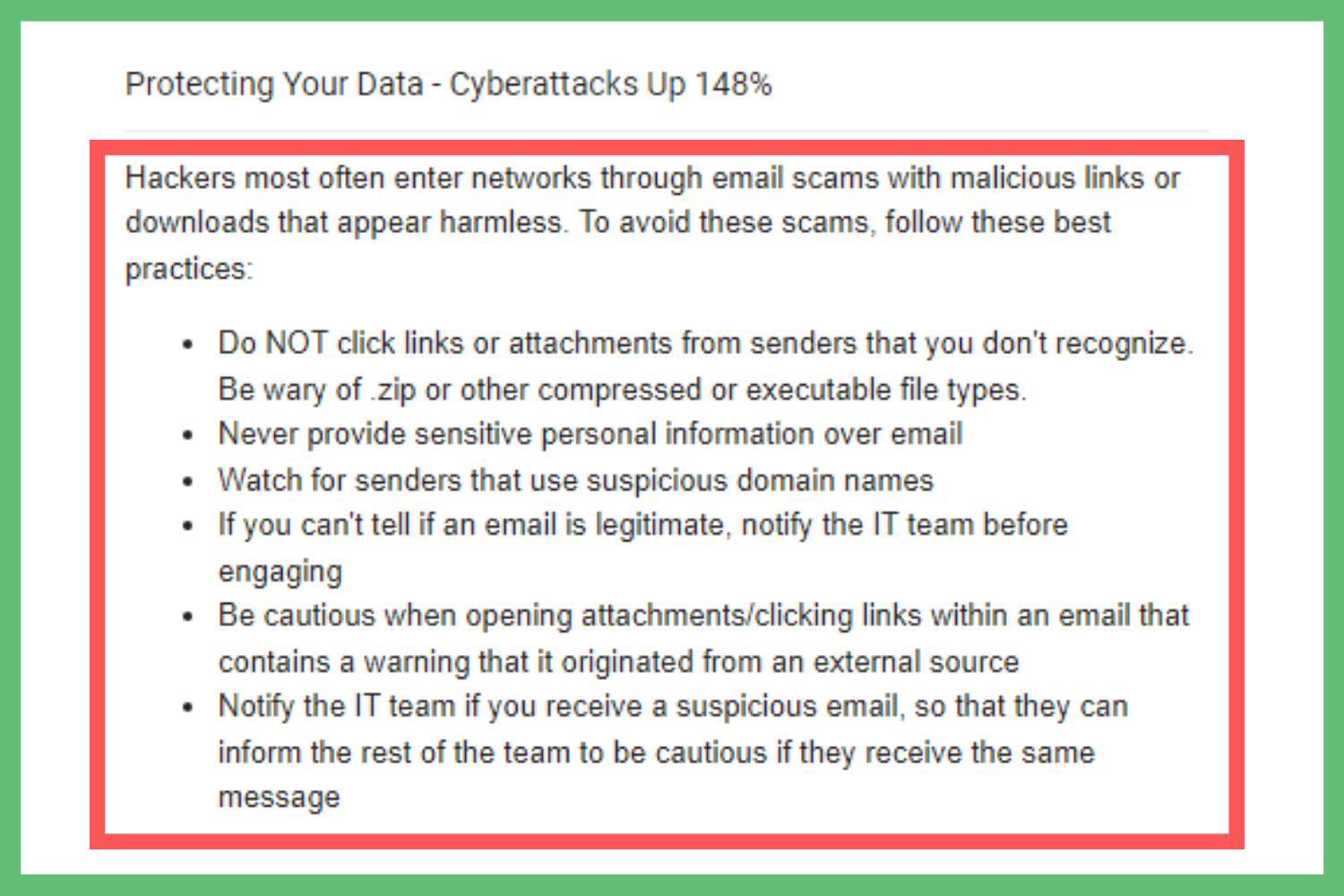
6 Effective Examples of Ransomware Awareness Emails — Etactics (2022)
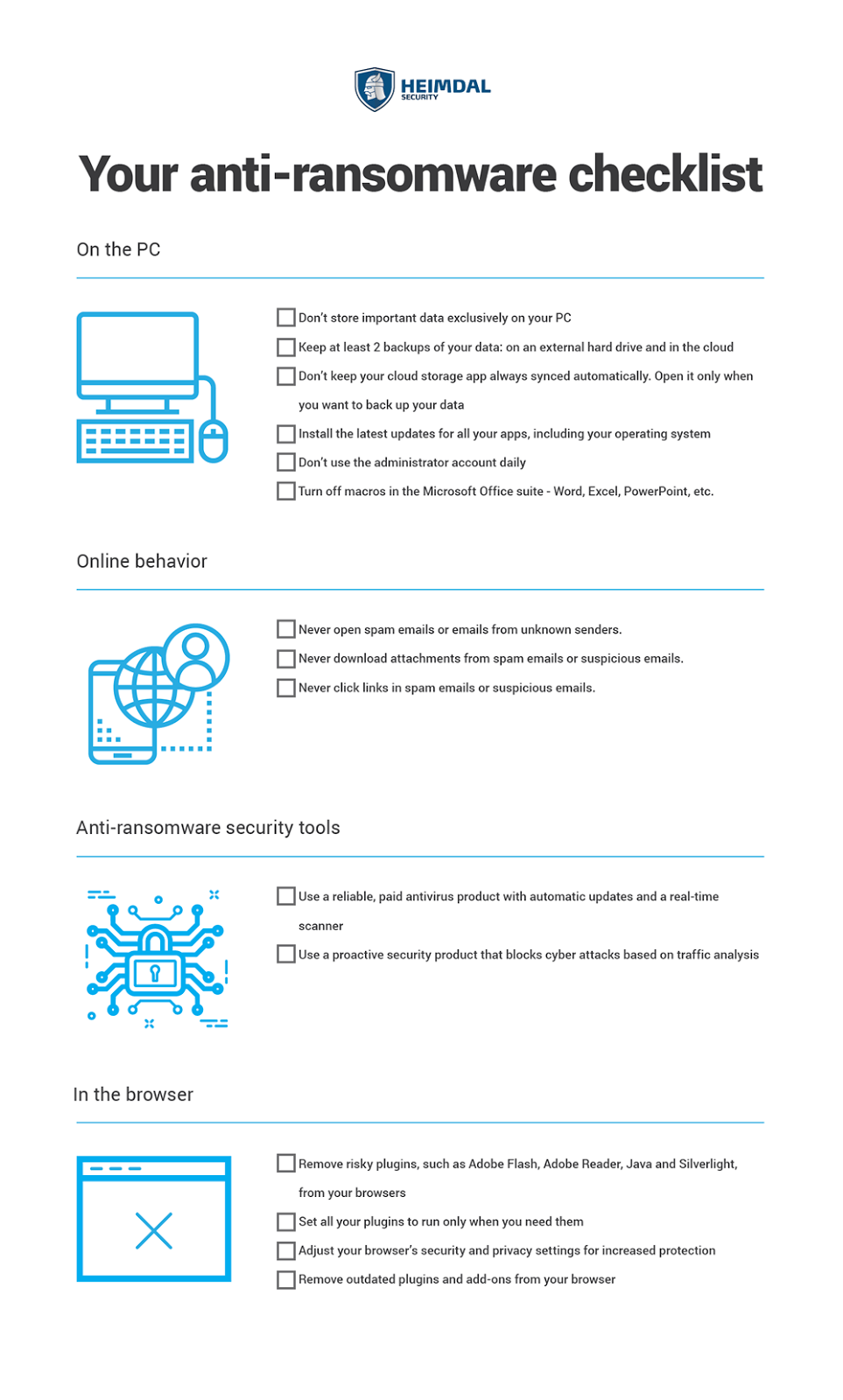
Malware Fighting Quick checklist for ransomware protection

Ransomware Response Plan Template
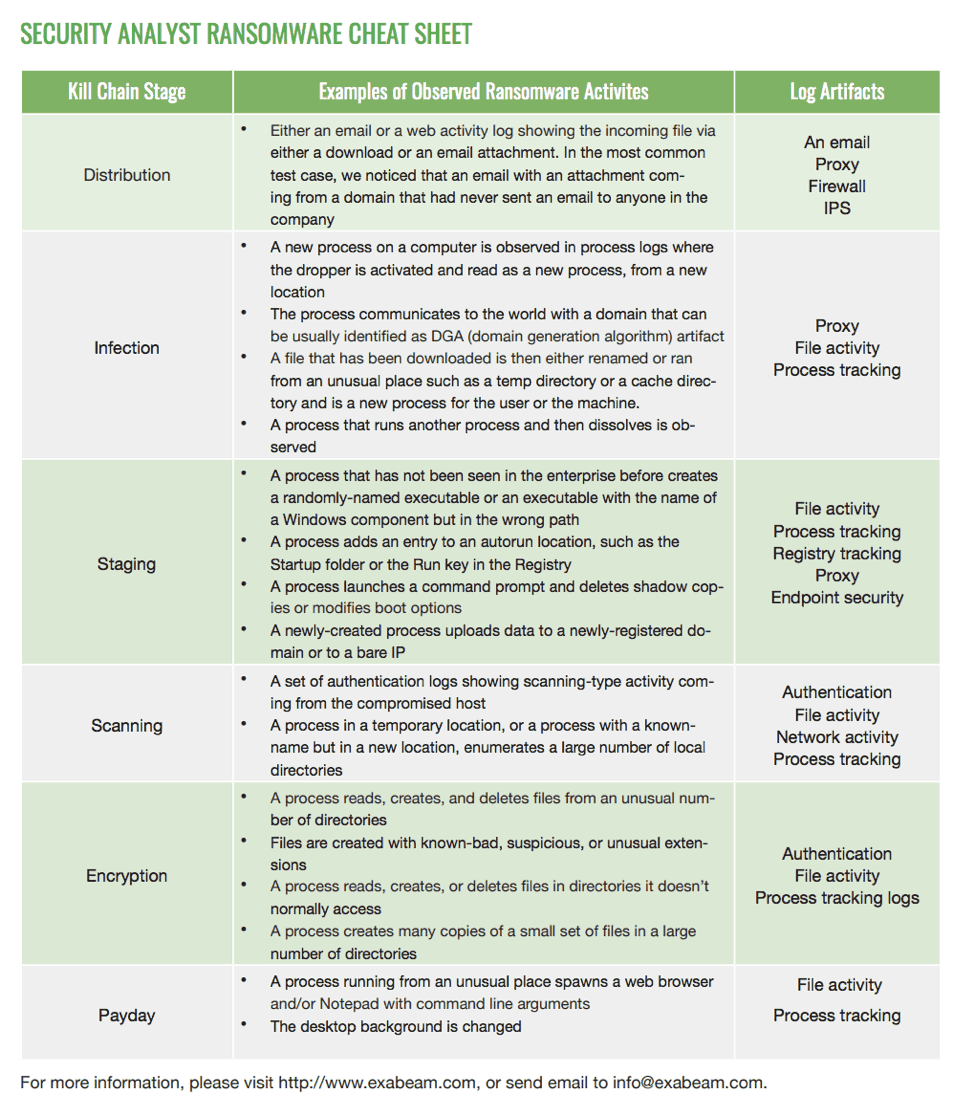
Ransomware Policy Template

Ransomware Policy Template
Ransomware Incident Response Plan Template PDF Ransomware

9step ransomware incident response plan H11 Digital Forensics
Ransomware Is A Type Of Malicious.
To Run On Computers, Thus Preventing.
Web The Policy Should Specify The Parameters To Be Considered, Including The Cost Of The Ransom Vs.
Web These Pillars Define A Cybersecurity Program’s Defensive Architecture And Arsenal, Available Assets, And Policies And Procedures That Together Inform Critical.
Related Post: