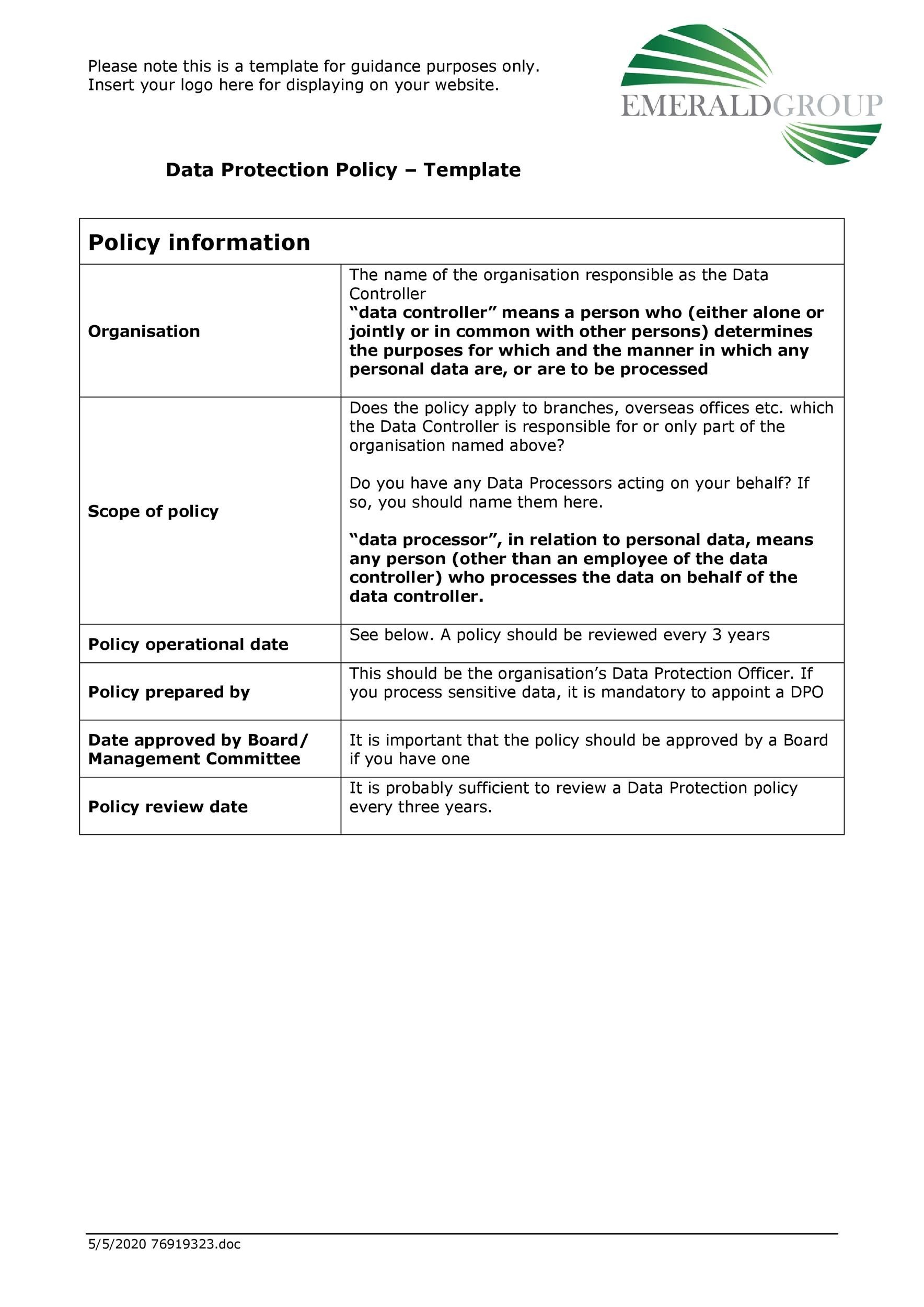
Information Technology Policies And Procedures Templates
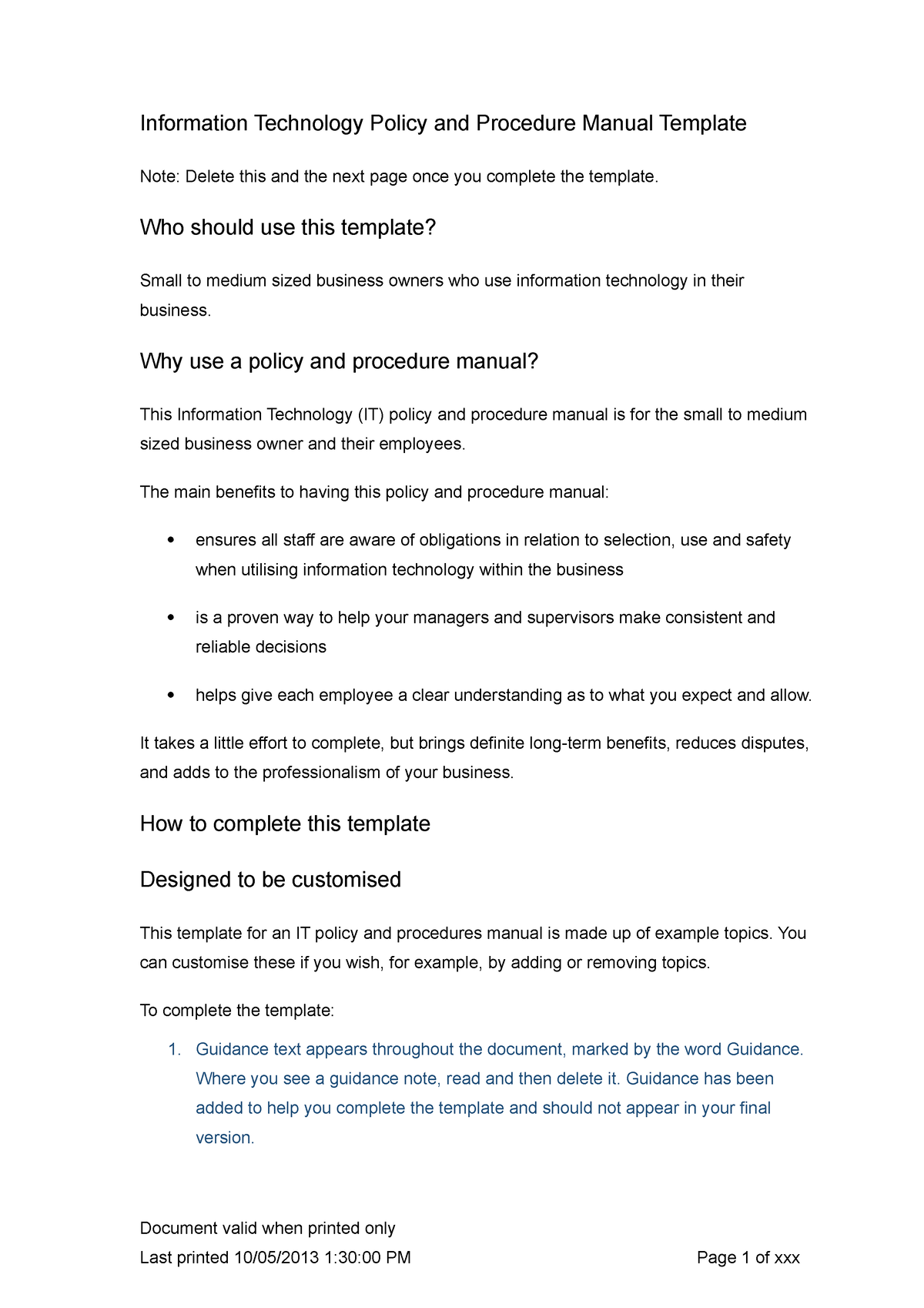
Information Technology Policies And Procedures Templates - Usage policy for device, internet, email, and social media. Create a team to develop the policy. Vita security baseline configurations (hardening standards) business impact analysis policy template. If thou need some tools to help you with one task of building it policies for to own organization, then use the tips. Web information security policy templates. It policies help growing companies protect their technology infrastructure, data, and intellectual property from cyber threats, regulatory. These footstep documents will typically covers your company’s rules also employee guidelines to guarantee that employees deliver services effectively to your clients. These are free to use and fully customizable to your company's it security practices. Explore the information technology policy and procedure templates available on way we do to add to your. An email policy template details clear. Determine whether your grant / funding will aim to advance any sensitive technology research area. Vita security baseline configurations (hardening standards) business impact analysis policy template. Web electronic data disposal policy. Web this template for an it policy and procedures manual is made up of example topics. Transmission of sensitive data policy. With the help of strong policies and procedures, you can incorporate actions that are consistent, effective and efficient. New policy on sensitive technology research and affiliations of concern. Vita security baseline configurations (hardening standards) business impact analysis policy template. This policy provides guidelines for the use of software for all employees within the business to ensure that all software use. If thou need some tools to help you with one task of building it policies for to own organization, then use the tips. Information security incident reporting policy. Web this policy covers defining company’s resources that has something to do with technology, such as the computers, servers, computer networks, communication and mail servers, and other resources that need technology to. Having a manual for your business: Where you see a guidance note, read and then delete it. Our list includes policy templates for acceptable use policy, data breach response policy, password protection policy and more. Every business needs it policies and procedures that incorporate security policies, onboarding new employees and setting up their it requirements to renewing domain names on. Web the following templates are available as a guideline for agencies to develop their it security policies. Your information technology (it) policies and procedures manual is to create a written record of your business's rules and processes for its digital operations, online presence and use of personal or business devices. Emergency response damage assessment procedure template. Define the scope of. An email policy template details clear. Under this policy, the use of all open source and freeware software will be conducted under the same procedures outlined for commercial software. Web purpose of the policy. Every business needs it policies and procedures that incorporate security policies, onboarding new employees and setting up their it requirements to renewing domain names on an. Under this policy, the use of all open source and freeware software will be conducted under the same procedures outlined for commercial software. Our list includes policy templates for acceptable use policy, data breach response policy, password protection policy and more. Web it policies and procedures establish guidelines for the use of information technology within an organization. Web this policy. These guidelines apply to all users and data in an organization, preventing any security incidents from occurring. Our list includes policy templates for acceptable use policy, data breach response policy, password protection policy and more. Web information & cyber security policy templates. Learn how to manage technology assets, respond to security incidents, and ensure business continuity. Web according to job. In other words, it outlines what everyone is expected to do while using company assets. Web information & cyber security policy templates. A practical and effective method to plan, implement and review it controls in the context of your business strategy. Usage policy for device, internet, email, and social media. Web electronic data disposal policy. Emergency response employee communications procedure template. Learn how to manage technology assets, respond to security incidents, and ensure business continuity. Schedule management briefings during the writing cycle to ensure relevant issues are addressed. The acceptable use policy should cover these important areas: The info~tech research group defines other policies that it organizations need to put in place. The acceptable use policy should cover these important areas: A practical and effective method to plan, implement and review it controls in the context of your business strategy. Web sample information technology policy procedure template. Web adapt existing security policies to maintain policy structure and format, and incorporate relevant components to address information security. Web information & cyber security policy templates. Web policies, standards and procedures. Vita security baseline configurations (hardening standards) business impact analysis policy template. Under this policy, the use of all open source and freeware software will be conducted under the same procedures outlined for commercial software. In other words, it outlines what everyone is expected to do while using company assets. Get our 5 tips for success plus free templates to get started. Determine whether your grant / funding will aim to advance any sensitive technology research area. These footstep documents will typically covers your company’s rules also employee guidelines to guarantee that employees deliver services effectively to your clients. Every business needs it policies and procedures that incorporate security policies, onboarding new employees and setting up their it requirements to renewing domain names on an annual basis. Guidance text appears throughout the document, marked by the word guidance. Define the components of the it policy: Adds to your business's professionalism.
Information Technology Policy Template
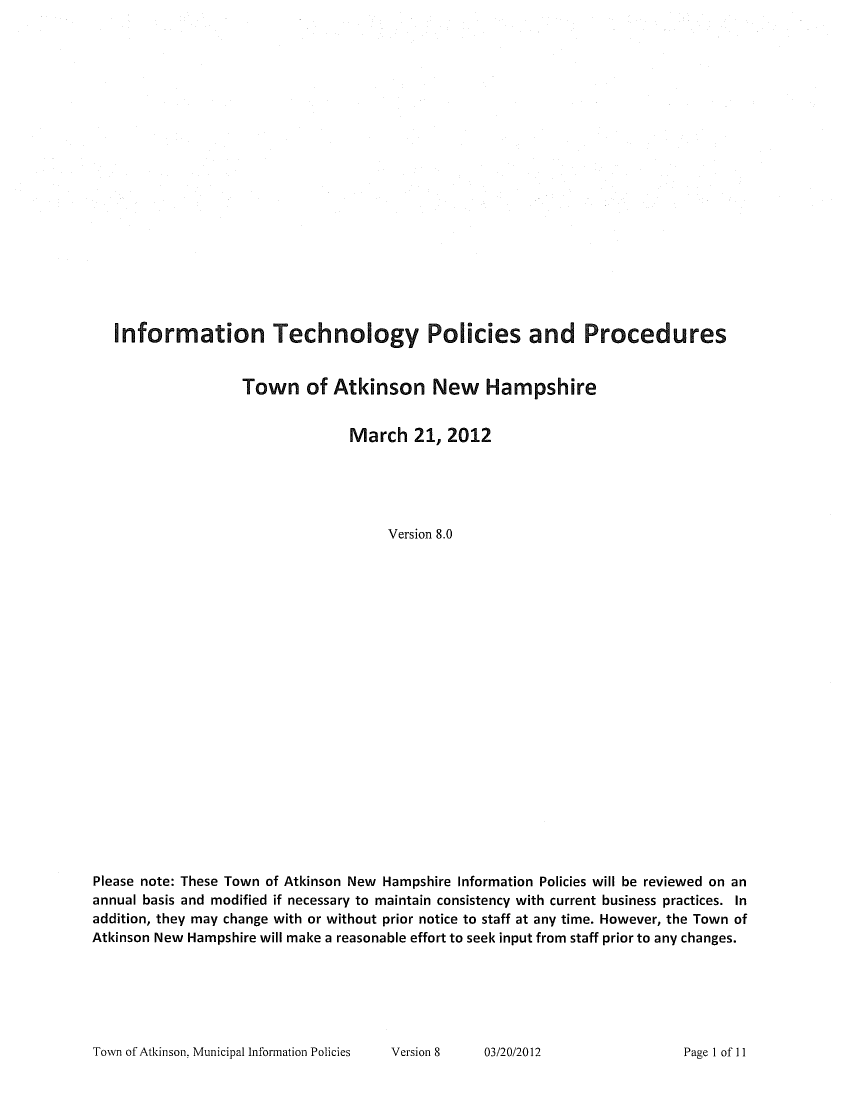
Examples of IT PoliciesProcedures Format, Sample Examples
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](http://templatelab.com/wp-content/uploads/2018/05/Security-Policy-22.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
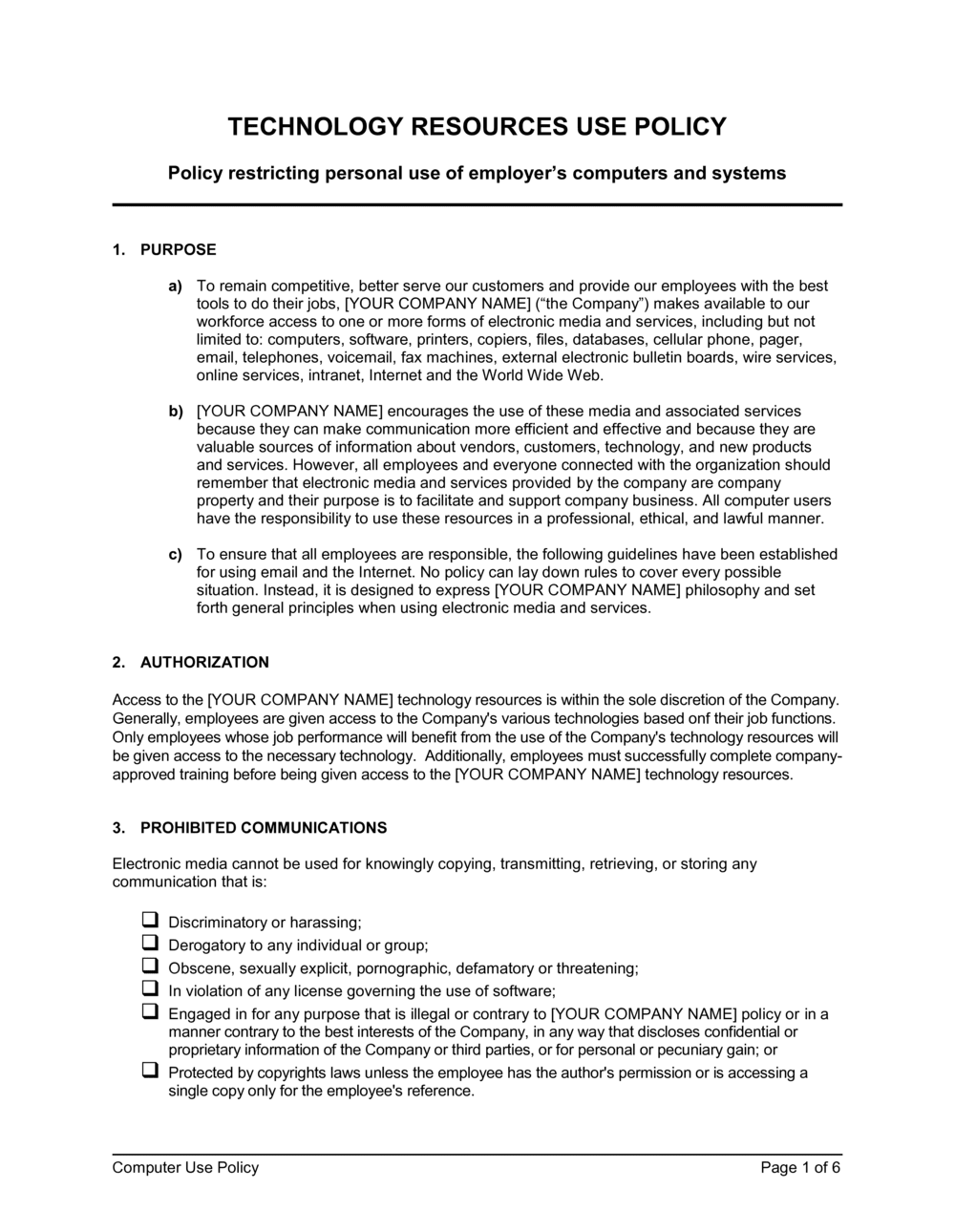
Computer Usage Policy Template
![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-10.jpg)
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
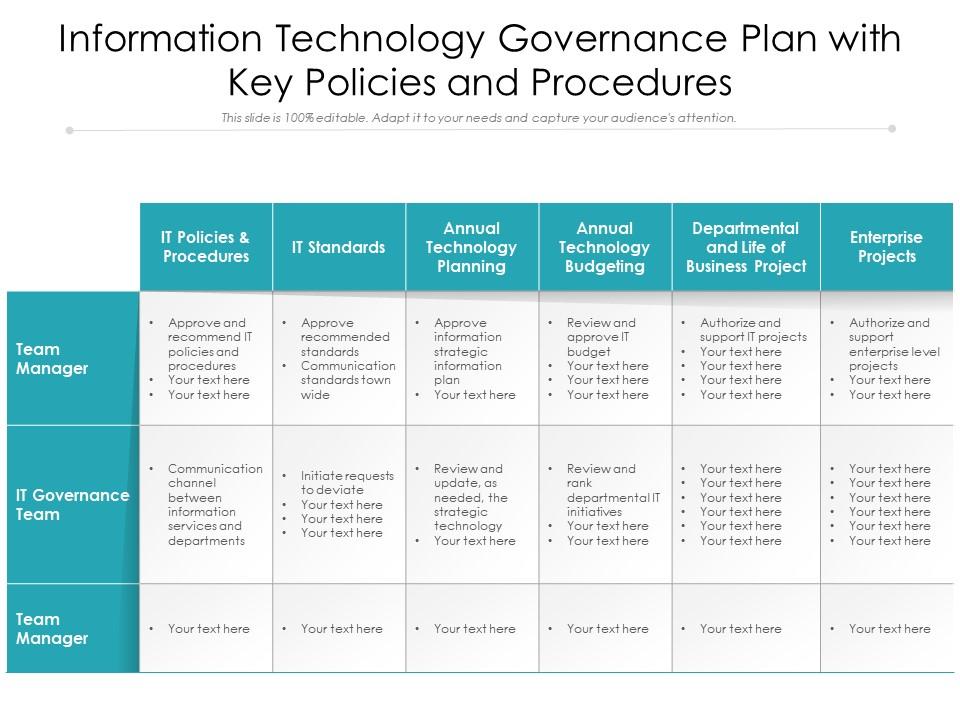
Information Technology Governance Plan With Key Policies And Procedures
IT Policies and Procedures Manual IT Standard Operating Procedures

How to Write Policies and Procedures Smartsheet (2022)
Free Cyber Security Policy Template Master of Documents
IT policies and procedures manual template Information Technology
Define The Scope Of The Policy.
New Policy On Sensitive Technology Research And Affiliations Of Concern.
Get Ahead Of Your 2023 Security Goals.
Web Information Security Policy Templates.
Related Post: