It Security Incident Response Plan Template
It Security Incident Response Plan Template - Relying on his more than 10 years of security and it expertise to understand and devise. In doing so, you have to make sure that its members possess relevant skills and are knowledgeable enough about the undertaking. Incident response planning often includes the following details: The purpose of this template is to help users in meeting the certification requirements for the develop an incident response plan security control area of cybersecure canada. Computer security incident response plan. It includes all the necessary elements for a cybersecurity emergency response plan. One of the benefits of having an incident response capability is that it supports responding to incidents systematically (i.e., following a consistent incident handling methodology) so that the appropriate actions are taken. The primary goal is to minimize damage, reduce recovery time and costs, and mitigate any negative impact on the. Web use this template to list out your primary contacts and make keeping it updated a core component of your incident response plan. Web an incident response plan is a document that outlines an organization’s procedures, steps, and responsibilities of its incident response program. Web an incident response plan is a written document, formally approved by the senior leadership team, that helps your organization before, during, and after a confirmed or suspected security incident. After the remediation efforts conclude, and after a data incident is resolved, reviewing the incident and response to identify key areas for improvement. Web while one basic incident response plan. As such, you must perform a risk assessment and. The roles and responsibilities of each member of the computer security incident response team (csirt) are to be followed efficiently. Web an effective cybersecurity incident response (ir) plan should codify all the steps required to detect and react to cybersecurity incidents, determine the scope and risks, and provide the steps for. Web the (company) incident response plan has been developed to provide direction and focus to the handling of information security incidents that adversely affect (company) information resources.the (company) incident management plan applies to any person or entity charged by the (company) incident response commander with a response to. It is a detailed document outlining the necessary steps to take before,. Web an incident response plan template is a comprehensive checklist of the roles and responsibilities of an incident response team in the event of a security incident. Web it security incident response plan. A lean workflow for fast incident response. Incident response templates, such as the five examples below, supply convenient starting points from which to begin your planning. It. Incident response planning often includes the following details: One of the benefits of having an incident response capability is that it supports responding to incidents systematically (i.e., following a consistent incident handling methodology) so that the appropriate actions are taken. Web the (company) incident response plan has been developed to provide direction and focus to the handling of information security. The purpose of this template is to help users in meeting the certification requirements for the develop an incident response plan security control area of cybersecure canada. After the remediation efforts conclude, and after a data incident is resolved, reviewing the incident and response to identify key areas for improvement. Web knowing you need an insider threat program is the. Web the (company) incident response plan has been developed to provide direction and focus to the handling of information security incidents that adversely affect (company) information resources.the (company) incident management plan applies to any person or entity charged by the (company) incident response commander with a response to. Web an incident response (ir) plan is a document containing a predetermined. Web a cybersecurity incident response plan (csirp) is the guiding light that grounds you during the emotional hurricane that follows a cyberattack.a csirp helps security teams minimize the impact of active cyber threats and outline mitigation strategies to prevent the same types of incidents from happening again. Web 6 template examples of incident response plans. The primary goal is to. These instructions or procedures should help an organization before, during, and after confirmed or suspected security incidents. One of the benefits of having an incident response capability is that it supports responding to incidents systematically (i.e., following a consistent incident handling methodology) so that the appropriate actions are taken. In the event of an outage, a business. Incident response planning. It includes all the necessary elements for a cybersecurity emergency response plan. It involves installing the security solution in software, hardware, and other technologies in the system. In addition to that, the use of a security incident response plan is to identify any threat that they come across and to help figure out a response, as well as to recover. National institute of standards and technology, is a complete guide to incident handling. Gathering key facts about the incident such as root cause and impact, and integrating additional resources as needed to implement necessary fixes as part of remediation. After the remediation efforts conclude, and after a data incident is resolved, reviewing the incident and response to identify key areas for improvement. The purpose of this template is to help users in meeting the certification requirements for the develop an incident response plan security control area of cybersecure canada. This segment is sponsored by graylog. Web an incident response plan is a document that outlines an organization’s procedures, steps, and responsibilities of its incident response program. We developed our incident response playbook to: Web at atlassian, our incident teams are constantly training, refining, testing, and improving our incident management process. These are the typical steps. The primary goal is to minimize damage, reduce recovery time and costs, and mitigate any negative impact on the. Web knowing you need an insider threat program is the first step. It is a detailed document outlining the necessary steps to take before, during, and after an incident to mitigate. The incident response plan template provides a. One of the benefits of having an incident response capability is that it supports responding to incidents systematically (i.e., following a consistent incident handling methodology) so that the appropriate actions are taken. Web a cybersecurity incident response plan usually includes: Web a good cybersecurity incident response plan template is designed to guide an organization through the process of recovering from a cybersecurity incident, such as a data breach, ransomware attack, or system compromise.
Incident Response Plan Template
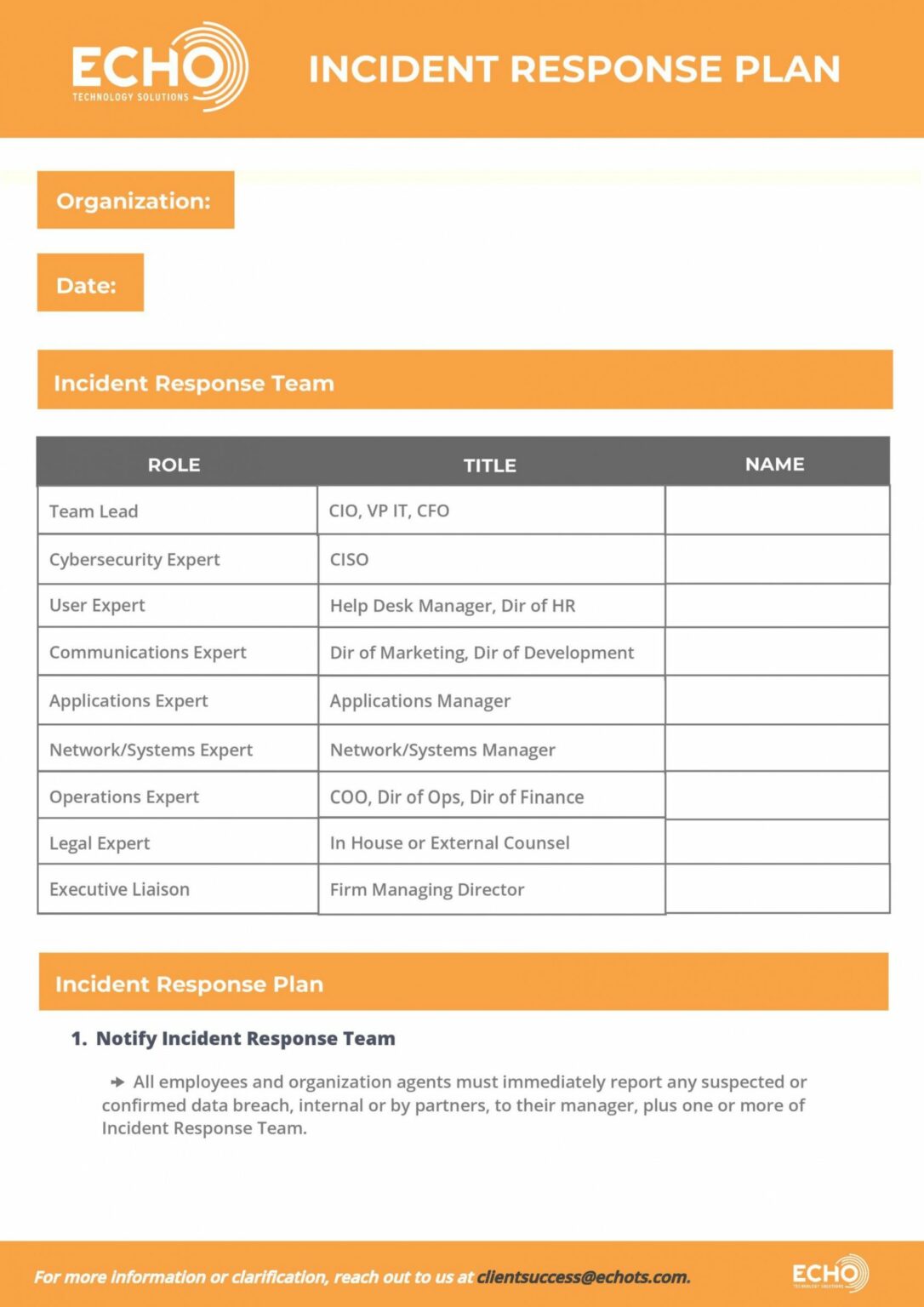
Cybersecurity Incident Report Template

Free Cybersecurity (IT) Incident Report Template PDF Word eForms
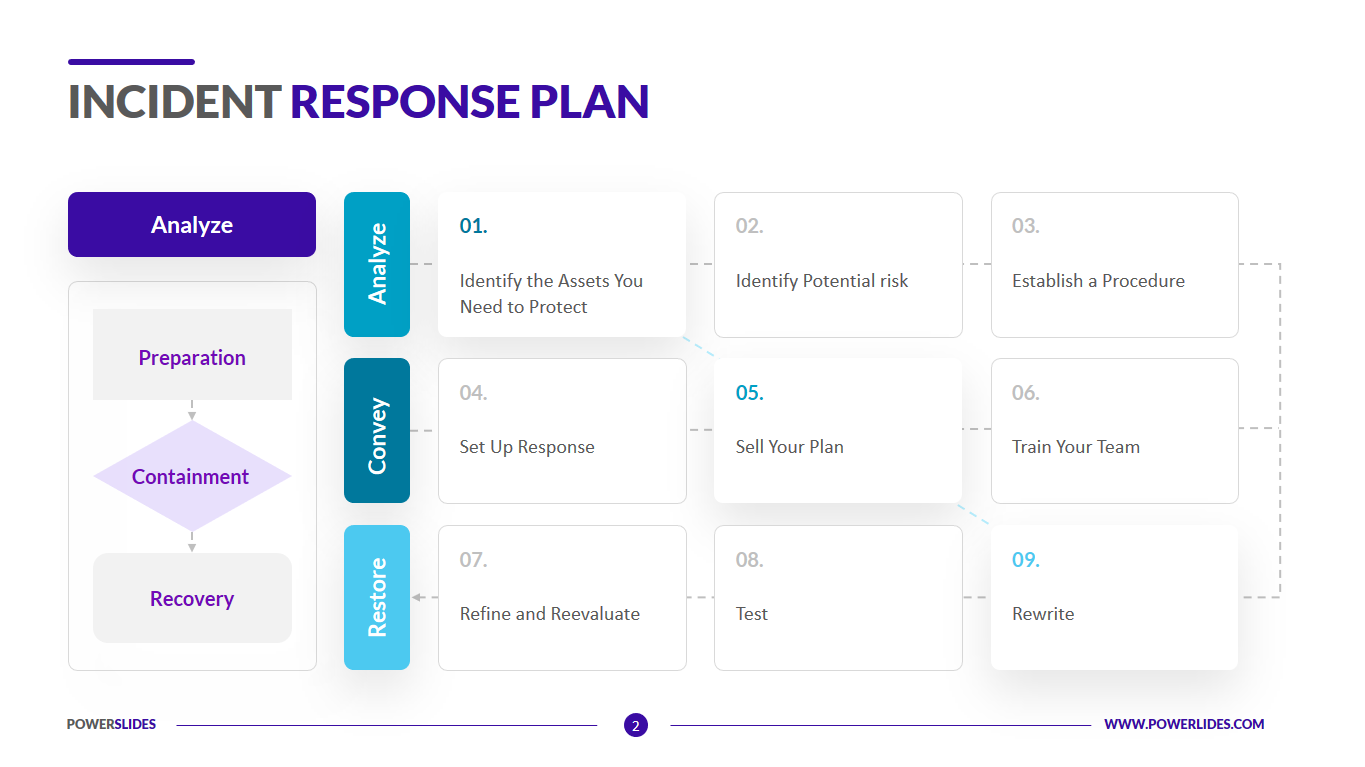
Incident Response Plan Template IT, Security and Data Professionals

What is an incident response plan? Reviewing common IR templates
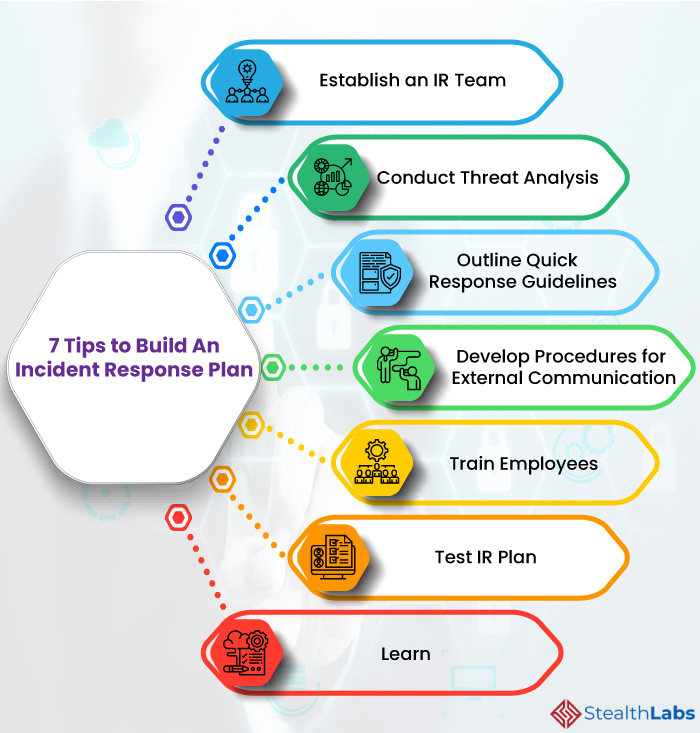
7 Tips to Build an Effective Cyber Incident Response Plan
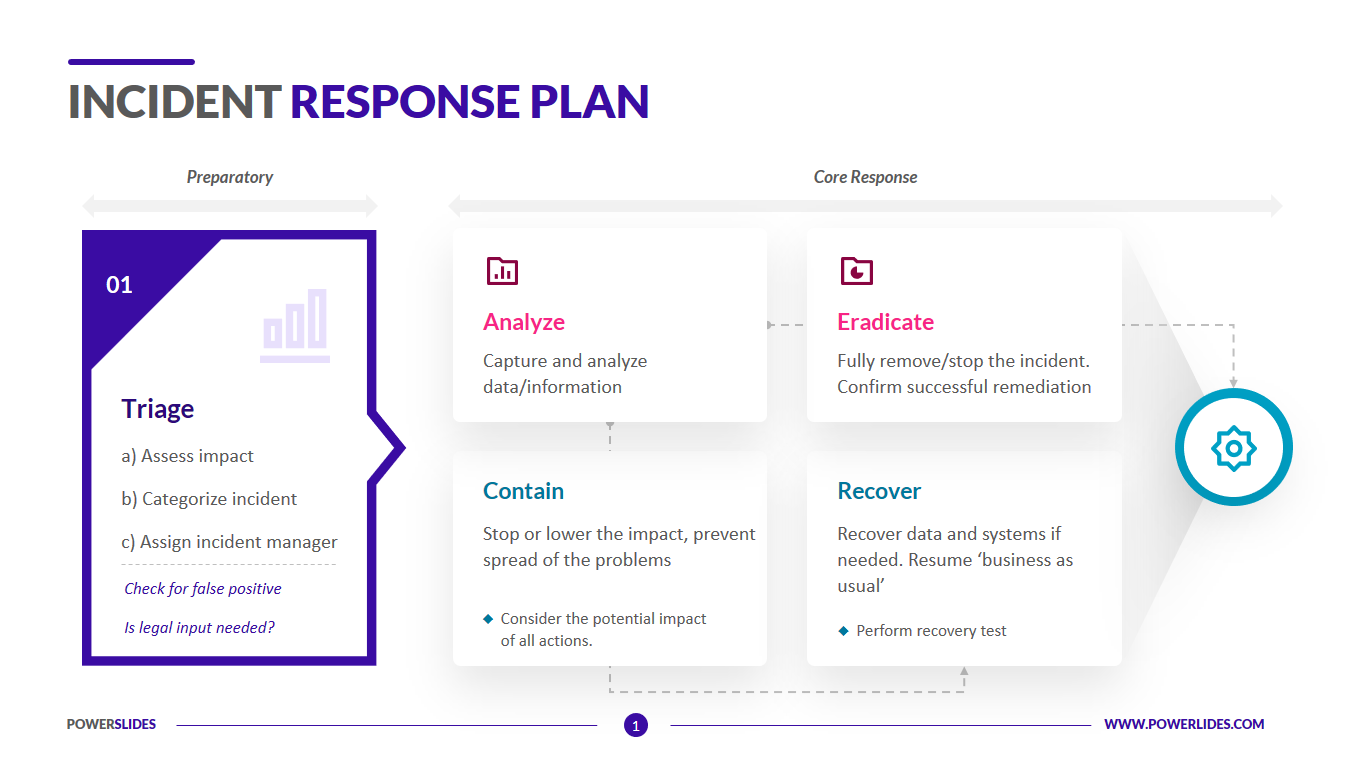
Incident Response Plan Template IT, Security and Data Professionals

How to Create an Incident Response Plan The CPA Journal
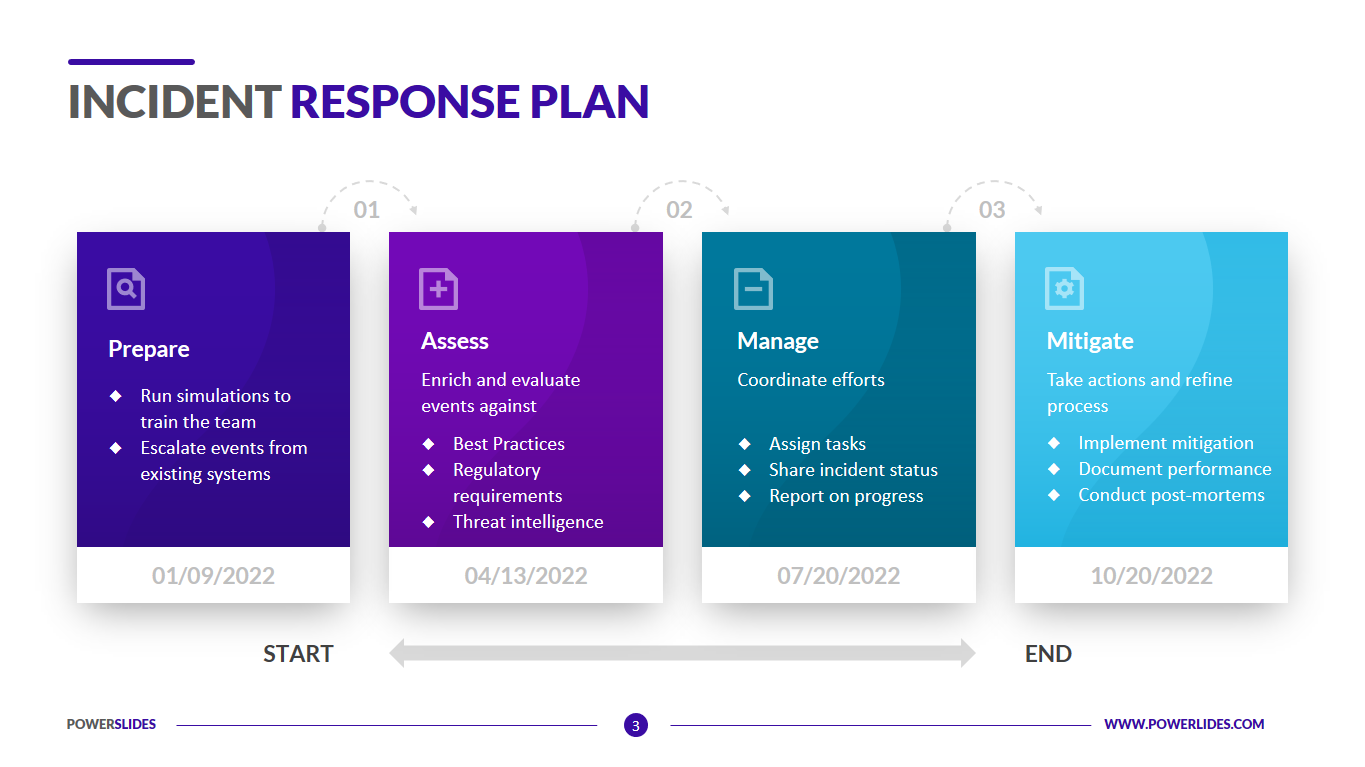
Incident Response Plan Test Template
IT Security Incident Response Plan Template Download in Word, Google
As Such, You Must Perform A Risk Assessment And.
The Roles And Responsibilities Of Each Member Of The Computer Security Incident Response Team (Csirt) Are To Be Followed Efficiently.
Create A Communication Plan, Document Roles, Responsibilities, And Processes, And Recruit Members To The Cyber Incident Response Team (Cirt).
Web An Incident Response (Ir) Plan Is A Document Containing A Predetermined Set Of Instructions Or Procedures To Detect, Respond To, And Limit The Consequences Of A Security Incident.
Related Post: