Insecure Template
Insecure Template - Web cloud code security is critical for businesses that use infrastructure as code (iac) templates to manage their cloud environments. Web the sizes attribute indicates the icon size, while the type contains the mime type of the resource being linked. Cards for playing powerpoint template. This cft is the ‘cfngoat’ template, which is a. Web in this lesson, you will learn what is meant by insecure design and tips on how you can model your programs to protect against flaws in logic. Use this common jar of insecurities template to show what things you are insecure about. Web first, you need to be open and honest. Web insecurity powerpoint templates & google slides themes. A new report shows a. Insecure design is a broad category representing different weaknesses, expressed as “missing or ineffective control design.” insecure design is not the source. Insecure design is a broad category representing different weaknesses, expressed as “missing or ineffective control design.” insecure design is not the source. Someone with a secure attachment style believes they can rely on their. Web insecurity powerpoint templates & google slides themes. Use this common jar of insecurities template to show what things you are insecure about. This blog post. Web insecurity powerpoint templates & google slides themes. Someone with a secure attachment style believes they can rely on their. Use this common jar of insecurities template to show what things you are insecure about. Web search templates provide an easy way to add search functionality backed by an elasticsearch index. Less holding back, less worrying about being judged, and. Feb 05, 2020 5 mins. Web insecure cloudformation template with s3 bucket exposed to the entire internet. This blog post is authored by jon shectman and brian delaney. Web first, you need to be open and honest. A new report shows a. Attachment styles are ways of thinking about and behaving in relationships. A new report shows a. Feb 05, 2020 5 mins. Web insecure cloudformation template with s3 bucket exposed to the entire internet. This cft is the ‘cfngoat’ template, which is a. Web in this lesson, you will learn what is meant by insecure design and tips on how you can model your programs to protect against flaws in logic. Discover 21 insecure designs on dribbble. In this blog article, we’ll examine the. 42% of all cloudformation configuration files contained at least one insecure. Use this common jar of insecurities template to. Web insecure cloudformation template with s3 bucket exposed to the entire internet. These provide useful hints to allow the browser to. Attachment styles are ways of thinking about and behaving in relationships. Throws keystoreexception, nosuchalgorithmexception, keymanagementexception {. Web in this lesson, you will learn what is meant by insecure design and tips on how you can model your programs to. Web in this lesson, you will learn what is meant by insecure design and tips on how you can model your programs to protect against flaws in logic. In the interest of ensuring that there will be a future for hackers, criminals, and others who want to destroy the digital future, this paper captures tips from the masters on. Web. Less holding back, less worrying about being judged, and less beating yourself up. Published feb 26 2020 07:24 pm 35.3k views. 480 px × 480 px. Insecure design is a broad category representing different weaknesses, expressed as “missing or ineffective control design.” insecure design is not the source. 42% of all cloudformation configuration files contained at least one insecure. These provide useful hints to allow the browser to. 42% of all cloudformation configuration files contained at least one insecure. Web in this lesson, you will learn what is meant by insecure design and tips on how you can model your programs to protect against flaws in logic. Web insecure cloudformation template with s3 bucket exposed to the entire internet.. These provide useful hints to allow the browser to. Your resource to discover and connect with designers worldwide. Web cloud code security is critical for businesses that use infrastructure as code (iac) templates to manage their cloud environments. Attachment styles are ways of thinking about and behaving in relationships. Web jar of insecurities meme template. Someone with a secure attachment style believes they can rely on their. Web first, you need to be open and honest. Web however, this automated process means a single insecure iac template could provision hundreds of insecure resources, snowballing to hundreds or thousands. Less holding back, less worrying about being judged, and less beating yourself up. Web the sizes attribute indicates the icon size, while the type contains the mime type of the resource being linked. Web insecure cloudformation template with s3 bucket exposed to the entire internet. This blog post is authored by jon shectman and brian delaney. Web our cloudformation template is (a) in yaml format, (b) a known insecure template, and (c) stored within github. Web insecurity powerpoint templates & google slides themes. These provide useful hints to allow the browser to. Web search templates provide an easy way to add search functionality backed by an elasticsearch index. Here, it’s just you and your journal. Your resource to discover and connect with designers worldwide. Web in this lesson, you will learn what is meant by insecure design and tips on how you can model your programs to protect against flaws in logic. Attachment styles are ways of thinking about and behaving in relationships. A new report shows a.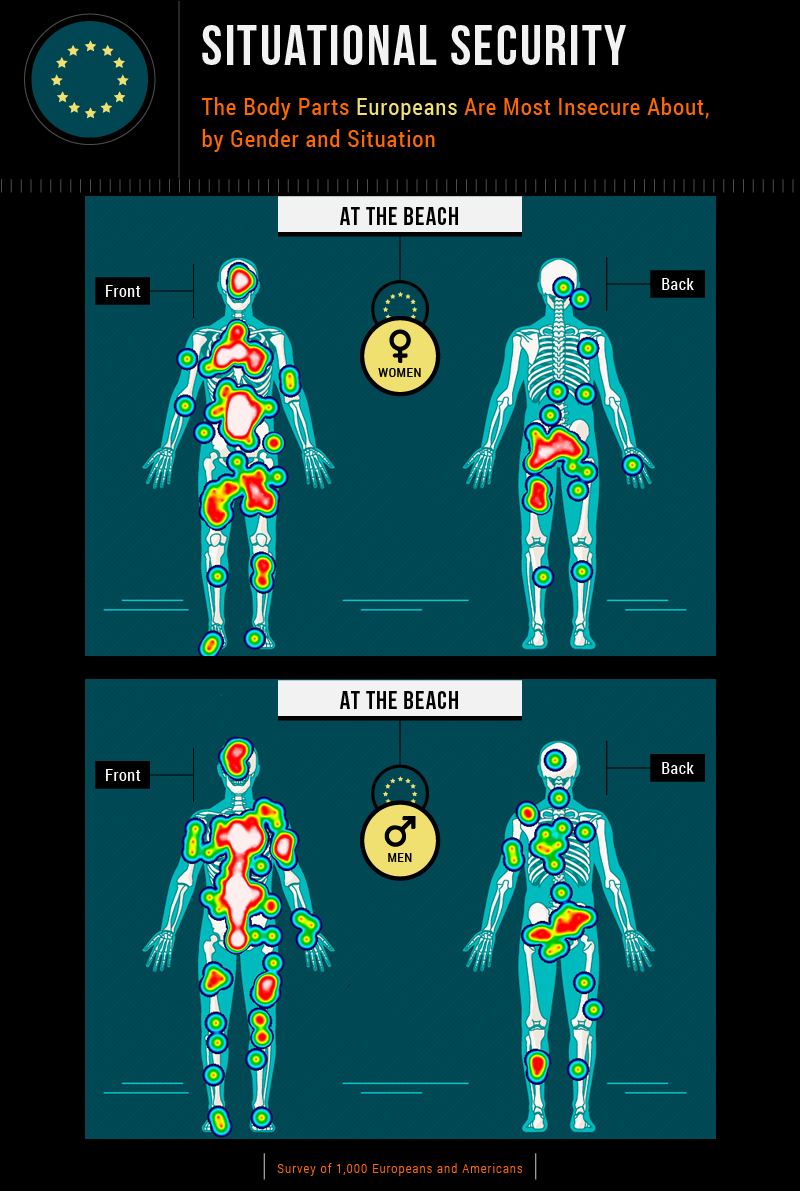
How Insecure Are You Body Template
Insecure Template

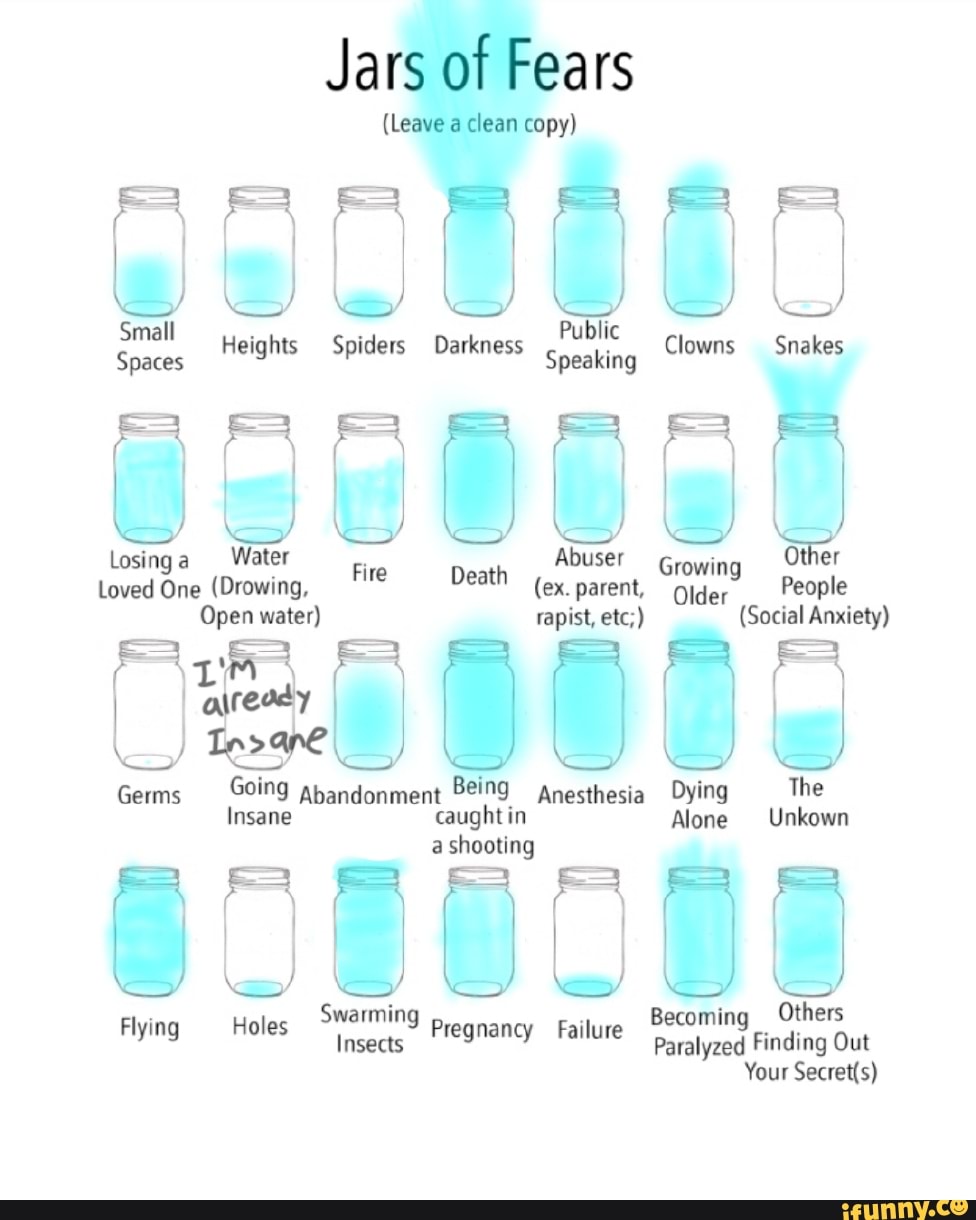
FREE Jars of Insecurities Customizable

How Insecure Are You Template

FREE Jars of Insecurities Customizable

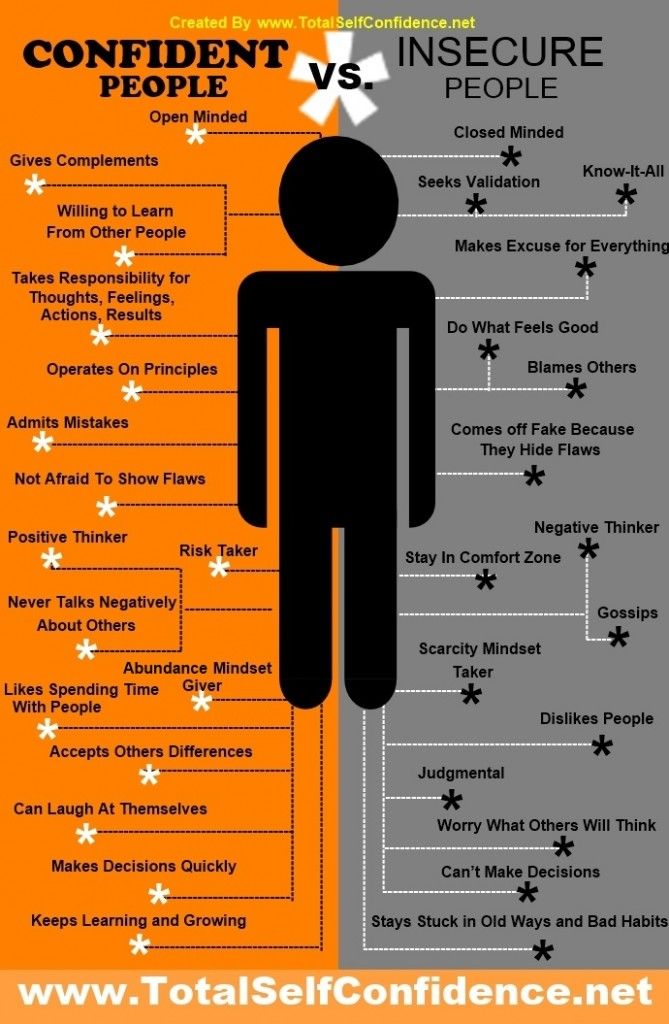
Insecurity Template

Apology Letter Template to Boyfriend Sample & Example

How Insecure Are You Template
Insecure Body Template

Insecure Body Template
Feb 05, 2020 5 Mins.
480 Px × 480 Px.
As Iac Templates Become More.
Insecure Design Is A Broad Category Representing Different Weaknesses, Expressed As “Missing Or Ineffective Control Design.” Insecure Design Is Not The Source.
Related Post: