Nist Continuous Monitoring Plan Template
Nist Continuous Monitoring Plan Template - The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. § define a continuous monitoring strategy based on risk tolerance that. Web this guideline helps organizations develop and implement a continuous monitoring program for their information systems and security controls. Security continuous monitoring (de.cm) 7 detect: Web this publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act of 2014, 44 u.s.c. Continuous monitoring escalation process guide. It covers topics such as. Anomalies and events (de.ae) 7 detect: Web as defined by nist, the process for continuous monitoring includes the following initiatives: Use these csrc topics to identify and learn more about nist's cybersecurity projects, publications, news, events and. Security continuous monitoring (de.cm) 7 detect: Web this guideline helps organizations develop and implement a continuous monitoring program for their information systems and security controls. It covers topics such as. § define a continuous monitoring strategy based on risk tolerance that. Web this publication provides an example methodology for assessing an organization's information security continuous monitoring (iscm) program, based on. Continuous monitoring escalation process guide. It covers topics such as. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Web created june 08, 2016, updated june 22, 2020. § define a continuous monitoring strategy based on risk tolerance that. Web this guideline helps organizations develop and implement a continuous monitoring program for their information systems and security controls. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitorin information. Maintain ongoing situational awareness about the security and privacy posture of the system and. Continuous. Web this publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act of 2014, 44 u.s.c. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitorin information. Continuous monitoring escalation process guide. Anomalies and events (de.ae) 7. It covers topics such as. Web created june 08, 2016, updated june 22, 2020. Web this publication provides an example methodology for assessing an organization's information security continuous monitoring (iscm) program, based on nist guidance. Detection processes (de.dp) 7 nist. The organization develops a continuous monitoring strategy and implements a continuous monitoring program that includes: § define a continuous monitoring strategy based on risk tolerance that. Detection processes (de.dp) 7 nist. Web this publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act of 2014, 44 u.s.c. Web this publication provides an example methodology for assessing an organization's information security continuous monitoring (iscm) program, based on nist. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitorin information. Security continuous monitoring (de.cm) 7 detect: The purpose. Maintain ongoing situational awareness about the security and privacy posture of the system and. Web this publication provides an example methodology for assessing an organization's information security continuous monitoring (iscm) program, based on nist guidance. Security continuous monitoring (de.cm) 7 detect: Detection processes (de.dp) 7 nist. Continuous monitoring escalation process guide. Web as defined by nist, the process for continuous monitoring includes the following initiatives: Use these csrc topics to identify and learn more about nist's cybersecurity projects, publications, news, events and. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Web this publication has been. The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program. Web as defined by nist, the process for continuous monitoring. Maintain ongoing situational awareness about the security and privacy posture of the system and. Web this publication has been developed by nist to further its statutory responsibilities under the federal information security modernization act of 2014, 44 u.s.c. Security continuous monitoring (de.cm) 7 detect: Web created june 08, 2016, updated june 22, 2020. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring program. Use these csrc topics to identify and learn more about nist's cybersecurity projects, publications, news, events and. It covers topics such as. Web as defined by nist, the process for continuous monitoring includes the following initiatives: The purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitoring. Web the purpose of this guideline is to assist organizations in the development of a continuous monitoring strategy and the implementation of a continuous monitorin information. Web this publication provides an example methodology for assessing an organization's information security continuous monitoring (iscm) program, based on nist guidance. Detection processes (de.dp) 7 nist. Continuous monitoring escalation process guide.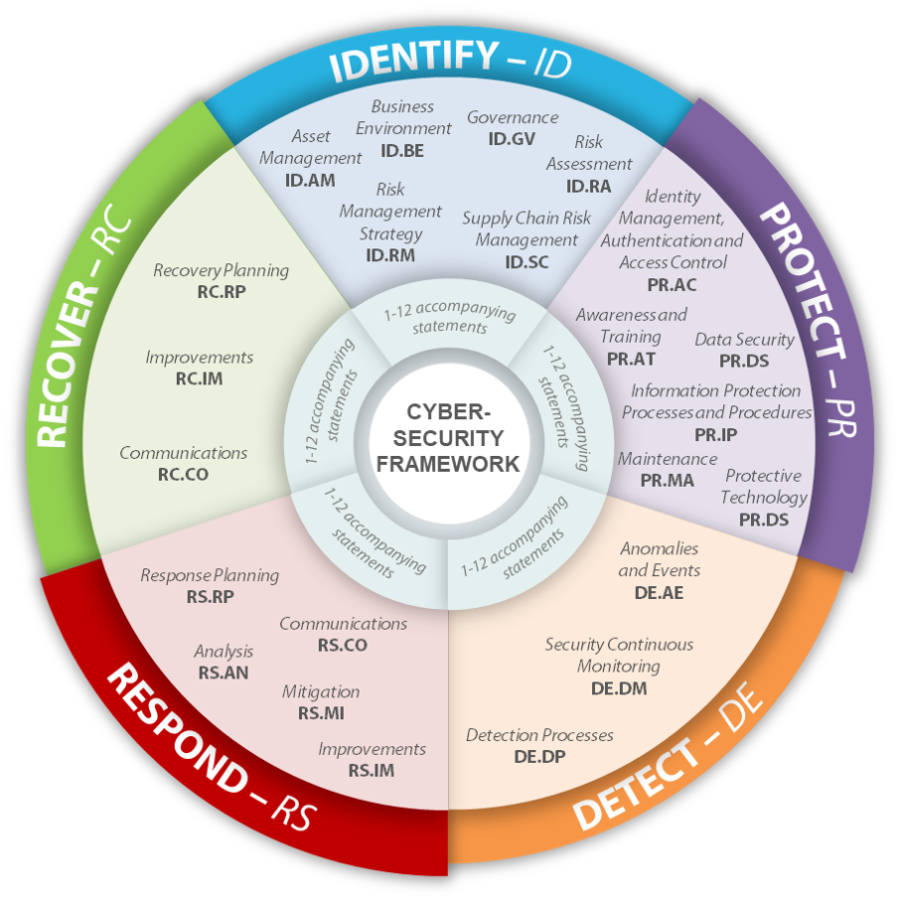
Nist Cybersecurity Framework Template

Implementing the NIST Risk Management Framework TalaTek, LLC
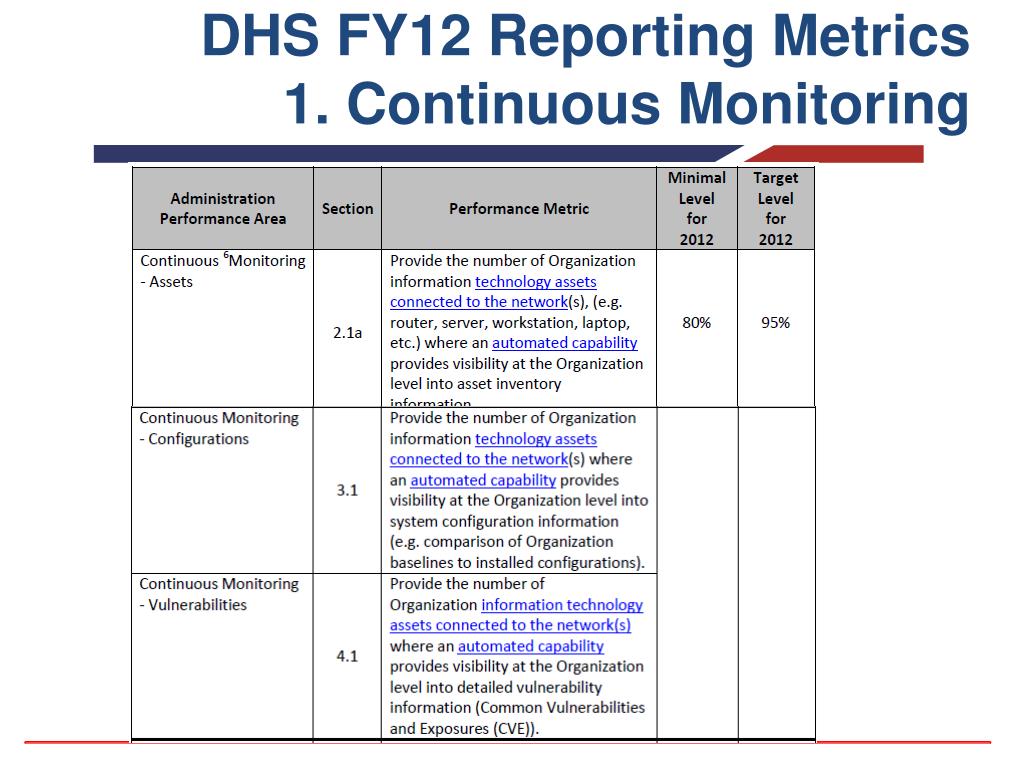
Continuous Monitoring Plan Template

Information Security Continuous Monitoring (ISCM) YouTube

Nist Continuous Monitoring Plan Template
.png?auto=compress,format)
6 Benefits of Continuous Monitoring for Cybersecurity

Rmf Continuous Monitoring Plan Template

Nist Continuous Monitoring Plan Template
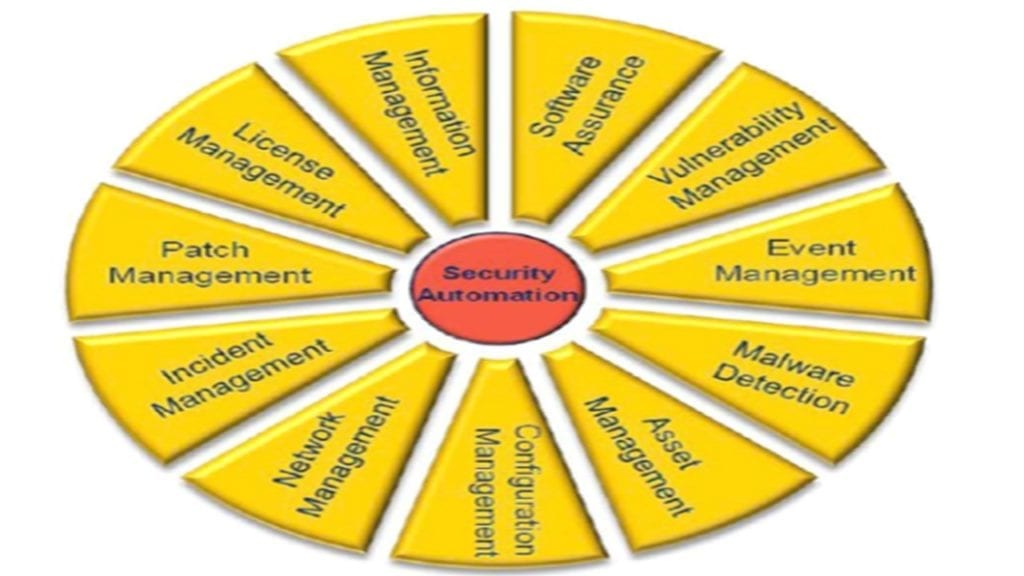
TEMPLATE Continuous Monitoring Plan (ConMon) ⋆ The Cyber Sentinel
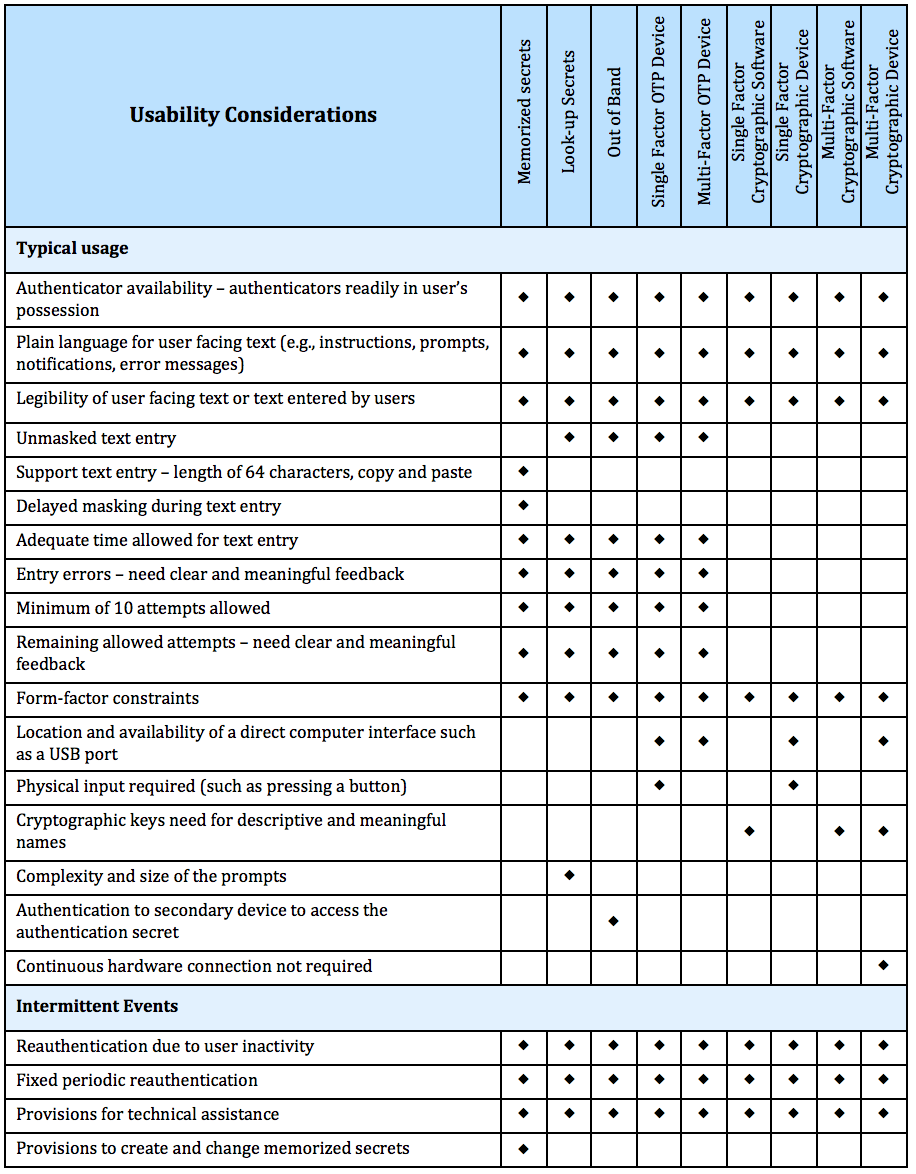
Rmf Continuous Monitoring Plan Template
Web This Guideline Helps Organizations Develop And Implement A Continuous Monitoring Program For Their Information Systems And Security Controls.
The Organization Develops A Continuous Monitoring Strategy And Implements A Continuous Monitoring Program That Includes:
§ Define A Continuous Monitoring Strategy Based On Risk Tolerance That.
Anomalies And Events (De.ae) 7 Detect:
Related Post: